The UIWIX ransomware virus is a newly discovered malware that assigns a unique machine id to each infected host. It encrypts user data and is able to cause a lot of system issues to the target computers. All affected data is renamed with the “._
DOWNLOAD UIWIX Virus Removal Tool
Once UIWIX is removed successfully, you can try to restore your files following our instructions below.
UIWIX Ransomware Virus Description
The UIWIX ransomware virus is one of the newest discovered threats. During the initial security analysis the researchers were not able to find a connection with any of the famous malware families. This means that the virus is probably made from scratch by the hacker(s) behind it. At the moment the identity of the creators is not known. Like other similar threats it features an encryption engine that processes user data when the infection is triggered.
The UIWIX ransomware virus uses a predefined list of target file type extensions. Depending on the configuration and targets the hackers can customize it. However in the most popular scenario it targets many of the file types used by the computers: archives, music, photos, videos, databases, configuration files and etc. At the moment the security analysis is still ongoing. It is similar to other basic viruses like the MOTD ransomware. It is very probable that the current version of the UIWIX ransomware virus is an early testing iteration. We expect to see future updates that can include additional functionality such as the following:
- Spying– Updated UIWIX ransomware virus strains can harvest sentsitive information from the victim computers. The institution of keyloggers can also be used to gain the data sets.
- Additional Payload Delivery – The UIWIX ransomware virus is able to install other threats to the infected computers.
- Remote Control – Advanced viruses can install Trojan components on the infected hosts. This means that it is possible for an updated version of the UIWIX ransomware virus to help the hackers control the computers at will.
When the encryption process is complete the ._
ALL YOUR PERSONAL FILES ARE DECODED
Your personal code: [id]
To decrypt your files, you need to buy special software.
Do not attempt to decode or modify files, it may be broken.
To restore data, follow the instructions!You can learn more at this site:
https://4ujngbdqqm6t2c53.onion.to
https://4ujngbdqqm6t2c53.onion.cab
https://4ujngbdqqm6t2c53.onion.nuIf a resource is unavailable for a long time to install and use the tor browser.
After you start the Tor browser you need to open this link http://4ujngbdqqm6t2c53.onion
The instructions show the victims how to acess the payment gateway used by the UIWIX ransomware virus.
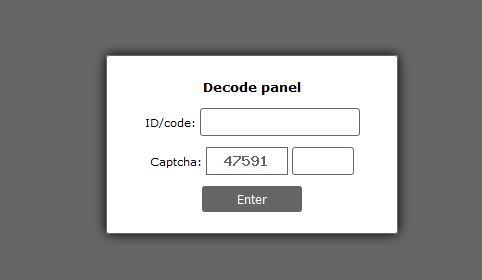
Other recent virus samples that use a similar setup include threats like the NM4 ransomware. When the users visit it they are shown a login page which requests the personal the unique machine infection ID. After it is entered the site displays the complete UIWIX ransomware virus note:
TO get the program to decrypt Use You need to pay: 0.12261 BTC (~200$)
How to pay?
1. You should click here to find out how to sign up for a Bitcoin wallet.
2. Buying Bitcoin is getting simpler every day, See the below for ways to buy Bitcoin:
coincafe.com – Recommended for fast, simple service. Payment methods: Western union, Bank of America, Cash by FedEx,Moneygram, Money Order
btcdirect.eu – The best place for Europe
other – Or any other convenient for you service
3. Send 0.12261 BTC to Bitcoin address: 174cykEkQpskcvCopjP3C6PzCeWPRmnjHi2
4. Ensure your payment information and then Click ‘Check Payment’
Check Payment
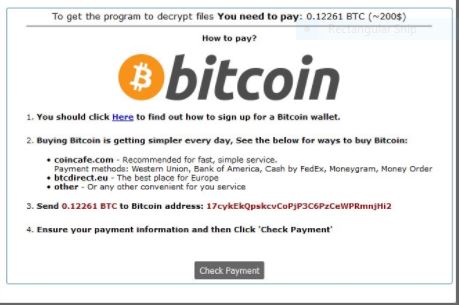
From this we can conclude several facts about the UIWIX ransomware virus:
Use of the Tor Anonymous Network – The hackers use the TOR anonymous network to display the ransomware note and operate their infrastructure. This signals that they can probably use other hidden services in future versions as well.
Fixed Ransomware Sum – The hackers behind the UIWIX ransomware virus have specified a ransomware sum that is extorted from the victims. It totals 0.12261 Bitcoins which is the equivalent of about 215 US Dollars.
Template Use – The hackers have copied the ransomware note template from other similar viruses such as the .Crypted File Virus (Dxh26wam Ransomware).
Machine ID Renaming Scheme – The UIWIX ransomware virus renames the affected files with the ._
UIWIX Ransomware Virus Distribution
The limited number of collected UIWIX ransomware virus shows that the hackers have not picked up a single infection strategy. As such different spread methods can be used. Some of the popular ones include the following:
Email Spam – Computer criminals can create and coordinate mass email campaigns that carry the UIWIX ransomware virus. These strategies include various social engineering tricks that attempt to make the targets infect themselves with the malware. The UIWIX ransomware virus is usually either attached directly as an executable file or linked in the body contents.
Direct Hacker Attacks – Another way of spreading the UIWIX ransomware virus is by launching automated vulnerability testing attacks. The targets can protect themselves by always running the latest softwaare on their computers.
Browser Hijackers – Malicious web browser extensions can be used to trigger an infection. They are also known as browser hijackers and are usually made for the most popular applications: Mozilla Firefox, Safari, Internet Explorer, Microsoft Edge and Google Chrome. Upon infection they modify them to point to a hacker-specified site by changing the default home page, default search engine and new tabs page. In addition they actively harvest and transmit sensitive information harvested from the browsers such as: stored account credentials, cookies, bookmarks, history, form data and etc.
Hacker-controlled Sites – The criminals can spread copies of the UIWIX ransomware virus on counterfeit download sites and portals. They usually pose as legitimate sources and can even imitate the design of well-known companies or products.
P2P Networks – File sharing networks like BitTorrent that are popular for spreading pirate content can also spread the dangerous UIWIX ransomware virus.
Dangerous Scripts – Hacker-operated scripts and ad networks can redirect the victims to the UIWIX ransomware virus samples. They are usually found on hacked sites.
Dropper Delivery – UIWIX ransomware virus can be spread via droppers or prior malware infections.
How to Remove UIWIX Ransomware Virus
As mentioned earlier, you can remove UIWIX virus by following the manual instructions below.
WARNING! Manual removal of UIWIX virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
UIWIX Virus – Manual Removal Steps
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely UIWIX Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover _
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore _.UIWIX Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



