Crptxxx ransomware is a family of viruses which are comprised of several strains which can easily be removed by following our removal guide.
Crptxxx Ransomware Description
Security experts have discovered a dangerous new family of viruses known as CRPTXXX. At the moment the initial security analysis does not show any identical code with one of the famous malware families we suspect tha this is an independent creation.
The discovered samples shows that the ransomware contains a feature that is borrowed from the code of another threat. Upon infection the virus is able to bypas the UAC prompt which allows the malicious binary file to access elevated privileges. This can potentially lead to some dangerous capablities from being executed:
- System Files Modification – By acquiring the necessary rights to access and modify all accessible files at will the encryption engine can compromise even files that belong to the operating system which can render it partially working.
- Remote Control – The malicious users behind the virus can use it to sp on the users by introducing a Trojan component.
- Information Harvesting – Hackers can use viruses such as this one to download key settngs, stored cookies, account credentials, history and personal files that might hold sensitive information from the infectd machine.
- Additional Malware Introduction – The virus can be used to download and institute additional malware to the infected host.
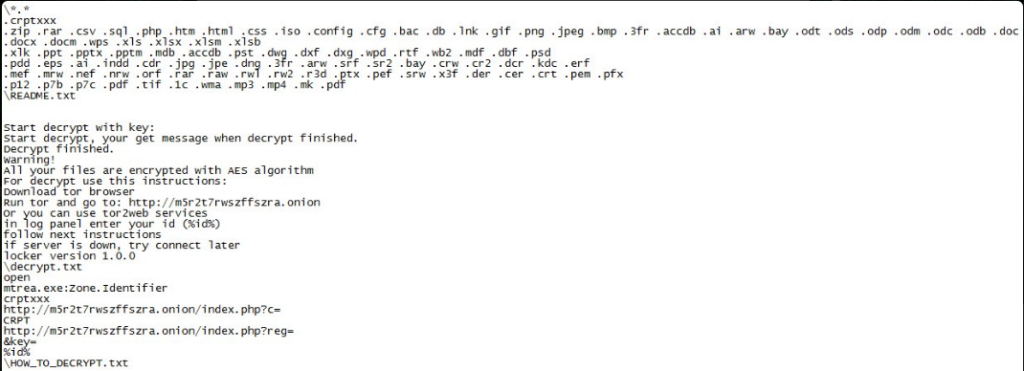
When the virus has acquired the necessary privileges it executes its built-in encryption engine. It starts to encrypt target user data which are renamed with the .crptxxx extension.The complete list includes the following:
.1c, .3fr, .accdb, .ai, .arw, .bac, .bay, .bmp, .cdr, .cer, .cfg, .config, .cr2, .crt, .crw, .css,
.csv, .db, .dbf, .dcr, .der, .dng, .doc, .docm, .docx, .dwg, .dxf, .dxg, .eps, .erf, .gif, .htm, .html,
.indd, .iso, .jpe, .jpeg, .jpg, .kdc, .lnk, .mdb, .mdf, .mef, .mk, .mp3, .mp4, .mrw, .nef, .nrw, .odb, .ode,
.odm, .odp, .ods, .odt, .orf, .p12, .p7b, .p7c, .pdd, .pdf, .pef, .pem, .pfx, .php, .png, .ppt, .pptm, .pptx,
.psd, .pst, .ptx, .r3d, .rar, .raw, .rtf, .rw2, .rwl, .sql, .sr2, .srf, .srw, .tif, .wb2, .wma, .wpd, .wps,
.x3f, .xlk, .xls, .xlsb, .xlsm, .xlsx, .zip
Depending on the strain a ransomware note is crafted:
- README.txt, HOW_TO_DECRYPT.tx – For the strain compiled on March 8.
- HOW_TO_FIX_!.txt – For the strain compiled on March 16.
The following note is displayed to the victims:
Warning!
All your files have been encrypted with AES
If you want to restore them, use this instructions:
1) Download tor browser
2) Run tor and go to: xxxx://dokg5gcojuswihof.onion
Or you can use tor2web services
xxxx://dokg5gcojuswihof.onion.to
In login panel enter your personal ID: %id%
Follow next instructions on website
If server is down – try connect later
!! Decoders from other users are not compatible with your data, because each users unique encryption key !!
!! Do not try to decrypt your data using third party software, it may cause permanent data loss. !!
As it appears the payment gateway is located on the TOR anonymous network. Each individual infection is assigned with a unique victim ID which the hackers require to be placed in a text boxto reveal the ransom fee.
Crptxxx Ransomware Distribution
The first malware samples were discovered in the beginning of March 2017. The initial security analysis shows that the hackers have used it to target English-speaking users globally. Two separate strains have been identified – one carried in an attack campaign initiated on March 8 and another one in March 16. At the moment we cannot judge which is the primary infection method but we suspect that the following are used:
- Email Spam – The hackers employ bulk email spam messages which use social engineering tricks to try and infect the target users. Such phishing techniques usually employ body text and files that appear to be sent by legitimate companies or institutions. The most likely used scenario is the use of infected documents that feature malicious macros. Upon interaction with them the payload is delivered to the host system.
- Download Sites and P2P Networks – Compromised or hacker-controlled download sites are a popuar place for distributing all kinds of dangerous viruses. BitTorrent trackers are another source of infections.
- Infected Software Installers – The CRPTXXX ransomware can be bundled with software installers distributed over the Internet. This includes a wide variety of well-known applications, games, tools, patches or utilities. Depending on the attack campaign this can include both freeware or trial versions.
- Direct Attacks – Attacks that use exploit kits or vulnerability testing frameworks can institute remote access and infection with the CRPTXXX ransomware.
Summary of the Crptxxx Ransomware
| Name |
CRPTXXX Ransomware |
| File Extensions |
.crptxxx |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove CRPTXXX Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
CRPTXXX Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
CRPTXXX Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely CRPTXXX Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Crptxxx Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Crptxxx Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



