A team of researchers from Arizona University has devised a sophisticated system that can gather information about upcoming cyber security threats from a variety of different sources such as The Dark Net, social networks, and others.
The System Alerts When Security Threats Are on the Rise
Arizona University researchers have managed to create a complex system that detects security threats in a very early stage of their development. Their method focuses on “cyber threat intelligence gathering” from all major sources the cyber security criminals utilize – social media networks, The Dark Net and user forums. Their system can collect information from hacker communities and marketplaces that offer products and services for malicious attacks.
Pre-reconnaissance cyber threat intelligence is the technique of information gathering before a malicious attack is executed against a target machine or network. The researchers state that this is an important defense mechanism against security exploits. By utilizing analysis made by threat reporting systems, administrators can defend their networks and machines against possible intrusions.
The operational demonstration of the devised system actively collects approximately 305 quality cyber threats per week. The collected data from sources from The Dark Net is organized into two categories – markets and forums.
- The gathered information gives cyber security experts data on several aspects:
- What vendors and users have a presence in multiple darknet/deepnet markets/ forums?
- What zero-day exploits are being developed by malicious hackers?
- What vulnerabilities do the latest exploits target?
Going Under for Security Threats Intelligence
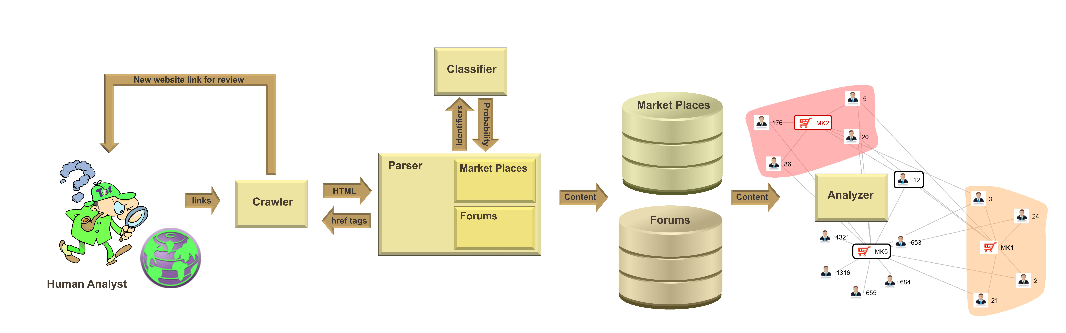
The cyber threat intelligence system can connect to The Dark Net and harvest information from both criminal markets and forums. Separate crawlers for different platforms have been created to server the system. A parser can extract the needed information and store it in a database, from there on machine learning techniques are employed to filter out only threats applying to cyber security.
The researchers have included methods that remove noise from text and descriptions, as well as other countermeasures against automated crawlers that are used by the criminal networks. The system was able to successfully identify 16 zero-day exploits from marketplace data sets over a 4-week period. Other features include the creation of social network graphs that show the relationships between vendors, marketplaces, and forums.
The researchers are currently working with a commercial partner to implement the system as a security solution.
Fore more information you can read their paper titled “Darknet and Deepnet Mining for ProactiveCybersecurity Threat Intelligence”.