Malware researchers have discovered the Kirk ransomware which encrypts target user data and is Star Trek themed, continue reading our removal guide to learn more.
Kirk Ransomware Description
Star Trek fans and computer users have one more reason to worry as computer hackers have devised a ransomware that is named after the famous saga. The infection follows the usual behaviour patterns by encrypting target user data with a strong cipher.
The initial security analysis does not show a clear connection between this particular threat and one of the famous malware families (such as EDA2, HiddenTear, Cerber and others) which means that the ransomware is created by an independent hacker or collective.
While the virus does not seem to be made by a famous entity, we have observed some advanced features that sets it apart from other similar threats:
- Stealth Protection – The virus has been found to feature a module which prevents analysis by detecting any running debugging tools.
- Volume Information Query – The ransomware is able to query information about the mounted partitions (disk drives) and all mapped networks shares.
- Creates Numerous Temporary Files – The ransomware engine is able to create numerous temporary files which are placed in various locations (both user and system folders).
- Hardware Interface – The virus is able to connect to devices and services over the LPC ports.
Upon infection the virus follows the same basic behavior patterns used by other similar threats. The virus immediately starts to create temporary files to prepare its encryption engine, while at the same time using an anti-debugging shield to protect itself from analysis or security solutions. The researchers uncovered that the virus can modify and drop all kinds of data which can cause system changes that might impact performance. It seems that the engine is written in the popular Python programming language.
The encryption engine is then started which employs a powerful cipher which targets a number of file type extensions. All affected files receive the .kirked extension and then the following ransomware note is displayed:
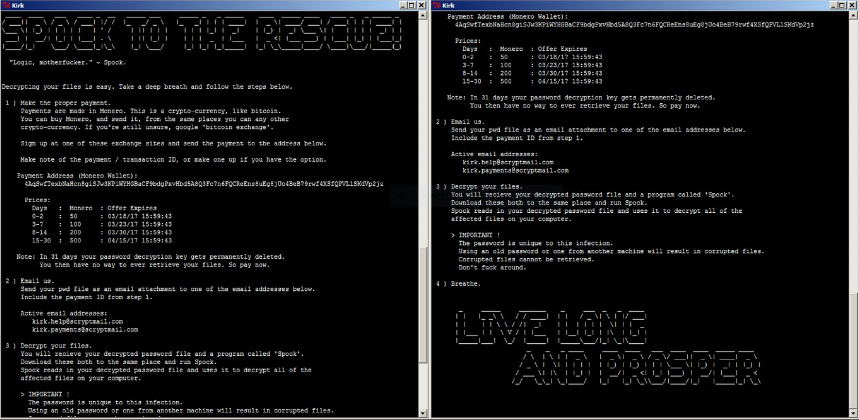
> ! IMPORTANT ! READ CAREFULLY:
Your computer has fallen victim to the Kirk malware and Important files have been encrypted – locked up so they don’t work. This may have broken some software, including games, office suites etc.
Here’s a list of some the file extensions that were targetted:
.3g2 .rar .jar .cgi .class .ltd .potx .xex .dds .3gp •IPS .pl .cd .7tt .pots .tiger .ff
.asf •31:e41 .psd .cos .)ava .hwp .sda .lbf .yrp .asx .png .wsf .swift .602 .sdd .cab
.pck .avi .tiff .ogg .bmp .vb .pdb .sdp .rx3 .t3 .flv .zip .1.74 .1scp .ods .psw .00= .epk .ltx
.ai .7z .alf .gif .xlr .xlw .wotreplay.vol .uasset .m2ts .dif.z .tif .xls .xlt .rofl .asset .bikey
.mlv .exe .wpl .tiff .xlsx .xlsm .pak .forge .patch .mov .tar.gz .ar) .htm .dot .xltx .big .1ng .upk
.mp4 .tar .deb .7s .docm .xltm .bik .311 .uax .mpg .mp3 .pkg .7sp .dotx .xlsb .xtbl .litemod .mdl .mpeg
.sh .db .php .dots .wkl .unicy3d .vef .1v1 mpeg4 .c .dbf .xhtml .wpd .wks .capx .dat .qst .cpp .sav
.cfm . WO .123 .ttarch .papa .ddv .swf .h .xml .r33 .rtf .sdc ./lei .psark .pta .vob .mov .html
.key .sdw .31k .rgss3a .ydk .gif .aimi .odp .sgl spx1 .gblorb .mpq .doc .txt .apk .pps .vor
.wb2 .rem .wtf .docx .py .bat .ppt .uot .pot .72e .bsa .pdf .pyc .bin .pptx .uof .pptm .mpk .ze4
There are an additional 441 file extensions that are targetted. They are mostly to do with games.
To get your files back, you need to pay. Now. Payments recieved more than 4e hours after
the time of infection will be charged double. Further time penalties are listed below.
The time of infection has been logged.
Any files with the extensions listed above will now have the extra extension ‘.kirked’, these files
are encrypted using military grade encryption.
In the place you ran this program from, you should find a note (named RANSOM_NOTE.txt) similar to this one.
You will also find a file named ‘pwd’ – this is your encrypted password file. Although it was generated by your computer, you have no way of ever decrypting it.
This is due to the security of both the way it was generated and the way it was encrypted. Your files were encrypted using this password.0 crypting your files is easy. Take a deep breath and follow the steps below.
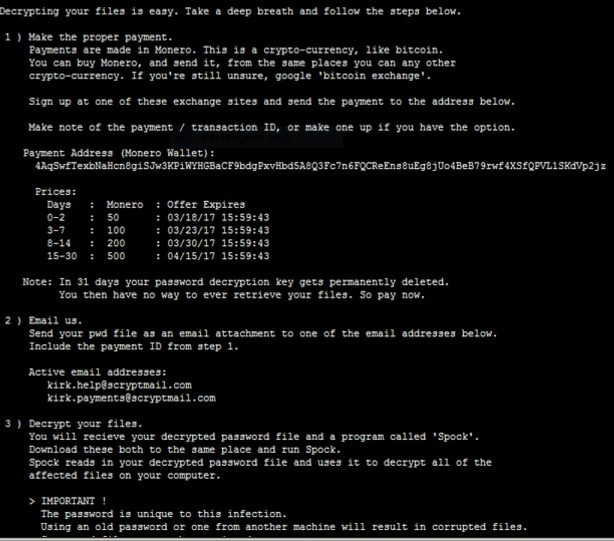
1 ) Make the proper payment. Payments are made in Monero. This is a crypto-currency, like bitcoin. You can buy Monero, and send it, from the same places you can any other crypto-currency. If you’re still unsure, google ‘bitcoin exchange’.
Sign up at one of these exchange sites and send the payment to the address below. Make note of the payment / transaction ID, or make one up if you have the option. Payment Address (Monero Wallet): 4AgSwfTembNalicnegiSJw3HPiWYHGBaCF9bdgPxvHbd5A8Q3Fc7n6FUCReEnseuEgepllo4BeR79rwf4XSfQPVL1SMV023z
Prices: Days : Monero : Offer Expires 0-2 : 50 : 03/1e/17 15:59:43 3-7 : 100 : 03/23/17 15:59:43 e-14 : 200 : 03/30/17 15:59:43 15-30 : SOO : 04/15/17 15:59:43
Note: In 31 days your password decryption key gets permanently deleted. You then have no way to ever retrieve your files. So pay now.
2 ) Email us. Send your pwd file as an email attachment to one of the email addresses below. Include the payment ID from step 1.
Active email addresses: kirk.helpescryptmail.com kirk.paymentsescryptmail.com
3 ) Decrypt your files. You will recieve your decrypted password file and a program called ‘Spook’. Download these both to the same place and run Spook. Spook reads in your decrypted password file and uses it to decrypt all of the affected files on your computer.
> IMPORTANT ! The password is unique to this infection. Using an old password or one from another machIne
result in corrupted files.Payment Address: (Monero Wallet):
XXXXXXXXXXXXXXXXXxxxxPrices:
DAys : Monero : Offer Expires
0-2 50 XXXXXXXXXXXXXXXXX
3-7 100 XXXXXXXXXXXXXXXXX
8-14 200 XXXXXXXXXXXXXXXXX
15-20 500 XXXXXXXXXXXXXXXXXNote: In 31 days your password decryption key gets permamently deleted.
You then have no way to ever retrieve your files. So pay now.2) Email us.
Send your pwd file as an email attachment to one of the email addresses below.
Include the payment ID from step 1.Active email addresses:
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX3) Decrypt your files.
You will receive your decrypted password file and a program called ‘Spock’.
Download these both to the same place and run Spock.
Spock reads in your decrypted password file and uses it to decrypt all of the affected files on your computer.> IMPORTANT !
The password is unique to this infection.
Using an old password or one from another machine will result in corrupted files.
Corrupted files cannot be retrieved.
Don’t fuck around.4) Breathe.
LIVE LONG AND PROSPER.
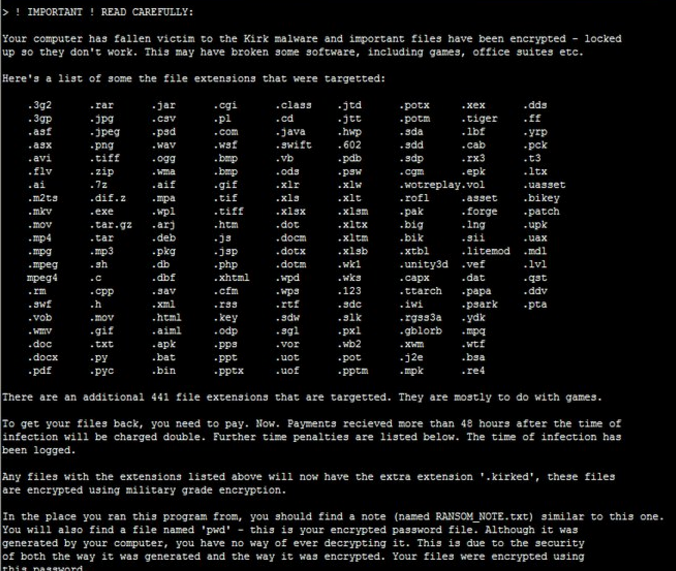
From the note we can obtain more details about the virus and its behaviour. As it appears the the creators of the threat request the recovery fee in the Monero crypto currency which is an alternative to the widely used Bitcoin system. The virus computers an unique ID of the infected machine which is based on several key variables. Like other viruses of this type the ransomware wants to achieve maximum profits, the hackers behind this threat request a different payment sum depending on the “age” of the infection.
The Kirk ransomware presents Star Trek-themed ASCII art in the note and also uses the widely used phrase/quote “Live Long and Prosper” in the end.
Kirk Ransomware Distribution
The collected malware samples are too limited in number to judge a primary infection method. We believe that the creators of the ransomware have used the following tactics to infect the compromised machines:
- Email Spam – The hackers employ bulk email spam messages which use social engineering tricks to try and infect the target users. Such phishing techniques usually employ body text and files that appear to be sent by legitimate companies or institutions. The most likely used scenario is the use of infected documents that feature malicious macros. Upon interaction with them the payload is delivered to the host system.
- Download Sites and P2P Networks – Compromised or hacker-controlled download sites are a popuar place for distributing all kinds of dangerous viruses. BitTorrent trackers are another source of infections.
- Infected Software Installers – The Kirk ransomware can be bundled with software installers distributed over the Internet. This includes a wide variety of well-known applications, games, tools, patches or utilities. Depending on the attack campaign this can include both freeware or trial versions.
- Direct Attacks – Attacks that use exploit kits or vulnerability testing frameworks can institute remote access and infection with the Kirk ransomware.
Summary of the Kirk Ransomware
| Name |
Kirk Ransomware |
| File Extensions |
.kirked |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove Kirk Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Kirk Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Kirk Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Kirk Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Kirk Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Kirk Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



