Security researchers have discovered a dangerous new exploit kit that has been hidden in malicious ads and named and named as the Stegano Exploit Kit.
The Stegano Exploit Kit Revealed
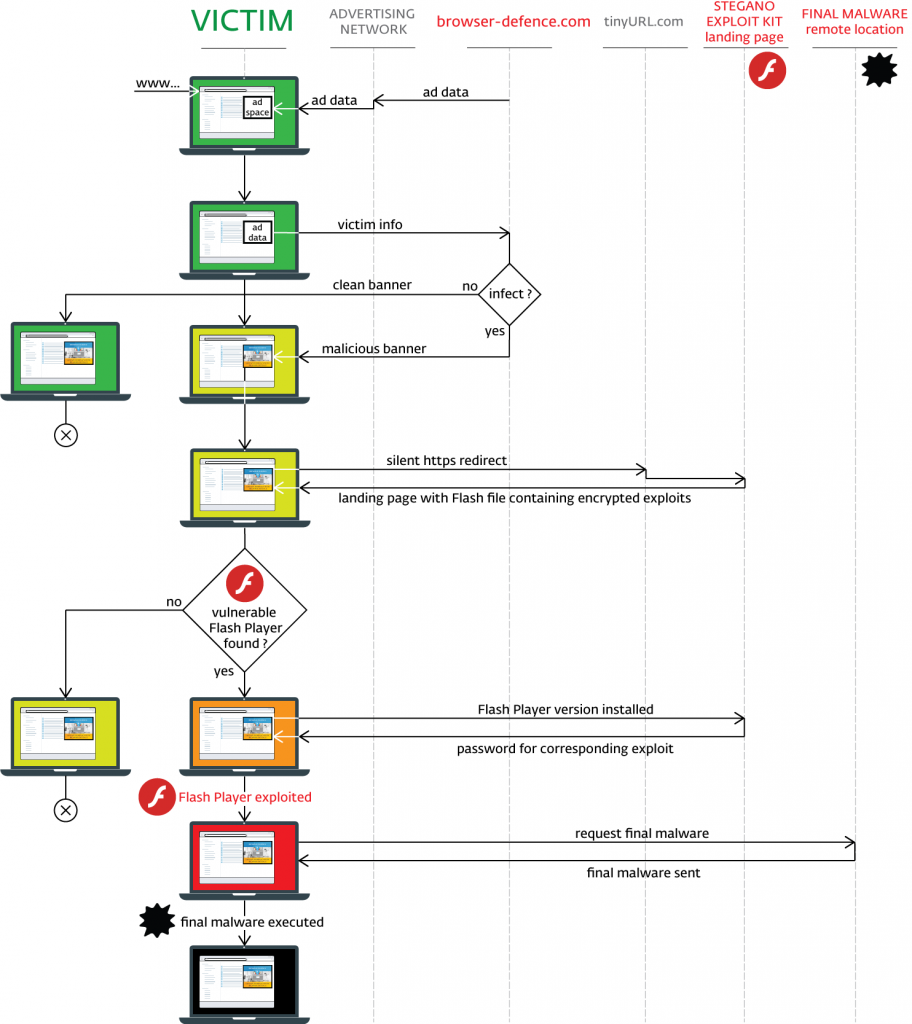
Security researchers from ESET have revealed a new exploit called the Stegano Exploit Kit as it uses the method of steganography. This is the technique of hiding various types of information and data inside other files.
The Stegano Exploit Kit is a good example of that. The dangerous software was discovered hidden in a PNG image file served in a malicious ads campaign operated by computer criminals. According to the available information it has been in active use for the past two months. So far it has been used to serve malicious ads while operating on various networks including some high-profile and popular sites.
When the code is extracted and executed it redirects the computer users to a gate address which filters out the victims. The server redirects only the visitors who use the Internet Explorer browser and so far they are have been the only victims.
The kit uses the exploit described in the CVE-2016-0162 disclosure which allows remote attackers to determine the existence of files via crafted Javascript code. This is also known as the “Internet Explorer Information Disclosure Vulnerability.” In addition this flaw allows the hackers to detect the presence of anti-virus and anti-spyware solutions. If that is the case then the connection is terminated to avoid any detection of Stegano’s activity.
To infiltrate the target computer hosts the Stegano exploit kit uses three Adobe Flash vulnerabilities:
- CVE-2015-8651 – Integer overflow in Adobe Flash Player before 18.0.0.324 and 19.x and 20.x before 20.0.0.267 on Windows and OS X and before 11.2.202.559 on Linux, Adobe AIR before 20.0.0.233, Adobe AIR SDK before 20.0.0.233, and Adobe AIR SDK & Compiler before 20.0.0.233 allows attackers to execute arbitrary code via unspecified vectors.
- CVE-2016-1019 – Adobe Flash Player 21.0.0.197 and earlier allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via unspecified vectors, as exploited in the wild in April 2016.
- CVE-2016-4117 – Adobe Flash Player 21.0.0.226 and earlier allows remote attackers to execute arbitrary code via unspecified vectors, as exploited in the wild in May 2016.
The Stegano Exploit kit has been used to deliver mainly banking Trojans such as Ramnit however the security experts to see a payload change if the kit grows popular among hackers.
For more information you can visit the detailed blog post to learn more about it.



