Recent research conducted by security experts from Symantec indicates that the Gatak Trojan malware is distributed via malicious websites that offer free keygens for various software applications. Victims that are tricked to download a product key receive a bundled malware with it. Cyber criminals aim to open backdoors on infected computers so they can conduct attacks on a company’s internal network and steal sensitive information.
The offered keys are primary for software that is used in professional environments. Undoubtedly the vendors of the applications have nothing in common with the malicious actions of the attackers. The security company Symantec has revealed a list of some applications which are included in the malicious scheme:
- SketchList3D
- Native Instruments Drumlab
- BobCAD-CAM
- BarTender Enterprise Automation
- HDClone
- Siemens SIMATIC STEP 7
- CadSoft Eagle Professional
- PremiumSoft Navicat Premium
- Originlab Originpro
- Manctl Skanect
- Symantec System Recovery
As it could be expected the generated keys from the websites are not working and their main purpose is to trick the user into executing the malicious keygen. You can find additional information on the applications in Symantec’s article.
The Gatak Trojan
The Gatak Trojan has been used for attacks since 2011. The malware has two main components – Trojan.Gatak.B and Trojan.Gatak.
Trojan.Gatak.B is its lightweight deployment module that injects itself into the explorer.exe process. When this happens the Trojan collects information from the compromised computer including:
Then it selectively installs additional payloads.
Trojan.Gatak is the main module. It is a backdoor Trojan that may be dropped on the computer by another threat. The Trojan.Gatak serves with obfuscation for its delivery. It may land on the computer as googletalk.exe or Skype.exe. And they might be located at:
%UserProfile%\Application Data\Google Talk\googletalk.exe
%UserProfile%\Application Data\Skype\Phone\Skype.exe
Furthermore, the Trojan.Gatak may create new values in Run Windows Registry key in order to execute its malicious files every time the Windows OS starts. Then it injects itself into the explorer.exe process and opens a backdoor that enables the connection to its malicious remote locations.
One of the most notable Gatak’s features is the steganography function. It allows the malware to hide data within image files. Thus Gatak could download a PNG image file from one of the URLs hardcoded into the malware without raising any doubts. However, the pixel data of the picture contains an encrypted message that Gatak Trojan can decrypt. The message consists of commands and files for execution.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
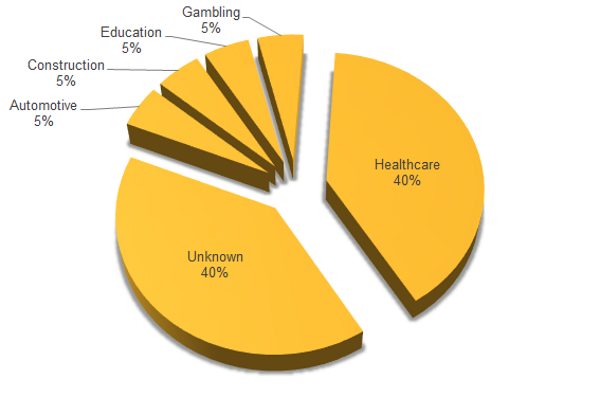
Healthcare Sector Is the Most Targeted One
Most of the attacks are directed to the healthcare industry. Here is how Symantec answer the question “Why healthcare?”:
Healthcare organizations can often be pressurized, under-resourced, and many use legacy software systems that are expensive to upgrade. Consequently, workers could be more likely to take shortcuts and install pirated software. While organizations in other sectors appear to be infected less frequently, the attackers don’t appear to ignore or remove these infections when they occur.
Which other sectors are a target of Gatak malware attacks?