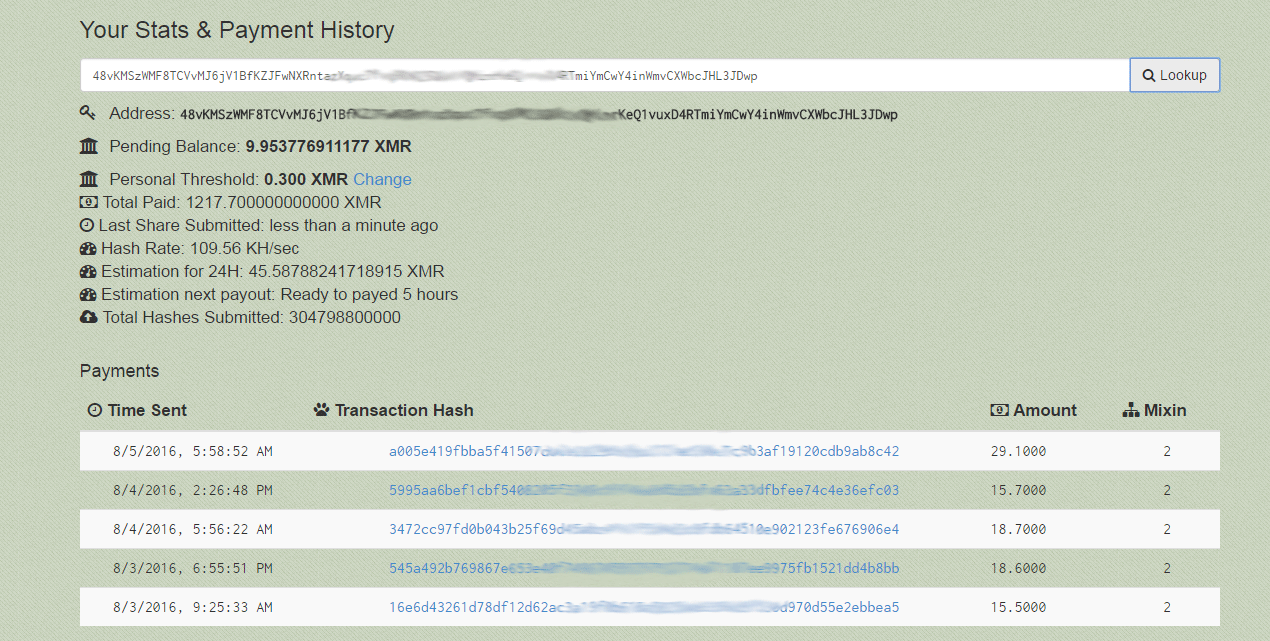
A new Linux Trojan written in Go programming language has been observed in the wild. The Trojan is called Linux.Lady.1 and has been discovered by specialists at Dr.Web labs. It is spreading through misconfigured Redis database servers and has the functionality to download a cryptocurrency mining program.
Go is a programming language developed by Google and most of its libraries are hosted on GitHub. Programs written in Go language are rarely detected in the wild. The code of Linux.Lady.1 mostly relies on the Go’s open source available on GitHub.
Working Mechanism of Trojan Linux.Lady.1
Once Linux.Lady.1 Trojan lands on the system it searches for particular keys and in case they are missing it terminates itself. Otherwise, it successfully infects the system. If Trojan Linux.Lady.1 finds keys Version, Install or D, it automatically launches on the system. Entering through different keys leads to various actions of the Trojan at the infection stage that follows.
After it makes some modifications on the system, it sends information to its Command and Control server. The data for Trojan’s version, a number of CPUs on the infected machine, host’s name, number and name of running processes, the family of the operation system, name of the operation system and host’s uptime is delivered to the Linux.Lady.1’s C&C. The C&C server sends back a configuration file to the Trojan.
This file has the functionality to download, install and launch a cryptocurrency mining program. Monero is the cryptocurrency targeted by Trojan Linux.Lady.1. The generated income is transferred to the cyber criminals’ financial account.
Misconfigured Redis Servers Are Vulnerable to Trojan Linux.Lady.1 Infection
The received configuration file from the C&C server contains a list of particular websites that allow this Linux Trojan to identify an external IP address and attack other computers of the network. In case the Trojan finds not correctly configured Redis server it establishes a connection to the remote servers without entering a password.
Once there is a connection between the server and the infected PC the malware downloads the malicious script Linux.DownLoader.196 (as detected by Dr.Web). This script is added to the cron scheduler. Then an installed copy of Linux.Lady.1 on the compromised host adds a key to the list of authorized keys. This key serves for connection to the computer over SSH protocol.
Information on over 6 000 compromised Redis database servers has been recently reported by the researchers from Risk Based Security (RBS). The misconfigured Redis servers are over 30 000. So the same number goes for Redis servers that may be infected by Linux.Lady.1 trojan. The servers are available online and are without a password.