BlackJoker HappyDayzz Virus – Further Analysis
After an infection by BlackJoker ransomware has occurred on the computer of the user, the virus may connect to a remote host and download its files on the user’s computer, which are the following:
- Executable (.exe) file with a random name.
- A “How To Recover Encrypted Files.hta” file, containing the ransom note (not malicious).
After this has become a fact, the BlackJoker ransomware begins to perform different activities on the infected computer. One of them may be to delete the shadow volume copies on the infected computer. This is usually achievable by imputing different variations of the vssadmin command:
->vssadmin delete shadows /for={Volume} {/oldest | /all | /shadow={ShadowID} {/quiet}
In addition to these activities, the BlackJoker (HappyDayzz) virus may perform another action, and it is to modify the Windows Registry Editor in its interest. This happens by adding registry value strings with custom data. For example, if the virus wants to run the malicious .exe file on system startup, it will attack the following registry sub-keys:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
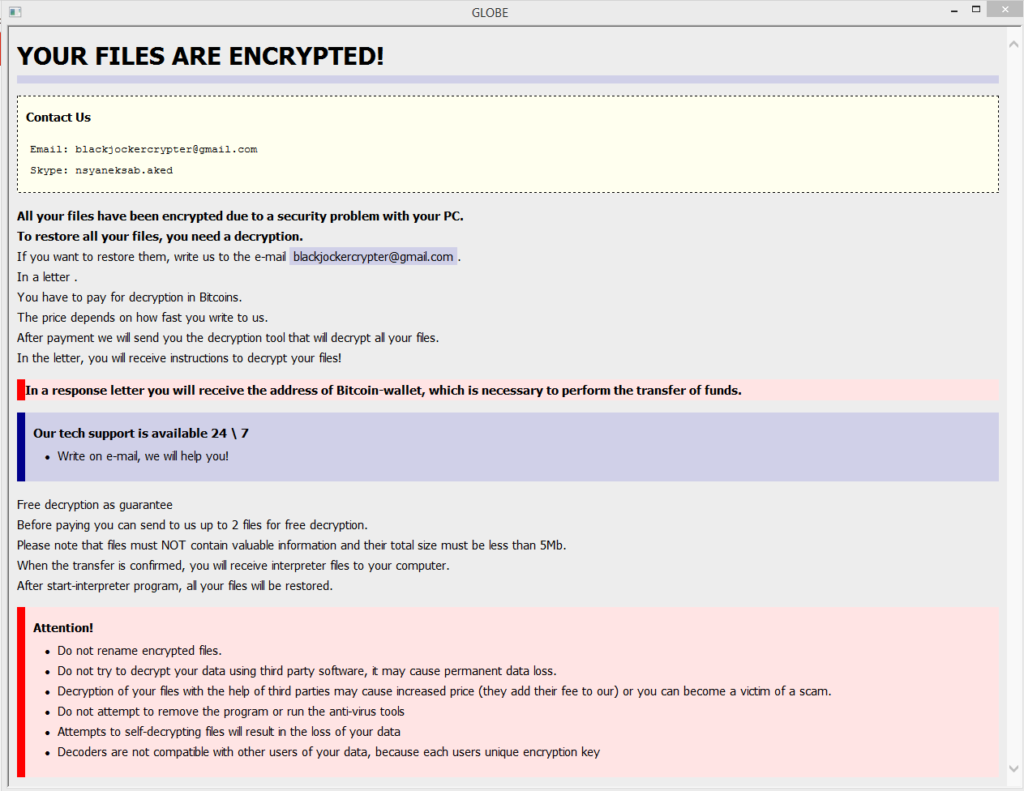
In addition to those activities, the BlackJoker ransomware may open the How To Recover Encrypted Files.hta file which contains the ransom demands by the cyber-criminals. The note has the following message to the victims:
YOUR FILES ARE ENCRYPTED!
Contact Us
Email: [email protected]
Skype: nsyaneksab.aked
All your files have been encrypted due to a security problem with your PC.
To restore all your files, you need a decryption.
If you want to restore them, write us to the e-mai [email protected] .
In a letter .
You have to pay for decryption in Bitcoins.
The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
In the letter, you wi receive instructions to decrypt your files!
In a response letter you will receive the address of Bitcoin-wallet, which is necessary to perform the transfer of funds.
Our tech support is available 24 \ 7
• Write on e-mail, we will help you!
Free decryption as guarantee
Before paying you can send to us up to 2 files for free decryption.
Please note that files must NOT contain valuable information and their total see must be less than 5Mb.
When the transfer is confirmed, you wl receive interpreter files to your computer.
After the start-interpreter program, all your files wi be restored.
Attention!
• Do not rename encrypted fifes.
• Do not try to decrypt your data using third party software, it may cause permanent data loss.
• Decryption of your files with the help of third parties may cause increased price (they add their fee to our), or you can become a victim of a scam.
• Do not attempt to remove the program or run the anti-virus tools
• Attempts to self-decrypting files wi result in the loss of your data
• Decoders are not compatible with other users of your data, because each user’s unique encryption key
The Encryption of BlackJoker(HappyDayzz) Virus
AES (Advanced Encryption Algorithm) is the cipher used by this virus to encode the data encrypted by it. This cipher is employed by the executable of the virus to replace data from widely used types of files with the cipher data, making them no longer openable. Targeted files by BlackJoker are the following:
- Microsoft Office documents
- OpenOffice files
- PDF documents
- Text files
- Database type of files
- Photos
- Music files
- Video files
- Archive types of files
- Image files
Since this virus belongs to the Globe v3 ransomware family, it also performs multiple other activities typical to these viruses. One of them is to heavily change the name of the file and add the .happydayzz file extension, an e-mail address for contact and a unique random A-Z 0-9 number. Below, you can see an example of how a file attacked by the BlackJocker (HappyDayzz) threat looks like:
[[email protected]]. 73176636534547467259595D756258417A0D0A 55674C5.happydayzz
Methods of Dissemination
The infection may be triggered with the help of a Trojan dropped on the computer. Hackers are most likely to distribute the malicious software via spam email campaigns. This method allows them to impersonate legitimate sources in order to trick users into clicking a link or downloading an attached file. These two components may cause an infection with HappyDayzz ransomware. A link’s destination will probably be a webpage with compromised source code. Thus the malicious code injected by the hackers will trigger an unnoticeable download of all ransomware payloads. Once they are on the PC, the infection process starts automatically. The file attachments may be documents, PDF files or archives with abused content. The infection can begin when the malicious file is opened.
Social and other types of file sharing networks may also be used by cyber criminals as a mean of HappyDayzz ransomware dissemination.
It is also possible to witness a ransomware infection after you download a freeware from shady websites. The bundling technique allows criminals to conceal the malicious code and make you feel like the content is safe.
HappyDayzz Ransomware – How to Remove and Get the Files Back
Since there is no information about this particular Globe v3 iteration to be decryptable, we advise you to back up the encrypted files by it for a later time, when a decryptor becomes available. In the meantime, feel free to remove the virus and restore your files by following the instructions below. In case you are having difficulty in manually removing HappyDayzz, experts always recommend using an advanced anti-malware program to remove this threat and prevent further intrusions automatically.
Once you remove the ransomware completely you may try to restore encrypted data with the Emsisoft’s decrypter for Globe v3 ransomware.
Further information on how to use the decrypter you can find by clicking here.
Summary of HappyDayzz (BlackJocker) Ransomware
| Name |
HappyDayzz (BlackJoker) Ransomware |
| File Extension |
.happydayzz |
| Ransom |
0.5 – 1.0 BTC |
| Easy Solution |
You can skip all steps and remove HappyDayzz (BlackJoker) ransomware with the help of an anti-malware tool. |
| Manual Solution |
HappyDayzz (BlackJoker) ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam emails, malicious URLs, malicious attacments, exploit kits, freeware. |
HappyDayzz (BlackJoker) Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely HappyDayzz (BlackJoker) Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



