In our previous publication we introduced how typical ransomware threats operate. And while users may fall victim to different types of infected applications, there are some popular examples which continue to plague computer users worldwide. In this post we give brief information about them and investigate their behavior, intrusion sources as well as removal instructions.
CTB-Locker
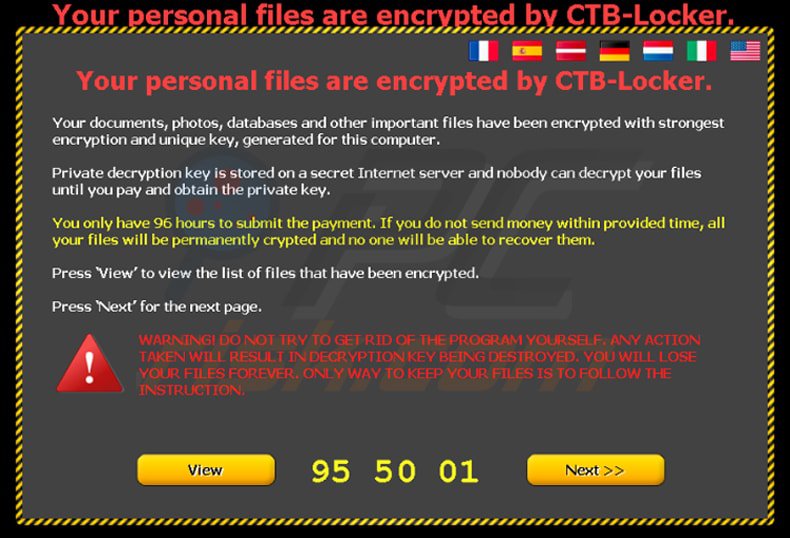
Ransomoware Description: The name CTB-Locker is actually short for several key features of the ransomware – “C” stands for “curve”, referring to the Eliptical Curve Cryptography technique, which encrypts the target data with unique RSA keys. “T” designates the use of the Tor anonymous network and “B” refers to the Bitcoin crypto currency used for the ransomware payment. CTB-Locker uses the powerful RSA 2048 encryption public-key cipher to encrypt the victim files.
Ransomware Behavior: CTB-Locker is a formidable ransomware virus that spreads mainly malicious email messages and counterfeit software downloads (targeting popular applications such as Adobe Flash, Internet Explorer, etc.). When a successful infection has been made the ransomware encrypts all files with the most popular file extensions (doc, docx, xls, ppot, pdf, psd, eps, ai, cdr, jpg and others) and demands a payment for decryption. The criminal developers have ensured that the ransomware operates on all Microsoft Windows operating systems. There are numerous malware registry entries that are added to the system configuration.
A variant of the CTB-Locker was identified that targets Germany, the USA, Netherlands and Italy. This is possible as the ransomware has advanced functionality that permits it to target specific geographic regions. In these cases the source of infection was mainly fake fax notification emails containing malicious web links and attachment with the malware payload. The cyber criminals also utilized an extended time limit for the payment.
Another type of CTB-Locker infects web servers exploiting security vulnerabilities. The virus defaces the root of the host and replaces the homepage with the ransomware notification. The victim server’s files uses two different AES-256 encryption keys. The developers of this variant allow the webmasters to “test” decryption by offering to decrypt two random files for free. If the victims want all affected contents to be decrypted they must pay the ransom sum.
The ransomware creates several files in the system directory: AllFilesArelocked.bmp (an image file), DecryptAllFilex.txt (text description) and .html files with folders containing the encrypted ransom files. These files contain the ransomware notification and instructions for the payment. The criminal developers have bundled the Tor anonymous browser to execute the payment in the Bitcoin crypto currency.
Ransomware Removal: To date there is no perfect automated solutions that deals with all variants of CTB-Locker. Computer experts advice all users to preserve secure copies of their sensitive information. There are several methods that can aid in the ransomware removal:
- Using system restore methods may regain some of the files that have been encrypted by the ransomware. Access the built-in program by typing “System Restore” in the Windows Menu. Choose a date before the infection in order to restore to an earlier date.
- You can use a “Ransomware Decryptor” to decrypt the encrypted .ctb files. Download the RannohDecryptor tool from the official source and execute it on the victim system.
- Use trusted antispyware tools with the latest updates applied in Safe Mode remove CTB-Locker itself.
Ransomware Aliases: Inject2.BJOA [AVG], Trojan.GenericKD.2055176 (B) [Emsisoft], Trojan.Win32.Ransom.345088.B[h] [ViRobot], Trojan.Inject!vI9OfWiyQlw [Agnitum], Trojan.Win32.Inject.ttcq [Kaspersky], Win32:Injector-CLC [Trj] [Avast], TROJ_FRS.PMA000LU14 [TrendMicro-HouseCall], Win32/Tnega.RHSHUPD [TotalDefense], Filecoder.EI [Norman], Trojan.Win32.Inject.dlgxbp [NANO-Antivirus], TrojWare.Win32.Amtar.amu [Comodo], Trojan.Encoder.853 [DrWeb], Trojan.Inject.Win32.124416 [Zillya], W32/Filecoder.EB!tr [Fortinet] and Win32/Filecoder.EB [ESET-NOD32].
TeslaCrypt
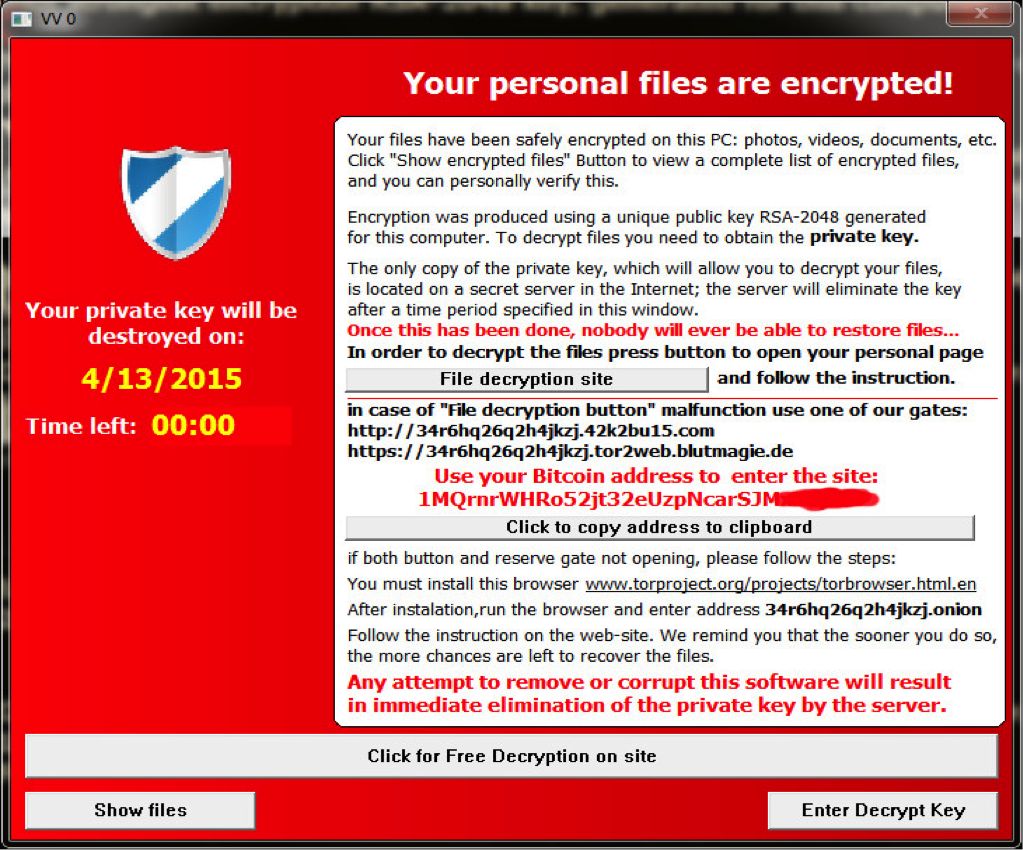
Ransomoware Description: TeslaCrypt is one of the most famous examples of ransomware that affected a large portion of Internet users. It uses a strong RSA cipher as its encryption method and has several iterations of updates to its code. The ransomware encrypts all files on the victim machine without extensions and renders them corrupt.
Ransomware Behavior: Upon successful infection the threat creates several files on the user’s Desktop and adds malware registry entries that enables it to run at system startup. After successful execution a ransom notification message is displayed. TeslaCrypt is unusual as it also encrypts computer game save files as well. The malware targets many different types of games and also affects Steam activation keys. TeslaCrypt is most often distributed using email attachments or malicious website links that point to the Angler Exploit Kit, which is usually bundled with the ransomware. The kit uses software vulnerabilities to gain access to the target system. Upon successful infiltration TeslaCrypt follows a set of instructions that deletes all system Volume Shadow Copies, encrypts the user files, sends the encryption keys to a remote C&C servers and imposes anti-tampering protection.
Ransomware Removal: The master encryption keys for TeslaCrypt were released publicly which lead to the creation of efficient countermeasures, capable to restore files from any iteration of the ransomware infection. One such decryptor is available from Cisco Talos. This is a command line tool that is used through the command prompt. The user must copy the “key.dat” file that is usually stored in the AppData folder to the tool’s location. If such a file is not available on the computer the utility is able to create one on its own.
Ransomware Aliases: Trojan-downloader:js/teslacrypt.[variant] , Trojan.TeslaCrypt.[variant], TeslaCrypt.[variant], Js.teslacrypt.gen.[variant].
Locky
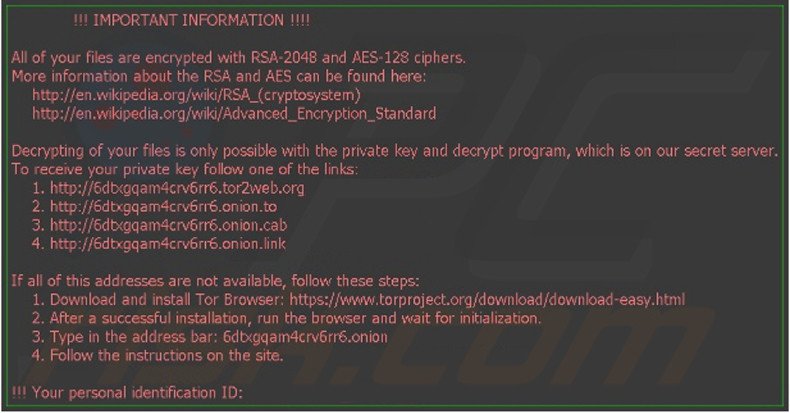
Ransomoware Description: Locky has grown to be one of the most widespread ransomware malware around the Internet. It doesn’t feature advanced techniques or outstanding distribution methods. It has become famous and popular following massive criminal campaigns against computer users worldwide. Numerous variants and offspring malware have been created by malicious users using Locky as basis.
Ransomware Behavior: While the basic Locky ransomware is seen as a variant of TeslaCrypt a lot of reported infections and the offspring of many malware that formed out of Locky’s base, make it a formidable malicious tool. The most widespread path of infection are corrupted attachment in phishing email messages. The attachments are .doc files (Microsoft Word document files) that contain text masquerading as macros. Upon activation of the macros feature the Locky ransomware is downloaded and executed. Other distribution methods include the typical malware sources – counterfeit software updates, P2P files and clients and exploit kits.
The virus behavior encrypts user data and renames the target files with combinations of 16 letters and digit combinations, then processes them with the .locky extension. This makes identification of the victim files impossible, the encryption used is also very strong RSA-2048 and AES-1024 ciphers are used.
Both of these algorithms use asymmetric cryptography and require the private key for successful decryption. This is held by the malicious users on remote servers controlled by them. A large number of file extensions are affected, comparable with those of TeslaCrypt. The malware then takes an extra step of inflicting damage by deleting the Shadow Volume copies of the encrypted files and all found System Restore points. Locky places malware ransom instructions to the victims in the Desktop and in each folder where an encryption has been executed. The malware also changes the user Windows wallpaper to a warning image that contains the contents of the ransom text file. Locky also adds entries in HKCU\Software\Locky.
Updated variants of Locky also target network shares. A notable Locky attack was executed in February this year. The agressive ransomware caused system shutdown in some of the hospital sectors. The damage caused a disturbance of the usual hospital operations. The IT staff was forced to pay the ransom sum to the cyber criminals to restore access to their files as a solution was not available then.
This event led to further attacks against similar targets. Two hospitals in Germany also became victim to Locky. THE US-CERT (United States Computer Emergency Readiness Team) issued warnings against Locky proliferation across the country and abroad. Top infected countries include The Netherlands, United States and Tunisia.
Ransomware Removal: There are no known decryption software that can restore the original files infected with Locky. Security researchers worldwide are currently investigating possible solutions. Computer users infected with Locky should be aware that there are a number of ransomware threats that imitate Locky. You can view tutorials for removing the PowerLocky and Zepto clones of Locky on our website.
Users are advised to follow the protection tips outlined in this article to evade infection with Locky or other threats.
Kovter
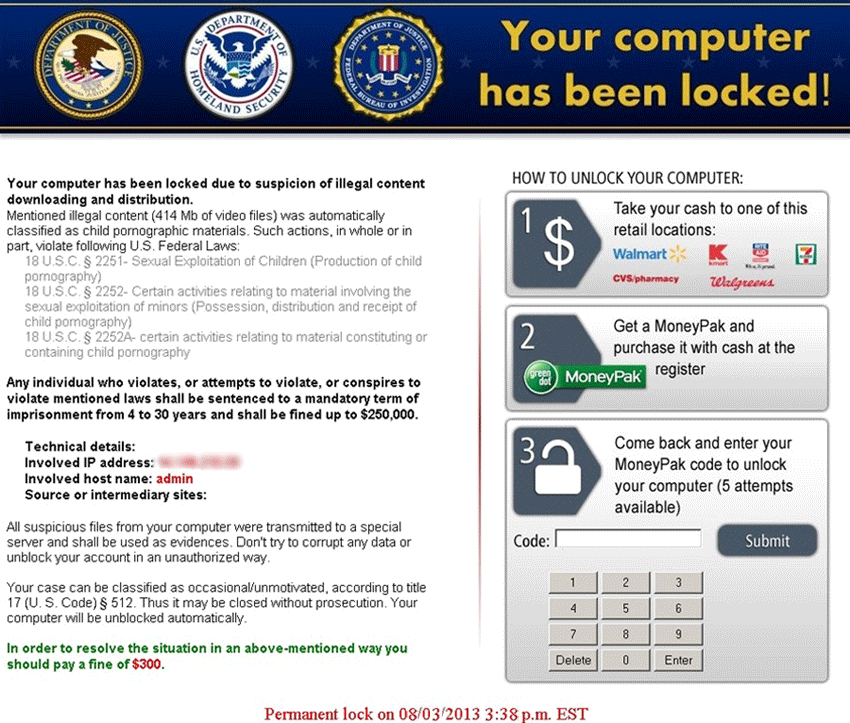
Ransomware Description: Kovter is one of the most well-known ransomware spread across the Internet. It uses a common police impersonation scam to lure users into payment. Kovter was first detected 2013 and has evolved into an intricate security threat ever since. The contemporary versions use unique tactics in scamming the victims. Like similar malware it uses a Winlocker component to block access to the infected host.
Ransomware Behavior: Kovter is a notorious malware that has seen extensive malicious use since its inception. The first reports of successful attacks were published in 2013 when Kovter was acting as a police ransomware. During 2014 and 2015 the code base changed as updates were committed and the ransomware conducted “click fraud” attacks as well. The latest evolution of Kovter was reported this year as the malware was updated to a new major version.
Some of the unique features are the ones that are integrated into the police ransomware variant of the malware. Typical distribution sources are identified—malicious clickbait links, fake emails with Kovter attachments or web links leading to executable files infected with the malware.
Upon infiltration of the target host Kovter uses an alternative method of scamming its users. It actively eavesdrops on the users Internet traffic. When an username and password combination or another type of login is executed or a file sharing application is downloading a file, the malware pops up a ransomware notification message impersonating the Police or the FBI.
Social engineering is used as the malware presents information from actual browser history and file sharing applications interaction. Some of the Kovter variants explicitly also scan for user searches of pornographic material and alert those attempts in the ransomware window.
The fact that Kovter uses an algorithm to craft a designed message into scaring the users makes it a formidable threat to unsuspecting users. At its peak the police ransomware stage of Kovter is believed to have impacted one million computers over the world.
In 2014’s evolution of the malware the malicious software added improved evasion detection countermeasures. While monitoring the victim’s web traffic the application also performed click fraud from the victim machines. This was executed using the command line.
In 2015 Kovter became “Fileless”, essentially rendering the malware very difficult to detect. This made the threat easier to spread as it utilized more advanced methods of intrusion. The latest iteration of Kovter encrypts the majority of the users files as usual. However Kovter’s cipher was not very strong making it easy to decrypt.
The latest version of Kovter is spread mainly through malicious web scripts, infected downloads and rogue programs. One of the main sources are actually PDF documents with infected macros. Kovter uses commonly used system files to obfuscate itself: notepad.exe, svchost.exe, setup.exe, patch.exe, update.exe and others. The malware executes malicious script upon infection to encrypt the most commonly used file extensions.
Security experts worldwide speculate what the next update will bring in terms of feature additions and behavior change. So far the top targeted countries with most infections are Hungary, Germany and Poland.
Ransomware Removal: Specific Kovter removal applications exist for some of the variants of Kovter. Symantec has published a utility that removes some strains of the ransomware. Download the application and follow the on screen instructions to remove the malware.
Ransomware Aliases: Trojan.Win32.Kovter.kj, Trojan.MulDrop6.7552, TR/Kovter.311854, Trojan: Win32/Kovter.E, Trojan.Kovter.A, Trojan:Win32/Kovter.C
We hope you enjoyed this brief overview of some of the most popular ransomware. Please take a few seconds to vote in our poll.
[poll id=”2″]



