
Programmable logic controllers (PLCs) made by the Allen-Bradley Rockwell Automation company are vulnerable to remote attacks due to an undocumented SNMP community string. The issue has been reported in a security advisory by Cisco Talos and is cataloged under CVE-2016-5645. The vulnerability allows malicious users to gain full control of the devices. These logic controllers are used in various critical industries across Europe, Asia, and the United States. Manufacturing industries, water, wastewater and chemical facilities are affected and the damage effects of the issue may be severe.
SNMP String Renders Rockwell PLCs Vulnerable to Remote Attack, CVE-2016-5645
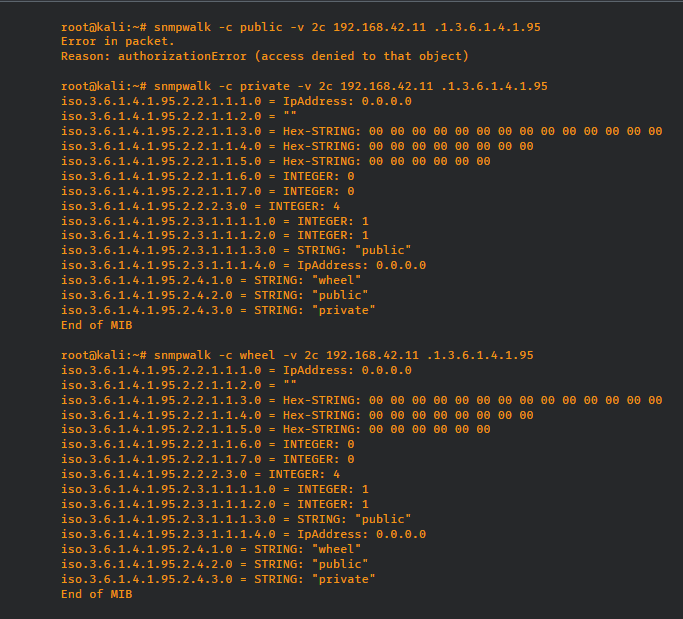
The Cisco Talos security researchers identified and investigated the cause of the vulnerability. It affects the MicroLogix 1400 PLC system, and Rockwell has shared that versions 1766-L32BWA, 1766-AWA,1766-L32BXB, 1766-BWAA, 1766-L32AWAA, AND 1766-L32BXBA are vulnerable. The cause lies in the default configuration of the devices that contains an undocumented SNMP string. The SNMP (Simple Network Management Protocol) is a standard that is used to collect and organize information as well as operate managed devices on networks. It is widely used on professional and industrial grade devices such as routers, switches, workstations, printers and other types of network capable equipment.
The SNMP string’s name is “wheel” and it exposes read/write permissions to system configuration files and the device firmware. The Cisco Talos experts state that the vulnerability may also allow access to other object identifiers. The SNMP capabilities are used by the logic controllers for applying firmware updates to the products.
The string allows malicious users to gain full remote control of the victim machines and grant access configuration settings. Full remote access also means that ability to replace the firmware of the controllers rendering them potentially unusable or even dangerous. Such tactics could be used for industrial sabotage or espionage. Significant damage can be done against critical systems that operate wastewater plants or heavy industries.
The published security advisory by the ICS-CERT (Industrial Control Systems Cyber Emergency Response Team) states that the vulnerability is high risk due to the high that an attacker with a low skill would be able to exploit the issue.
Mitigation of the vulnerability
As the SNMP capabilities are part of the firmware update feature, they cannot be removed from the affected devices. Rockwell Automation provided a number of solutions to mitigate the risks of the security issue.
- The use of the “RUN” key switch setting. This option prevents unauthorized firmware updates from running.
- The use of various network security mechanisms such as firewalls and routers to block the remote SNMP requests.
- Disabling the SNMP service daemon.
- Minimizing network exposure of the affected logic controllers.
- Setting up isolated local control system networks for management purposes.
- Using secure methods such as virtual private networks for remote access and management.
The relevant CVE ID is CVE-2016-5645 with a score of 7.3. For more detailed information about the vulnerability, you can read the public Talos report available on their website.



