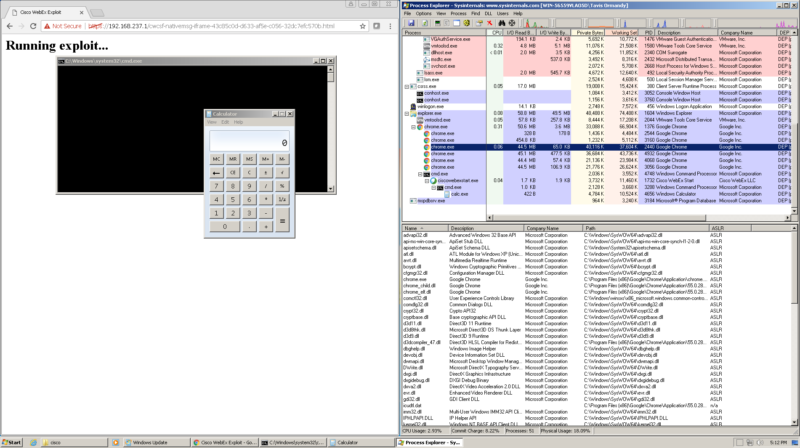
The online communications platforms Cisco WebEx has been found to feature a dangerous Chrome extension that exposes its users to dangerous vulnerabilities.
WebEx Chrome Extension Vulnerable To Dangerous Hacks
Security experts have identified that the Cisco WebEx communications and collaborations platform had a very dangerous vulnerability in itself. The issue effectively left all 20 million users a possible target of dangerous attacks. According to several experts this is one of the most severe security issues in recent years for the following reasons:
- The WebEx platform is used mainly by enterprise customers. This makes potential intrusions very dangerous as criminals can harvest sensitive information from the internal business networks.
- The dangerous exploit is very easy to implement in practically every site.
The problem is rooted in the fact that arbitrary code execution can be used by using a magic pattern. The code is used using the nativeMessaging function which is used by the software. The protocol allows any criminal to use the combination of the pattern and the target code to execute various commands on the target hosts. There are several proof-of-concept demonstrations that showcase how the vulnerability can be leveraged.
The WebEx Chrome Extension works by following the following behavior:
- The extension uses its own API and passes JSON messages between itself and the site where the WebEx session is initiated and the native browser code on the Google Chrome Browser.
- The extension inserts information about the session, a large part of which is sensitive and can be used in malicious ways in further attacks.
- One of the properties is an embedded scripting language that allows for native code interaction. This allows the attackers to call C functions directly by using the JSON objects.
An investigation into the WEbEx domain has discovered the following issues:
- The domain doesn’t use HTTP Strict Transport Security.
- The domain doesn’t use Content Security Policy (CSP).
- According to a Mozilla Observtory scan on it, the domain host doesn’t follow any “web hygiene tasks”.
The code combination can be published on every web site. A covert way of making this possible is by storing the string in an HTML-based iframe tag. This prevents the visitors from seeing the code in their windows. Any cross-site scripting exploits also pose a considerate threat.
On the bug tracking site a fix was released publicly and the vendor has rolled a critical update shortly after that in version 1.0.3.
Update: 3rd-Party Patch Released
A Third-party micropatch has been released by experts from ACROS Security. Even though the Chrome browser has been updated, according to the security experts doubt that this is a final solution to the issue.
In addition they are working on a “0patch” technology that will allow vendors to deploy microscopic patches to amend vulnerabilities in an easier and quicker manner.
For more information about it you can read their in-depth blog post.



