Researchers Uncovered a dangerous attack campaign that delivers the BrickerBot malware that is able to literally destroy IoT devices.
BrickerBot IoT Malware Spreads Rapidly
Security specialists detected an ongoing attack campaign that carries a dangerous new weapon called the BrickerBot. This is a new malware that infects IoT devices and physically disable them and cripple their functionality. The discovery was made via a honeypot network of servers that are being operated by the Radware cyber security company. According to their reports the first instances of the virus date back from March 20. At the moment the virus targets only BusyBox shells running on the Gnu/Linux operating system. Its interesting to note that the developers have created two instances – named BrickerBot.1 and BricketBot.2.
The route of infection is through vulnerability testing of open Telnet ports. They are usually used by various services and applications to relay remote execution commands or files. This tactic is used by many other bots like Mirai, LuaBot, all of them use a list of default administrator credentials. This means that users can defend their devices by changing their passwords when they configure them.
BrickerBot IoT Infection Pattern
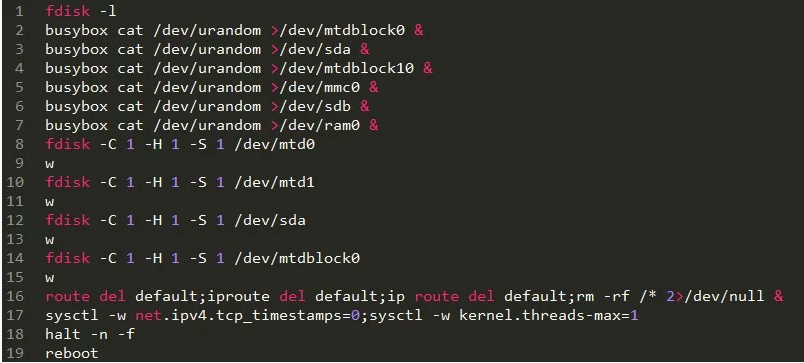
The virus performs different sets of commands depending on the version. However both of them use similar behavior patterns which allowed the researchers into uncovering its routine of execution:
-
The malware writes random data to the available storage devices. This depletes the internal memory which can lead to several types of problems – applications may stop running or data may not be able to be processed.
-
The malware disables the TCP timestamps using a command parameter. This can lead to Internet connectivity problems and can cause serious network disruptions. Such modifications can hinder the operating system itself as many of its processes rely on network streams.
-
BrickerBot sets the maximum number of kernel threads to one. This a very dangerous modification as it can effectively stop all kernel operations.
-
The affected device is rebooted.
As a result of this pattern the devices are rendered technically broken. The infection uses a simple sequence of commands which allows for a very operation. In practice the devices can be broken in a matter of only a few seconds. The detected attack campaign has been categorized as aggressive, the specialists observed that almost 2000 intrusion attempts have been detected on the honeypot servers alone. The two versions of the virus are being distributed in a different manner:
-
BrickerBot.1 – The first iteration is spread by a mass attack campaign that is distributed by a lot of IP addresses globally. The attacks have been traced to a Ubiquitti network of devices. This likely means that the virus contains a botnet module. The affected devices range from access points and bridges to routers. It appears that all of them run an old version of the Dropbear SSH server. Its interesting to note that the server supports only the SSH protocol. Its possible that the hackers have used a command argument an assigned custom commands to route the infection commands to the running applications.
-
BrickerBot.2 – This is an advanced version of the malware. The reports indicate that it is able to execute more commands and the servers that spread the strain are hidden on the TOR anonymous network.
Such threats are not the usual type. The majority of the IoT viruses aim to install Trojan components or infiltrate the internal network. The BrickerBot malware intentionally destroys the affected devices. Depending on the products the commands may temporarily disable the device until the administrators reset them. In other cases the appliances cannot be recovered and have to be replaced. The identity of the hacker collective behind the BrickerBot malware is not known. There are two theories that are currently being investigated:
-
Malicious users wanting to raise awareness about the large number of vulnerable IoT devices. The attacks are made to warn device owners about other possible intrusions.
-
A hacker collective that aims to cause a wide sabotage attack on as many victims as possible.
As always we recommend that users utilize a trusted anti-spyware solution that can guard against viruses, payload droppers and other malware that can serve as sources of the infection.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



