Karmen Ransomware is a new HiddenTear based malware which can easily be removed by following our guide which explores both automatic and manual removal options.
Karmen Ransomware Description
Malware researchers have created a new malware strain which is called Karmen ransomware and is derived from the Hidden Tear family. Like other similar variants of the main code we pressume that these samples follow the usual behaviour patterns.
HiddenTear based ransomware are one of the most popular tools used by hackers in virtually all types of file manipulation intrusion attempts.
As the initial security analysis doesn’t show if there are any advanced modules added to the core encryption engine, we suspect that developers may include updates such as:
- Persistent Environment – The virus may modify the compromised host and install itself in a way which prevents manual removal.
- Additional Infection – The ransomware can be bundled with other payloads such as other malware, trojans and ransomware.
- Information Harvesting – The ransomware can be used to harvest important information from the infected computers.
- Remote Control – Improved versions of the Karmen ransomware can be used to gain remote control capabilities.
Upon infection the encryption engine is started which targets the most commonly used file type extensions. This includes files such as documents, photos, music, videos, configuration files, archives, databases and etc. All affected data receive the .grt extension.
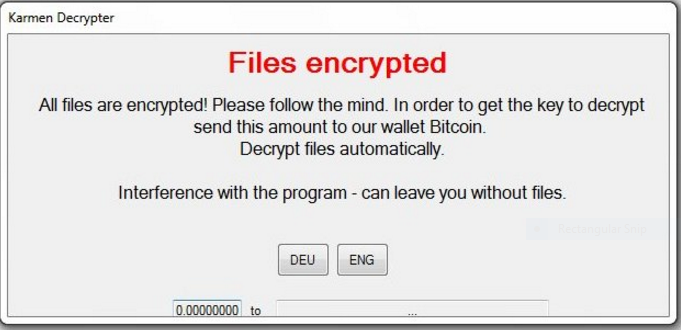
The following ransomware note is displayed to the victims once the encryption process is complete:
Files encrypted
All files are encrypted! Please follow the mind. In order to get the key to decrypt send this amount to our wallet Bitcoin.
Decrypt files automatically.
Interference with the program – can leave you without files.
DEU | ENG
There are several important characteristics that we must mention in regards to the Karmen Ransomware:
- The strains are used as a RaaS – RaaS (ransomware-as-a-service) platforms are used by hackers to construct effective attacks.
- Yet Another HiddenTear Variant – The hackers buy the core HiddenTear code and customize it to create new variants. This strain is merely an overhauled version of the malware family.
- No Fixed Ransomware Sum Request – The operators have not posted a fixed sum which is a popular tactic. The victims need to contact the hackers to obtain the necessary sum which is negotiated with them.
Analysis of the Karmen Ransomware
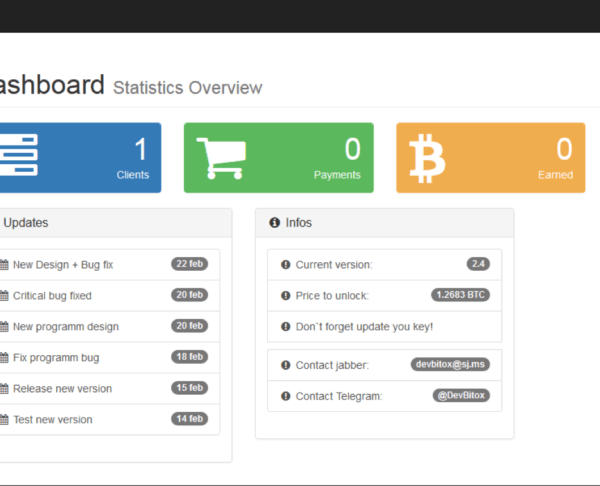
Malware researchers obtained several samples of the malware. The in-depth analysis showcased that the service specifically targets beginner criminals aiming to infect targets with a minimum amount of knowledge. Its easy to use graphical user interface is laid out in a friendly manner. The Karmen features a “Dashboard” display which allows the hackers to track the number of infected hosts via a “Clients” section. The panel shows the total earned revenue and also notifies of new malware versions.
The researchers discovered that its being sold as a package on various underground black markets for the price of <175 US Dollars. The buyers can customize the ransom sum and time counter for the payment window period themselves. The virus engine itself is multi-threaded and supports multiple languages. According to the available data it uses the .NET framework and the AES-256 encryption cipher. To use it the attackers must set up a machine running the MySQL database server along with a web server with PHP 5.6. Allegedly its developer is a hacker known as “DevBitox” who originates from a Russian-speaking country.
A distinct feature of the threat is that it can detect any running sandbox or debugging environments. The built-in stealth protection can automatically bypass running anti-virus protection engines or delete the virus if it is about to be detected. Furthermore the dashboard panel can be adapted to include additional functionality as it is adapted.
The encryption engine can automatically encrypt all local drives and attached removable storage devices. A predefined file type extensions list may be used to target a wide variety of user data – documents, photos, videos, configuration files, archives and etc.
The virus itself of a small size and can be attached to other files such as software installers. It is available in two versions – a “light” one which contains only the obfuscation and autoloader components and a more feature-rich “complete” iteration. The malware is programmed to automate its behavior by automatically deleting its loader and malware components when the ransomware sum is received from the victims.
According to several sources about 20 versions of the Karmen have been sold to various hackers or hacker collectives. At the moment the exact infection mechanism is not known.
Karmen Ransomware Distribution
The Karmen ransomware has seen only a limited number of samples. This does not give an accurate indication about the primary methods of infection. As such we pressume that the hackers employ the most widely used infection tactis:
- Email Spam Messages – A main method for virus delivery is the creation and management of phishing (social engineering) email campaigns. They utilize infected documents and messages which attract the users interest by posing as being sent from a legitimate sender: an individual, company or even government institutions. Recently the use of infected Microsoft Word and Excel files has become the major trend in distributing viruses like the Karmen ransomware. When they are opened an user prompt is shown which asks from the users to enable macros. They trigger a script which triggers the payload delivery to the host machine.
- Download Sites and P2P Networks – Criminal download sites or hacked ones can be used to distribute the virus strain. BitTorrent trackers are another popular option where the virus can be renamed as a popular software.
- Software Installer Bundles – The Karmen ransomware can be bundled with software installers of popular freeware or trial versions of well-known applications, games or utilities.
Summary of the Karmen Ransomware
| Name |
Karmen Ransomware |
| File Extensions |
.grt |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove Karmen Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Karmen Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Karmen Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Karmen Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Karmen Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Karmen Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



