DeriaLock ransomware is yet another malware strain found by the malware analysist at GData Karsten Hahn. It locks your screen by displaying a ransom note and requests a $30 ransom payment.
The article is dedicated to the threat’s specifics, its distribution, and its complete removal from the computer. Keep reading and stay safe!
| Name |
DeriaLock Ransomware |
Special Feature |
Screen Lock Function | Ransom |
$30 USD |
| Solution #1 |
Use the help of an anti-malware tool to remove DeriaLock ransomware and any additional cyber-security threats. |
|
Solution #2 |
DeriaLock ransomware can be removed manually. See the detailed tutorial below. This solution requires good computer skills. |
| Distribution |
Spam emails, malicious URLs, malicious attacments, exploit kits, freeware. |
DeriaLock Ransomware Features
DeriaLock ransomware family belongs to the screen lockers category. So upon infection DeriaLock doesn’t encrypt particular file types but prevent access to the system. The good news is that all files stay undamaged.
The Infection Progress
Once DeriaLock’s malicious payloads are running on the computer, the ransomware starts to collect information from the infected device. Then it generates an MD5 hash that supports its screen lock feature.
After creating the MD5 hash and checking it locally, DeriaLock ransomware is designed to connect its command and control (C&C) server and update itself to its latest version. If it finds a new version, the ransomware downloads the file and stores it in the following directory:
→C:\Users\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\StartUp\SystemLock.exe
The next step includes displaying its ransom note to a fullscreen window that locks the access to all files and applications. DeriaLock ransom note looks like this:
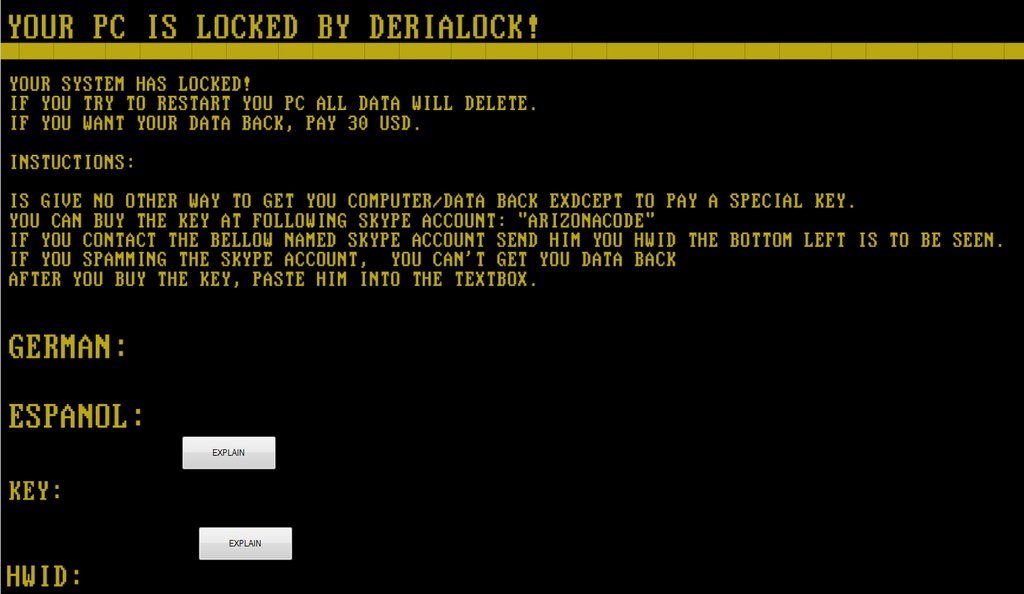
And the whole text on it reads:
”Your System has Locked!
If you try to restart you PC ALL data will delete.
If you want your data back, pay 30 USD.
Instuctions:
Is give no other way to get you computer/data back exdcept to pay a special Key.
You can buy the Key at the following Skype account: “arizonacode”.
If you contact the bellow named Skype account send him you HWID the bottom left is to be seen.
If you Spamming the skype account, you can’t get you data back
After you buy the key, paste him into the textbox.”
The researchers from BleepingComputer have reported that DeriaLock screen locker ransomware is programmed to shut down several essential Windows processes including:
This step is processed in order to prevent victims from closing the lock screen window.
DeriaLock Ransomware Distribution
So far it is not known which is the main distribution method that used by the DeriaLock ransomware. However, as the virus is contained in an infected binary file it would be logical to assume that it uses one of the following methods:
- Email Spam Campaigns – Computer hackers typically use botnets and compromised servers to spread malicious files, including malware samples that may include the DeriaLock ransomware via spam email campaigns. They typically use various social engineering tricks to make the target open the malicious files.
- Malicious Ads – Infected ad networks can host links to DeriaLock samples in links or directly in the ads themselves.
- Counterfeit Software Installers
– Many ransomware strains can be contacted from downloading fake software installers, updates or computer games from untrusted download sites or P2P networks like BitTorrent
Other sources of infection include browser hijackers, payload downloaders, etc.
Remove DeriaLock Ransomware
Unfortunately, pressing the the ALT + F4 buttons won’t close the screen locker. A popup displays the following message instead:
“I think that is a bad decision. Nice try mate =)”
By following the guide below you can get rid of this noxious infection.
DeriaLock Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete DeriaLock completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely DeriaLock Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



