Several new variants of the Android.Lockscreen ransomware have been identified, they use pseudorandom number generators to prevent the users from unlocking their device.
Android.Lockscreen Ransomware Makes a Comeback
The infamous Android.Lockscreen ransomware has been noticed to have evolved to several new iterations. The new malware versions use pseudorandom number generators which prevents victims from unlocking their devices without paying the ransom fee to the criminal operators.
The previous version of the threat used hardcoded passwords which were cracked by security engineers, thus rendering the ransomware ineffective. However the developers have created a new version that now combines a custom lockscreen along with the device’s own one to create additional difficulty for the users.
The Trojans are created directly on the mobile device upon infection which means that the complete code is not distributed via a vulnerability. This mechanism is used by hackers to evade detection by various security software solutions.
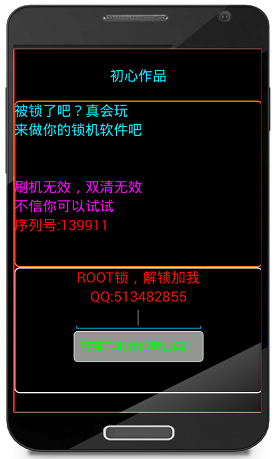
Upon infection the Android.Lockscreen ransomware creates a custom System Error window that is imposed on of every visible user interface element on the device. The older versions of the threat used a passcode to unlock the device. The newer variants use a random password, depending on the version it may be six-digit or eight-digit.
The generated key is different for every infected device as the base number is calculated using a random function command. In addition to creating this persistent addition to the ransomware code they have also added a function in the Trojan that changes the PIN of the regular Android lock screen.
All users are advised to keep their apps updated to the latest versions and not to download anything from unofficial sources, which are the most likely sources of infection. Good security practices advise everyone to keep all valuable files backed to a secure location to avoid infection by such threats.



