CryptoGod ransomware is a new iteration of the Hidden Tear malware that encrypts data with the .payforunlock extension. Our complete CryptoGod Ransomware removal guide will guide victims on restoring their computers and recovering all affected files.
Manual Removal Guide
Recover CryptoGod Ransomware Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does CryptoGod Ransomware Infiltrate the System?
According to the available research the hacker or hacker collective behind the CryptoGod ransomware originate from Italy. It is very likely that the first attack campaigns to target people located in the country before moving to a worldwide infection attack. The Hidden Tear malware family has seen thousands of variants and they all use varied strategies. In the case of the CryptoGod virus we suspect that the hackers are going to use the most popular and effective ones.
They include the use of email spam messages that contain social engineering tricks. The CryptoGod ransomware is attached to template emails that pose as being sent by legitimate and well-known companies or government institutions. The dangerous virus can be attached directly or linked in the body contents.
The hackers may also opt to include a payload code in infected office documents or software installers. The virus is downloaded when the computer users interact with the file. Some anti-virus products cannot effectively detect such infection attempts, this is why we advise everyone to use a quality anti-spyware solution.
Browser hijackers can be used to deliver the CryptoGod ransomware. They are malicious browser add-ons that seek to redirect the victims to a hacker-designated third-party site by changing the default home page, search engine and new tabs page. In addition they harvest sensitive information such as any stored account credentials, history, cookies, bookmarks, form data and etc.
The creation of counterfeit download sites and torrents is another way of distributing the virus. The hackers can rename the file to make it appear as another software.
Related: Skyname Ransomware, CerberTear Ransomware
Infection Flow of CryptoGod Ransomware
Malware experts discovered a newly constructed iteration based on the Hidden Tear core malware. It is known as the CryptoGod ransomware and it originates from a prior sample called “MoWare H.F.D”. It follows the same behavior patterns associated with most other viruses that are descendant from Hidden Tear.
Upon infection with the CryptoGod ransomware the malicious module automatically launches the encryption process. The captured samples encrypt file types based on a predefined list. The hackers extracted it from the captured CryptoGod ransomware:
.#vc, .$ac, ._vc, .00c, .07g, .07i, .08i, .09i, .09t, .10t, .11t, .123, .13t, .1pa, .1pe, .2011, .2012, .2013,
.2014, .2015, .2016, .2017, .210, .3dm, .3ds, .3g2, .3gp, .3me, .3pe, .500, .7z, .aac, .aaf, .ab4, .ac2,
.acc, .accd, .ach, .aci, .acm, .acr, .aep, .aepx, .aes, .aet, .afm, .ai, .aif, .amj, .as, .as3, .asc, .asf,
.asm, .asp, .asx, .ati, .avi, .back, .bak, .bat, .bay, .bc8, .bc9, .bd2, .bd3, .bgt, .bk2, .bkf, .bmp, .bpf,
.bpw, .brd, .brw, .btif, .bz2, .c, .cal, .cat, .cb, .cd, .cdf, .cdr, .cdt, .cdx, .cf8, .cf9, .cfdi, .cfp,
.cgm, .cgn, .ch, .chg, .cht, .clas, .clk, .cmd, .cmx, .cnt, .cntk, .coa, .cpp, .cpt, .cpw, .cpx, .crt, .cs,
.csl, .csr, .css, .csv, .cur, .cus, .d07, .dac,.dat, .db, .dbf, .dch, .dcr, .ddd, .dds, .defx, .der, .des,
.dgc, .dif, .dip, .djv, .djvu, .dng, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .drw, .ds4, .dsb, .dsf,
.dtau, .dtd, .dtl, .dwg, .dxf, .dxi, .ebc, .ebd, .ebq, .ec8, .efs, .efsl, .efx, .emd, .eml, .emp, .ens, .ent,
.epa, .epb, .eps, .eqb, .ert, .esk, .ess, .esv, .etq, .ets, .exp, .fa1, .fa2, .fca, .fcpa, .fcpr, .fcr, .fef,
.ffd, .fim, .fla, .flac, .flv, .fmv, .fon, .fpx, .frm, .fx0, .fx1, .fxr, .fxw, .fyc, .gdb, .gem, .gfi, .gif,
.gnc, .gpc, .gpg, .gsb, .gto, .gz, .h, .h10, .h11, .h12, .hbk, .hif, .hpp, .hsr, .html, .hts, .hwp, .i2b, .iban,
.ibd, .ico, .idml, .iff, .iif, .img, .imp, .indb, .indd, .indl, .indt, .ini, .int?, .intu, .inv, .inx, .ipe, .ipg, .itf,
.jar, .java, .jng, .jp2, .jpeg, .jpg, .js, .jsd, .jsda, .jsp, .kb7, .kd3, .kdc, .key, .kmo, .kmy, .lay, .lay6, .lcd, .ldc,
.ldf, .ldr, .let, .lgb, .lhr, .lid, .lin, .lld, .lmr,
.log, .lua, .lz, .m, .m10, .m11, .m12, .m14, .m15, .m16, .m3u, .m3u8, .m4a, .m4u, .m4v, .mac, .max, .mbsb, .md, .mda,
.mdb, .mdf, .mef, .mem, .met, .meta, .mhtm, .mid, .mkv,
.ml2, .ml9, .mlb, .mlc, .mmb, .mml, .mmw, .mn1, .mn2, .mn3, .mn4, .mn5, .mn6, .mn7, .mn8, .mn9, .mne, .mnp,
.mny, .mone, .mov, .mp2, .mp3, .mp4, .mpa, .mpe, .mpeg, .mpg, .mql, .mrq, .ms11, .msg, .mwi, .mws, .mx0,
.myd, .mye, .myi, .myox, .n43, .nap, .nd, .nef, .nl2, .nni, .npc, .nv, .nv2, .oab, .obi, .odb, .odc,
.odg, .odm, .odp, .ods, .odt, .oet, .ofc, .ofx, .old, .omf, .op, .orf, .ost, .otg, .otp, .ots, .ott,
.p08, .p12, .p7b, .p7c, .paq, .pas, .pat, .pcd, .pcif, .pct, .pcx, .pd6, .pdb, .pdd, .pdf, .pem, .per,
.pfb, .pfd, .pfx, .pg, .php, .pic, .pl, .plb, .pls, .plt, .pma, .pmd, .png, .pns, .por, .pot, .potm,
.potx, .pp4, .pp5, .ppam, .ppf, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptx, .pr0, .pr1, .pr2, .pr3, .pr4,
.pr5, .prel, .prf, .prn, .prpr, .ps, .psd, .psp, .pst, .ptb, .ptdb, .ptk, .ptx, .pvc, .pxa, .py, .q00,
.q01, .q06, .q07, .q08, .q09, .q43, .q98, .qb1, .qb20, .qba, .qbb, .qbi, .qbk, .qbm, .qbmb, .qbmd, .qbo,
.qbp, .qbr, .qbw, .qbx, .qby, .qbz, .qch, .qcow, .qdf, .qdfx, .qdt, .qel, .qem, .qfi, .qfx, .qif, .qix,
.qme, .qml, .qmt, .qmtf, .qnx, .qob, .qpb, .qpd, .qpg, .qph, .qpi, .qsd, .qsm, .qss, .qst, .qtx, .quic,
.quo, .qw5, .qwc, .qwmo, .qxf, .r3d, .ra, .raf, .rar, .raw, .rb, .rcs, .rda, .rdy, .reb, .rec, .resx,
.rif, .rm, .rpf, .rsspptm, .rtf, .rtp, .rw2, .rwl, .rz, .s12, .s7z, .saf, .saj, .say, .sba, .sbc, .sbd,
.sbf, .scd, .sch, .sct, .sdf, .sdy, .seam, .ses, .set, .shw, .sic, .skg, .sldm, .sldx, .slk, .slp, .sql,
.sqli, .sr2, .srf, .ssg, .stc, .std, .sti, .stm, .str, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw,
.t00, .t01, .t02, .t03, .t04, .t05, .t06, .t07, .t08, .t09, .t10, .t11, .t12, .t13, .t14, .t15, .t99,
.ta1, .ta2, .ta4, .ta5, .ta6, .ta8, .ta9, .tar, .tax, .tax0, .tax1, .tax2, .tb2, .tbk, .tbp, .tdr, .text,
.tfx, .tga, .tgz, .tif, .tiff, .tkr, .tlg, .tom, .tpl, .trm, .trn, .tt10, .tt11, .tt12, .tt13, .tt14, .tt15,
.tt20, .ttf, .txf, .txt, .u08, .u10, .u11, .u12, .uop, .uot, .v30, .vb, .vbpf, .vbs, .vcf, .vdf, .vdi, .vmb,
.vmdk, .vmx, .vnd, .vob, .vsd, .vyp, .vyr, .wac, .wav, .wb2, .wi, .wk1, .wk3, .wk4, .wks, .wma, .wmf, .wmv,
.wpd, .wpg, .wps, .x3f, .xaa, .xcf, .xeq, .xhtm, .xla, .xlam, .xlc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb,
.xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xpm, .xqx, .yuv, .zdb, .ziparc, .zipx, .zix, .zka
Effectively it targets a total of 666 extensions that include a wide range of file types: documents, archives, backups, music, photos, videos, configuration files and etc. All affected files are renamed with the .payforunlock extension.
The ransomware note is displayed through a lockscreen hosted in an application frame. It reads the following:
INFORMATION SECURITY
Your Personal Files has been Encrypted and Locked
Your documents, photos, databases and other important files have been encrypted with strongest
encryption and locked with unique key, generated for this computer.
Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you
pay and obtain the private key.Caution: Removing of CryptoGod will not restore access to your encrypted files.
Now you have the last chance to decrypt your files.
1. Buy Bitcoin (https://blockchain.info)
2. Send amount of 0.03 BTC to address: 1JC2xyroJXvtFtxW6s5fM89Dke5geqCAep
3. Transaction will take about 15-30 minutes to confirm.
4. When transaction is confirmed, send email to us at [email protected]
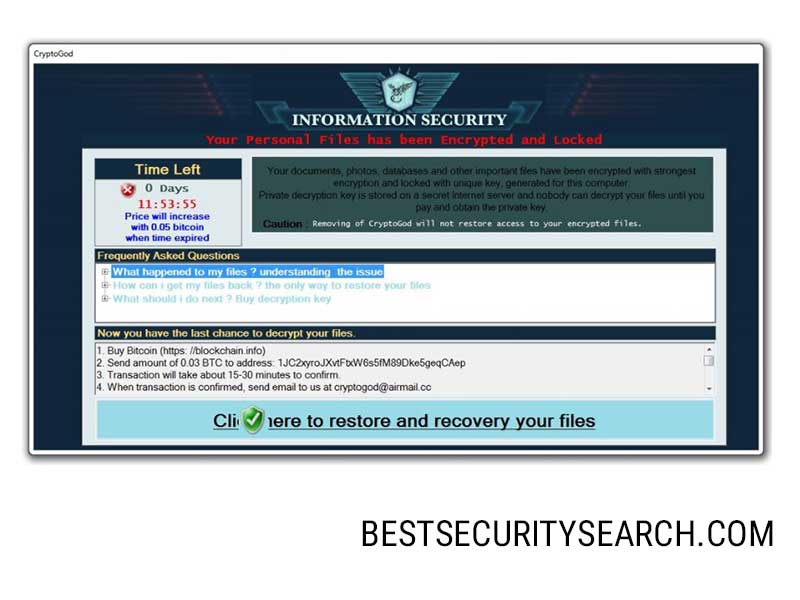
The lockscreen not only prohibits ordinary computer interaction and contains instructions on how the victims can pay the hackers for file decryption. We strongly advise all affected users not to pay them, as the transactions done through the Bitcoin digital currency cannot be traced. To restore infected computers users can use a quality anti-spyware solution in combination with a professional-grade data recovery product.
The hackers combine several different blackmail tactics:
- The ransomware sum is specified in Bitcoins. The initial sum is relatively low compared to other Hidden Tear samples. The hackers behind the CryptoGod ransomware demand 0.03 BTC which is equivalent to about 85 US Dollars.
- A short time limit is enforced. If the victims do not pay within the displayed time frame the price will increase with increments of 0.05 Bitcoins.
- The computer criminals behind the CryptoGod ransomware offer detailed information about the infection. Computer victims may be persuaded to pay the fee if they read the instructions or contact the hackers.
In addition the malware is able to conduct several system modifications. The CryptoGod virus engine can manipulate running processes via the Task manager and also execute arbitrary commands sent by the hackers. Combined with a ready-made network infrastructure can result in an effective Trojan ransomware.
The CryptoGod ransomware therefore can spy on the users, recruit the infected machines into a worldwide botnet and infect it with additional malware.
Remove CryptoGod Ransomware and Restore Data
WARNING! Manual removal of CryptoGod Ransomware requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
CryptoGod Ransomware – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover CryptoGod Ransomware Files
WARNING! All files and objects associated with CryptoGod Ransomware should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD CryptoGod Ransomware Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



