Mikoyan Ransomware encrypts sensitive user files, victims can recover their computers by following our removal guide.
Mikoyan Ransomware Description
The security community has reported the discovery of a new malware known as the Mikoyan ransomware. Its origins are not known, at the current moment the available information shows that it is most likely an independent creation. The virus has been compiled in the Visual Studio 2012 environment which supports a variety of programming languages – C, C++, VB.NET, C#, F# and TypeScript. We have received an indication that the ransomware is based on open-source code found on various online software repositories and communities.
Future updates of the ransomware may include the following additional modules:
- Keylogger – Future updates of the virus engine may include various forms of surveillance upon the victims. One of the most popular ways is to include a keylogger that is able to capture the input keystrokes and mouse movement.
- Remote Control – Another surveillance option includes the ability to initiate full remote control of the infected hosts.
- Data Stealing – The remote attackers can steal arbitrary data to their own servers by issuing commands to the virus engine.
- Botnet Recruitment – Infected computers can be recruited to a worldwide botnet that is being isedby the operators or rented out to other criminals.
- Additional Payload Delivery – The virus may be used to deliver other threats to the infected computer.
- Persistence – The engine may create a persistent state of execution which effectively prevents all manual removal attempts.
The limited quantity of the captured malware samples indicates that the Mikoyan ransomware may be still in an early testing stage. Right now the virus only has a basic encryption engine built-in as part of its core structure. Upon infection it starts to search and process a predefined list of target file type extensions with a strong encryption cipher. At the moment we don’t a copy of the list, however we assume that it targets the most commonly used data – archives, documents, photos, music, backups and etc. All of the affected data is received with the .MIKOYAN extension.
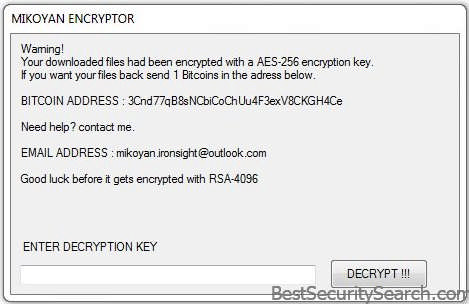
Once the encryption process is complete the engine enforces a screenlocker. It effectively prohibits the users from engaging in ordinary computer interaction until the threat is completely removed from the computer. It also displays hte ransomware note which reads the following message:
Warning!
Your downloaded files had been encrypted with a AES-256 enciyption key.
If you want your files back send 1 Btcoins in the adress below.
BITCOIN ADDRESS: 3Cnd77qB88NOiCoChUu4F3exV8CKGH4Ce
Need help? contact me.
EMAIL ADDRESS : [email protected]
Good luck before it gets encrypted with RSA-4096
ENTER DECRYPTION KEY
button [DECRYPT!!!]
From the ransomware note we can see that the hacker operator(s) demand a ransomware fee of one bitcoin. This is the equivalent of about 1523 US Dollars with today’s conversion rate. The use of a free email hosting service shows that the supplied address probably serves as a relay.
The current iteration of the Mikoyan ransomware affects only files found in the User’s “Downloads” folder. In addition to the encryption process the engine engages in several other malicious actions:
- Information Harvesting – The engine harvests sensitive information from the infected hosts such as the active computer name, its unique machine identifier and supported information. This data is used for both the generation of the unique victim ID.
- Windows Settings Modification – The Mikoyan ransomware is able to modify values used by the operating system. This may include essential components such as the Registry, boot options and etc.
- Uses The .NET runtime environment – The virus is written in a modern environment which requires the use of the .NET runtime.
Mikoyan Ransomware Distribution
Mikoyan ransomware is distributed as a single binary file bearing its name – MIKOYAN.exe. As the number of captured samples is low we suspect that the hackers are going to use the most popular methods:
- Email Spam Messages – The operator behind the Mikoyan ransomware create spam campaigns that use social engineering tricks designed to make the targets infect themselves with the malware. They may opt to attach the binary directly to the messages or link it in the body contents.
- Infected Documents – The hackers behind the virus create documents with embedded code. Once the targets open them a notification prompt is displayed. It asks the computer users to enable the built-in macros and if they agree the virus is downloaded from a remote server and started immediately.
- Software Installers – Ransomware as this one can be bundled with software installers that are usually distribute on hacked or hacker-controlled sites. The chosen software installers are usually of popular free or trial versions of applications, games, utilities, patches and etc.
- Hacker-controlled Sites and Malicious Scripts – Various hacked or hacker-controlled sites can pose as legitimate download portals or redirect the victims to the binary file. This category also includes the hacker-controlled ad networks which also generate income for their operators.
- Direct Intrusion Attempts – Hackers can use software frameworks to launch automated attacks that take advantage of older software installations. This is the reason why we recommend that users always use the latest version of all installed applications.
The first samples that are associated with the Mikoyan ransomware have been identified in the beginning of May 2017 and according to the limited information available it primarily targets English-speaking computer users. The various attack campaigns indicate that it is distributed globally and attempts to infect as many people as possible.
Summary of the Mikoyan Ransomware
| Name |
Mikoyan Ransomware |
| File Extensions |
.MIKOYAN |
| Ransom |
One Bitcoin |
| Easy Solution |
You can skip all steps and remove Mikoyan Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Mikoyan Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Mikoyan Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Mikoyan Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Mikoyan Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Mikoyan Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



