The Malabu ransomware is a virus threat which renames files with the .fucked extension, recover your files by reading our complete removal guide.
Malabu Ransomware Description
Computer security specialists detected a new unknown virus threat known as the Malabu ransomware. The captured samples are categorized as low-risk as they employ only the most basic features.
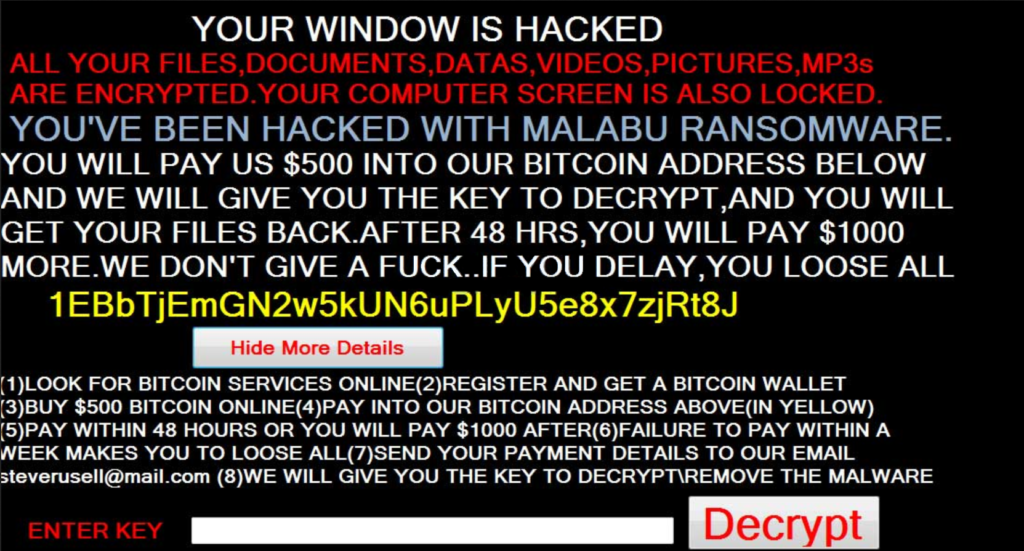
Upon infection it follows the basic patterns of encrypting a predefined list of target file type extensions. At the moment we don’t it extracted yet however we presume that it targets the most commonly used user data – documents, music, photos, videos, backups, configuration files, databases and etc. Once this is done the .fucked extension is used to mark the affected data. In addition the Malabu ransomware engine employs a screenlocker which prohibits ordinary computer interaction. The following ransomware message is shown to the victims:
YOUR WINDOW IS HACKED
ALL YOUR FILES, DOCUMENTS, DATAS, VIDEOS, PICTURES, MP3s ARE ENCRYPTED. YOUR COMPUTER SCREEN IS ALSO LOCKED.
YOU’VE BEEN HACKED WITH MALABU RANSOMWARE.
YOU WILL PAY US $500 INTO OUR BITCOIN ADDRESS BELOW AND WE WILL GIVE YOU THE KEY TO DECRYPT, AND YOU WILL GET YOUR FILES BACK. AFTER 48 HRS, YOU WILL PAY $1000 MORE. WE DON’T GIVE A FUCK.. IF YOU DELAY, YOU LOOSE ALL
1EBbTjEmGN2w5kUN6uPLyU5e8x7zjRt8J
[Hide More Details] (1) LOOK FOR BITCOIN SERVICES ONLINE
(2) REGISTER AND GET A BITCOIN WALLET
(3) BUY $500 BITCOIN ONLINE
(4) PAY INTO OUR BITCOIN ADDRESS ABOVE(IN YELLOW)
(5) PAY WITHIN 48 HOURS OR YOU WILL PAY $1000 AFTER
(6) FAILURE TO PAY WITHIN A WEEK MAKES YOU TO LOOSE ALL
(7) SEND YOUR PAYMENT DETAILS TO OUR EMAIL
[email protected]
(8) WE WILL GIVE YOU THE KEY TO DECRYPT \ REMOVE THE MALWARE
ENTER KEY [***] [Decrypt]
From the information available in the ransomware note we can see that the hackers request a ransomware fee of 500 US Dollars in Bitcoins. They use a free hosting provider which can be used as a redirect relay. This is an often used tactic used by hackers to mask their identity.
The malware analysts have found out that the virus engine uses static encryption keys which means that file recovery and the virus removal can be achieved by using a quality anti-spyware solution. The captured malware samples seem to be an early version of the virus. We expect to see an improved iteration in the near future.
Malabu Ransomware Distribution
The virus is distributed as a single executable file. As such it can be distributed easily via different means.
One of the primary methods is the use of spam email messages. The hackers organize and create emails by following predefined templates that employ phishing strategies. The criminals attempt to lure the victims into infecting themselves by sending them documents or links that may be of user interest such as bank documents, invoices, letters and etc. In recent times a popular strategy is to use crafted documents that contain malicious macros. When the victims open them they are presented with a prompt that asks them to enable the scripts. Once this is done the payload downloader is triggered which automatically infects the host machine.
In many other cases the virus can be bundled in software installers. They are usually freeware or trial versions of popular software such as applications, games, updates or patches. They are distributed on hacked or hacker-controlled download sites as well as P2P networks like BitTorrent trackers. Security experts advise all computer users to download software only from their official sources to avoid the risk of getting infected.
Depending on the attack campaign the hackers can also use other methods to spread the virus such as sending spam messages over messaging apps such as Viber and Snapchat. Fake profiles on social media platforms like Facebook can also lead to a virus infection.
Direct hacker attacks are another infection method. The hackers attempt to find vulnerabilities often by using exploits on the installed applications.
Summary of the Malabu Ransomware
| Name |
Malabu Ransomware |
| File Extensions |
.fucked |
| Ransom |
500 US Dollars in Bitcoins |
| Easy Solution |
You can skip all steps and remove Malabu Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Malabu Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Malabu Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Malabu Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Malabu Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Malabu Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



