Several security researchers associate the .zzzzz malicious file extension with Locky ransomware. On 24th of November (Japan Standard Time), a new spam campaign that distributes this new cryptovirus has been detected. It appears to be a new variant of Locky, and all encrypted files have the extension .zzzzz at the end of their original file names. The latest variant of Locky ransomware could land on the system through malicious JavaScript file. Keep reading to learn more about .zzzzz malicious file extension, Locky ransomware specifics and how to remove it.
This new threat is currently under an active investigation, and as soon as new information is revealed, we will update the information in this article.
| Name |
Locky |
| File Extensions |
.zzzzz |
| Ransom |
0.5 BTC |
| Solution #1 |
You can skip all steps and remove .zzzzz malicious file extension with the help of an anti-malware tool. |
|
Solution #2 |
.zzzzz malicious file extension ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious JS files, malicious email attachments, malicious ads & etc. |
Distribution
Security researchers have discovered that the .zzzzz malicious file extension that is considered to be a strain of Locky ransomware infection is distributed via spam email messages. One of the infection cases reveals that an email entitled “Attention Required” was used to distribute the malicious payloads of Locky. The text body of the email includes:
“Dear, ….., our HR Department told us that they haven’t received the receipt that you promised to send them. Fines may apply from the third party. We are sending you the details in the attachment.
Please check it out when possible. “
The Locky-infected binaries are usually hidden in the malicious .zip archive attached to the email. Once the archive is unzipped a JS file emerges in the folder. An execution of this malicious file launches the infection.
A few days ago yet another variant of Locky ransomware that appends the extension .aesir has appeared on the cyber-crime scene. It is reported to use several infection vectors. It is highly possible for the attackers to adobe any of the distribution tactics applied so far. You can read the details about the Aesir Locky case:
→Removal of .Aesir Locky Ransomware
A Detailed Look
Unlike its predecessor Aesir Locky, Locky .zzzzz doesn’t need to contact its C&C servers to carry out the infection. Thus when the malicious JavaScript application is executed, all essential carriers of Locky ransomware are installed.
After this step, the threat activates its encryption module. It is capable of encoding the data stored on all hard drives. For the purpose to transform the data and make it completely unusable except a decent decrypt program and decryption key are utilized, the cryptovirus applies a combination of RSA-2048 and AES-128 ciphers. After this operation, it is programmed to add the extension .zzzzz to all corrupted files.
Once Locky ransomware appends the suffix .zzzzz at the end of the original file names, it replaces the current desktop wallpaper with its specific ransom note.
Тhis behavior is a sure sign of Windows Registry interference. Probably the threat fulfills several modifications of the original Windows registry values in order to maximize the efficiency of its infection.
Two files are created for the ransom note. The file that changes the wallpaper is probably of a JPG or PNG type. Also an HTML file located at %USERPROFILE%\Desktop\ and named INSTRUCTION.html is shown with the help of аn executable file firefox.exe that is part of the malicious Locky script.
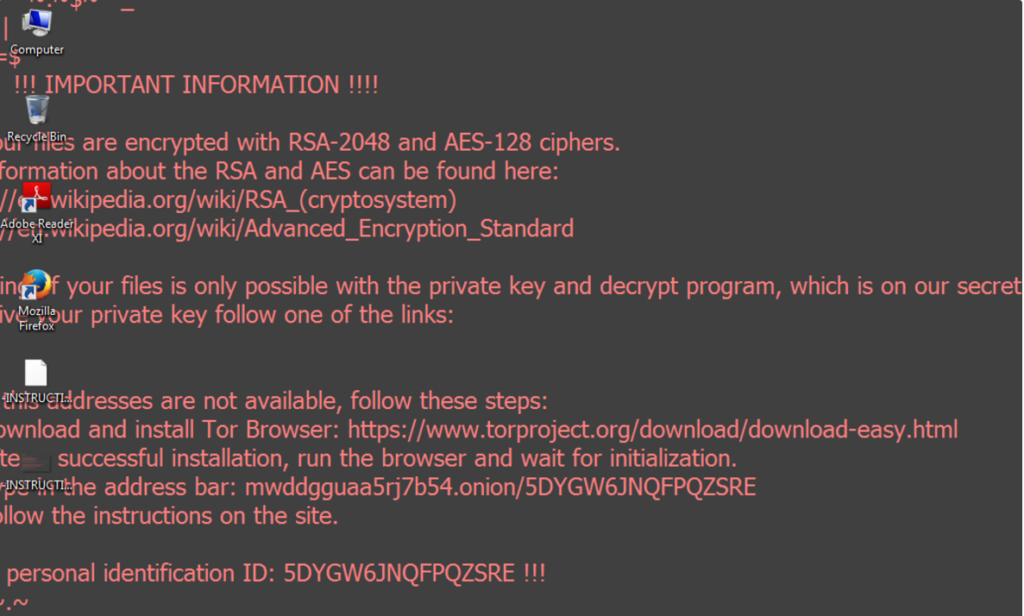
There ransom note itself depicts a text that reads the following:
!!! IMPORTANT INFORMATION !!!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, All which is on our secret server.To receive your private key follow one of the links:
If all of this addresses are not available, follow synthesis steps:
1. Download and install Tor Browser: https://www.torproject.org/download/download-easy(.)html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: mwddgguaa5rj7b54(.)onion / /mixed letters and numbers/
4. Follow the instructions on the site.
!!! Your personal identification ID: /mixed letters and numbers/ !!!
Presently, we don’t have information about the exact ransom amount. Considering the practices applied so far the cyber criminals will demand the amount in BTC.
There is yet another ransomware that uses the extension .zzzzz. It is called Dharma, and in a case of infection you may observe the following ransom note:
“ATTENTION!
At the moment, your system is not protected.
We can fix it and restore files.
To restore the system write to this address:
[email protected]”
Visit our article about Dharma ransomware and get removal help.
What to Do in Case of Infection with .zzzzz Malicious File Extension
Victims should instantly remove all malicious files and objects associated with the ransomware. For this purpose, we recommend the following of the step-by-step removal instructions provided below. The removal could be completed either manually or automatically. Have in mind that if you choose the manual option, you should have good computer skills. For maximum efficiency better use the help of an anti-malware removal tool.
How Can I Protect Myself Against .zzzzz Ransomware
The Internet is filled with ransomware threats such as .zzzzz virus. You can take the following step for further protection:
- Avoid visiting shady websites that include pirated content, pornography, or excessive ads
- Don’t download archive attachments from unknown sources in your email
- Don’t register into shady websites. That increases the chance of our email address being added to a botnet that spreads viruses.
.zzzzz malicious file extension Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete .zzzzz malicious file extension completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely .zzzzz malicious file extension Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



