The Takahiro Locker Ransomware is a new malware threat from Japan that targets various types of users, learn how to remove it from our article.
| Name |
Takahiro Loader Ransomware |
| File Extensions |
Depends on the variant |
| Ransom |
3 Bitcoins |
| Solution #1 |
Takahiro Locker Ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
|
Solution #2 |
Takahiro Locker Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam email campaigns, infected software bundles, browser hijackers and malicious ads. |
Takahiro Locker Ransomware Description
The Takahiro Locker ransomware has recently been spotted by security researchers and is one of the newest malware that have a ransom note written in a language other than English. Despite the fact that the instructions are in Japanese, there have been a variety of campaigns that deliver the threat in countries other than Japan.
Takahiro Loader has a rather long initialization process in comparison to other threats by following a sequence of commands. The first thing that it does is to create a new folder in the %User Temp%\Google\Chrome location where the ransomware copies itself as the Update.exe binary. This is made to fool the users into thinking that its an update for the Google Chrome web browser. Two registry entries are also added to the Windows registry:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run Google Chrome Update Check = %User Temp%\Google\Chrome\Update.exe
- HKEY_CURRENT_USER\Software\Google\Update\SEND SENDING = [random address]
The first registry entry creates an auto-start mechanism in the Windows operating system, making the ransomware execute upon every boot of the system. The second entry is probably a variable address to which harvested information about the infected machines are send.
The actual start of the encryption process is started when a notification message displaying the “WARNING RUNNING KILL ME!” text. This step has been placed by the hackers to scare the users while the ransomware has locked its process and has started to encrypt the target victim files. The affected data are the most popular documents and audio & videos. As of today we do not have the complete list yet yet. Some of the following extensions are affected:
txt, .jpg, .png, .bmp, .zip, .rar, .torrent, .7z, .sql, .pdf, .tar, .mp3, .mp4, .flv, .lnk, .html, .php
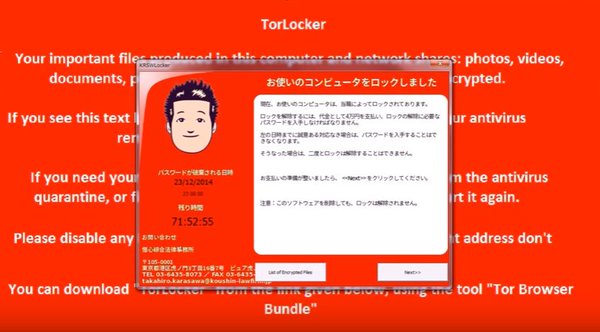
When the encryption process has completed another notification screen is displayed which shows the ransom note in Japanese. A rough translation of it reads the following:
Hello,
this is Tang, a Lawyer.
You have made an illegal file transfer, so I have locked your PC.
To unlock your files, you need to pay 3 Bitcoins within 3 days.
You need to have 30,000 Japanese Yen, to transfer them to Bitcoins and send them to me.
If you don’t pay within 3 days, the key for decryption will be deleted from where the server is stored and the data of your PC can no longer be returned.
Click the button “Next”.
Like other ransomware variants the hackers request the sum of 3 Bitcoins which is unusually high for a typical ransomware strain. A time limit of 3 days is also imposed on the user to try to extort them into paying the sum.
What’s interesting about the Takahiro Locker ransomware is that it does not damage files found in the following locations:
- Windows
- Steam
- Origin
- Program Files
- Recycle Bin
In addition the ransomware deletes all Shadow Volume Copies from the Windows operating system to prevent file restoration.
Takahiro Locker Ransomware Distribution
The Takahiro Locker ransomware is delivered as a single binary executable file using various methods. One of the most popular distribution techniques is through spam email campaigns. They bear the ransomware either as a malicious link or directly as attached to the messages. The hackers usually employ social engineering tricks to make the victims to start the file.
The Takahiro Locker ransomware can also compromise victim systems through infected software bundles from untrusted web sites or P2P networks, as well as served through malicious ads.
Takahiro Loader Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete Takahiro Loader completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Takahiro Loader Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



