A survey conducted by cyber security researchers from Cyber Ark shows that a lot of system administrators do not adhere to good security practices and basic password protection instructions.
The Cyber Ark Security Survey Shows How System Administrators Handle Passwords
The report is the result of a series of surveys conducted with 750 IT and IT security decision makers from around the world. This includes C-level executives, directors and heads of departments among enterprise organizations. The respondents represent both public and private organizations across multiple industries from Europe, the US, Israel and Asia Pacific.
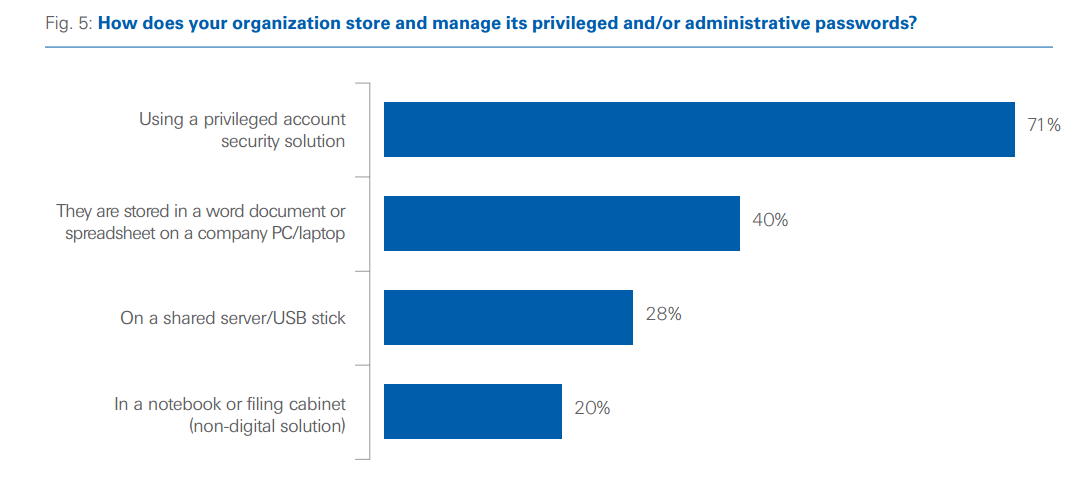
The results show that 40% of all surveyed organizations store critical or admin passwords in Word documents, spreadsheets or other Office files on company computers. And 28% use shared servers or USB sticks. This is a serious concern as IT security policies prohibit these practices for the sake of better protection against hacker attacks.
The report gives valuable insight on how these companies handle risk and threat response. The top changes implemented after mass public awareness of security issues are related to malware detection and endpoint protection measures. 71& of all respondents state that they have increased their perimeter security budget for purchasing and implementing solutions such as firewalls, intrusion detection software, anti-virus packages, and other tools.
The most difficult type of attack to mitigate is the malware installation which includes all popular variants – ransomware, Trojans, and viruses. Companies are worried about DDOS attacks; they believe they are the number one concern for the next year.
According to the respondents, the most potentially catastrophic event is related to cyber attacks that target financial systems and issues that disrupt the global stock markets.
The biggest concern for the organizations are the safeguarding of the customer data, nearly seven in ten surveyed responses have placed this as a top priority.
The top three priorities when a cyber attack has occurred are the following:
- Stopping the breach and removing the attackers
- Detecting the source of the breach
- Updating IT security to prevent the same breach from occurring again
For more information and to read the whole report navigate to Cyber Ark’s survey page.