The Windows Registry is a hierarchically structured database that stores low-level settings for Microsoft Windows OS and for applications that utilize the Registry in order to work properly. Whenever a new program is installed, a new subkey is added to the Windows Registry. The subkey contains information about program’s version, its location, and settings how to start the program. The Windows Registry has two essential elements called “keys” and “values”. The Registry keys are container objects similar to folders while the values are non-container objects similar to files.
Generally once activated on the computer unwanted software or malware modify the entries in the Windows Registry Editor. The changes may have low-impact on the system like changed appearance of the desktop wallpaper, screensaver and added buttons in the drop-down menus. However, some changes may expose the whole system at stake and result in system disruption.
The most frequently used registry keys you can see when you open the Windows Registry Editor are:
- HKEY_LOCAL_MACHINE or HKLM – This key contains specific information about the type of the software, hardware and other preferences for your computer. All users on a given computer who log on the system use this information.
- HKEY_CLASSES_ROOT or HKCR – This key is for all your windows shortcuts and the core aspects of the Windows user interface.
- HKEY_USERS or HKU – This key collects all information about the preferences of each user who has a login account for a given computer. Each user is identified in a SID subkey under the main key.
- HKEY_CURRENT_USER or HKCU – This key contains information about the login names, Start menu settings, and desktop settings of the currently logged on user.
Let’s guess that a malicious process has set a module “virus.exe” in %AllUsers% profile directory. Then you could observe the following registry entry in the Windows Registry:
→HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\”cry” = “%AllUsers%\virus.exe”
Each value in the keys performs a different function from the other values. For its malicious purposes, the unwanted application or the malware can modify the current Windows values or create new values.
In this article, we aim to show you how to fix Windows Registry errors caused by unwanted applications and malware. Once you’re ready, all adverse effects should be gone. Please have in mind that making changes in the Windows Registry Editor is a tricky process. Using the Windows Registry Editor inaccurately can cause serious problems requiring the reinstallation of your OS.
Note!
You should first remove the unwanted program or the malware from your computer. It is not recommended to clean the registries without getting rid of the viruses that modify and create them. You could use an advanced anti-malware tool for the best results. It can detect and fix all malicious registry entries automatically.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Repair Corrupted Windows Registry by Resetting Permissions
You can manually fix your Windows Registry by resetting permissions by following the steps below.
STEP I: Back up Your Data.
As we mentioned an error during the Registry cleanup process can have a serious impact on the whole system, especially if it’s infected. Before we begin, our advice is to backup all your data. For this purpose, you can use USB, external drive, Memory Stick, etc. Other options are using cloud platform and using Windows Backup in the Control Panel.
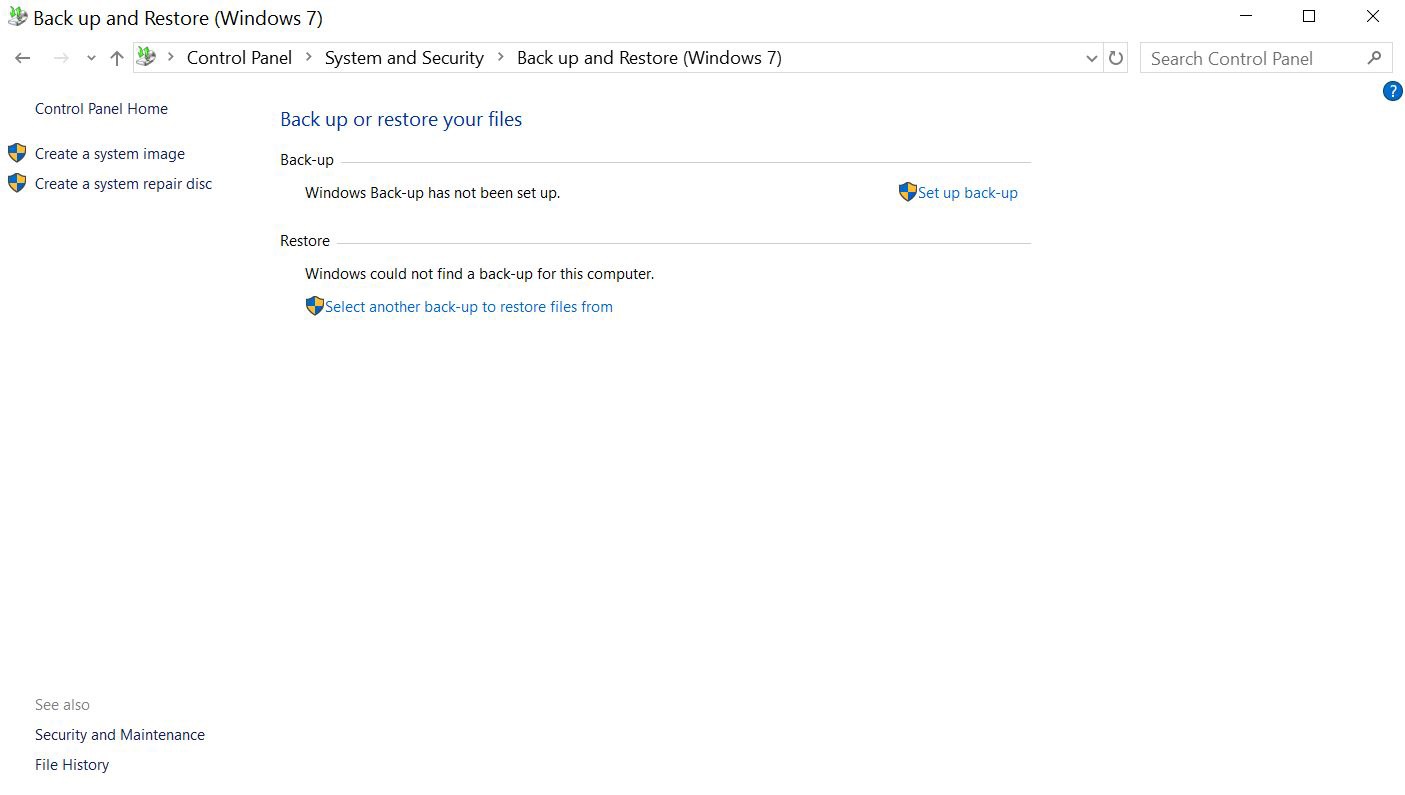
STEP II: Back up the Data of the Current Windows Registry Entries.
-
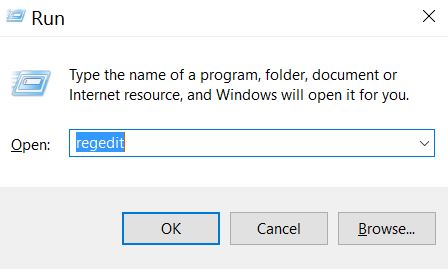
1) Press Windows button + R to open the Run dialog box

- 2) In the field type “regedit”
- 3) When the Registry Editor appears go to File drop-down menu
4) Then choose “Export..” option
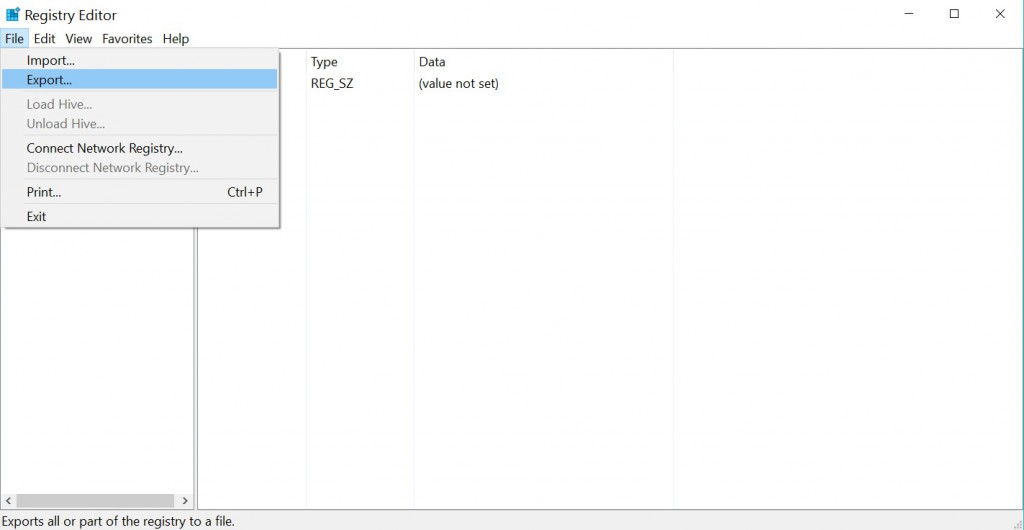
- 5) Select a location and a name for the backup and save it. We will name our “preventivemeasure.reg”.
STEP III: Download and Install SubInACL Provided by Microsoft to Reset Registry Permissions.
-
1) Download SubInACL.
Download link for SubInACL provided by Microsoft
-
2) Install SuInACL in the default directory.
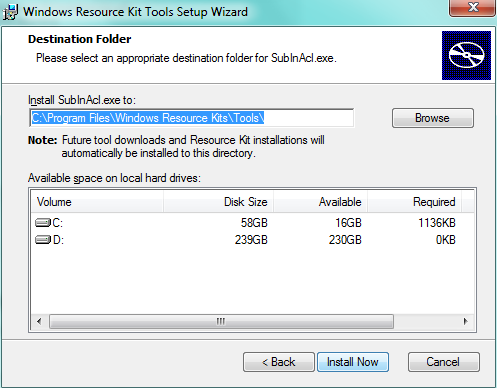
STEP IV: Make Registry Fixing Script.
-
1) We need to make a .txt file. Press Windows button and start typing Notepad. Then click the app to open it. Paste the following script in the text document:
subinacl /subkeyreg HKEY_CURRENT_USER /setowner=Administrators
subinacl /subkeyreg HKEY_CLASSES_ROOT /setowner=Administrators
subinacl /subdirectories %SystemDrive% /setowner=Administrators
subinacl /subkeyreg HKEY_LOCAL_MACHINE /grant=system=f
subinacl /subkeyreg HKEY_CURRENT_USER /grant=system=f
subinacl /subkeyreg HKEY_CLASSES_ROOT /grant=system=f
subinacl /subdirectories %SystemDrive% /grant=system=f
-
2) Save the file as a .bat file. Click on File drop-down menu and select “Save As…” option.
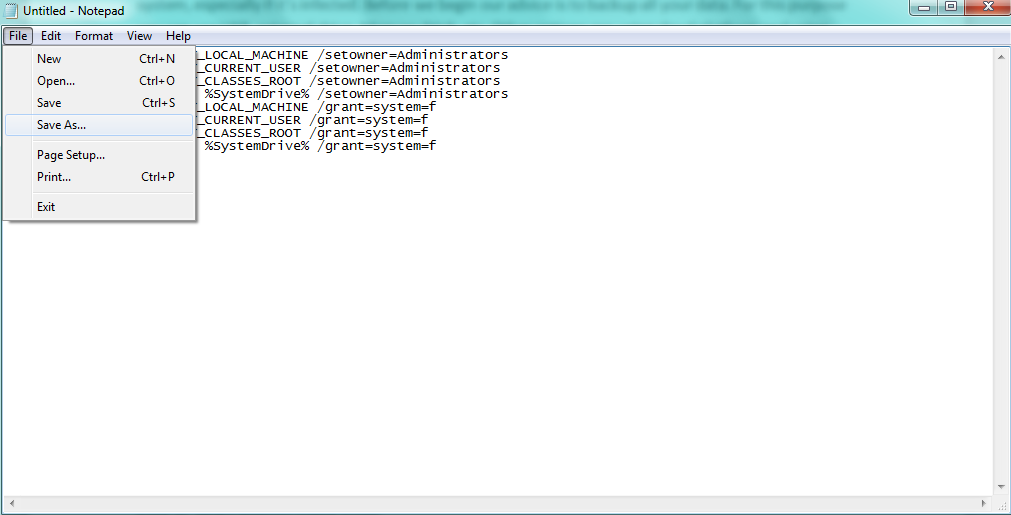
- Then select find “Safe as type” option and choose “All Files” instead of “Text Documents(*.txt)“. In the field for the file name type “fix.bat” and save it in “C:\Program files\Windows Resource Kits\Tools”.
STEP V: Clean up Your Registries.
-
1) Press “Windows button” and start typing “Command Prompt“. Right-click on it and choose “Run as Administrator“.
2) In the Command Prompt window type one of those two commands and press “Enter“:
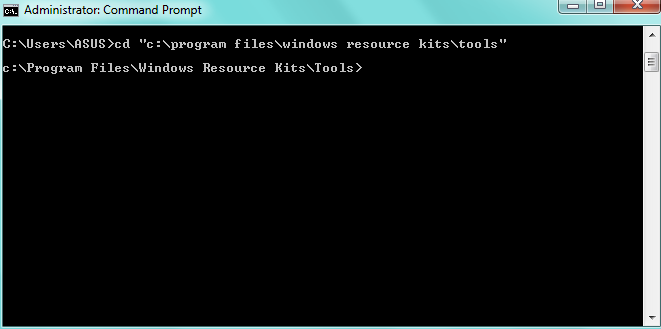
→cd “C:\Program Files\Windows Resource Kits\Tools” or
cd “C:\Program Files (x86)\Windows Resource Kits\Tools”
-
Your choice depends on where the “Windows Resource Kits” folder is located.
In our situation, it is in Program Files. Then, you should see the following:
-
3) Now type “fix.bat” and press “Enter“.
Once the cleanup is ready, all your registry permissions will be restored back to normal. You should also see a report of how many registries have failed or contained syntax errors.



