Experts discovered a new malware known as RanRan which is attacking Middle Eastern government structures, read our removal guide for more information.
RanRan Ransomware Description
Computer security experts discovered a new ransomware known as RanRan which has been used in several attack campaigns against governments from Middle Eastern countries. According to the initial security analysis its code stems down from a previously unknown ransomware family. It is very possible that this current iteration has been used in other related attack which are still undetected.
The virus’s name comes after the security researchers discovered the title in several of the embedded strings. The ransomware itself is not very sophisticated according to the code analysis. The malware authors have made a number of mistakes which have allowed the security experts to create a script which decrypts some of the files.
Upon infection it creates a process which which runs as mutually exclusive file. This allows only a single instance running at once, such programming designs are typical for simpler threats.
The virus copies itself to the “C:\services.exe” file. To attain persistence on the host system it creates an autorun key which is base64 encoded with the following value:
TlFRICJVWFBIXEZCU0dKTkVSXFp2cGViZmJzZ1xKdmFx
YmpmIEFHXFBoZWVyYWdJcmVmdmJhXEp2YXFiamYiIC9zIC9pIFlibnEgL2cgRVJUX0ZNIC9xIA==
The payload is then decoded and a routine that adds or subtract 13 from each alpha character. A registry key is then added which executes the virus when the computer boots.
The most important thing is that the ransomware code features stealth protection by monitoring for applications that contain the string “task manager”.
In addition the code looks out for the following processes which are also shut down by the virus’s engine:
- MSSQLSERVER
- SQLWriter
- MSSQL$CONTOSO1
- SQLServerAgent
- MSSQL$SQLEXPRESS
- Microsoft Exchange Information Store
- OracleASMService+ASM
- OracleCSService
- OracleServiceORCL
- OracleOraDb10g_home1TNSListener
- usermanager
- outlook
- exchange
- sql
Such functions are built-in to stop the services and applications which execute various actions on databases and frequently used user data. By disabling them the RanRan Ransomware can increase the number of files it has affected.
The following target file extensions are affected by the encryption engine (which uses the AES-128 cipher):
.mdf, .ldf, .edb, .pst, .ost, .doc, .docx, .pdf, .xls, .xlsx, .ppt, .pps,
.pptx, .ppsx, .accdb, .mdb, .zip, .rar, .txt, .jpg, .bad, .epf, .bdp, .efp,
.vsd, .mpp, .xlt, .cmd, .lic, .me, .xlsm, .war, .bdr, .stm, .sdb, .psd, .eml,
.vdw, .vdx, .tar, .csv, .max, .png, .ai, .dwg, .dxf, .7z, .c, .cpp, .bak, .ese,
.ashx, .asmx, .soap, .svc, .bkf, .issue, .sql, .fmb, .olb, .java, .webm, .mkv,
.flv, .dbf, .mtb, .asp, .aspx, .sln, .cs, .jar, .bmp, .iso, .resx, .exe, .tar,
.dat, .rtf, .img, .gz, .vmdk, .log, .ace, .kdbx, .rdp, .psc, .bat, .cfg, .rmvb,
.3gp, .swf, .ipdb, .db, .cmsc, .kmz, .edx
The file list showcases that the virus affects some of the most commonly used data such as Microsoft Office documents, PDF files, images, daabases, archives, backups and etc.
Its interesting to note that there are two separate encryption mechanisms employed by the RanRan ransomware:
- Supplied RSA Public Key – If the attackers have supplied an RSA public key in the C:\pubkey file then it will be used to encrypt the user files.
- Built-in MD5 Hash Encryption – If a public key is not found the RanRan ransomware encrypts the files using the md5 hash of the following string – aaoy09aaqqq@#433dd56fdfdf$Fss45*ss.
A randomly generated string is crafted in a file named C:\WINDOWS\pass. The value is used as the RC4 password. Based on the filesize of the individually affected files a new password is generated for the following groups:
- 0 – 5 MB
- 5 – 30 MB
- 30 – 100 MB
- 100 – 300 MB
- 300 – 700 MB
- 700 – 2000 MB
- 2000 – 3000 MB
- 3000 MB and greater
After each encryption stage the used key is encrypted using the supplied RSA public key. It is then written using the following pattern:
VictemKey_[lower_bound]_[upper_bound]
The [lower_bound} value shows the lowest file size of the group, while the [upper_bound] is the upper file size.
As such the following types of files are generated:
- VictemKey_0_5
- VictemKey_5_30
- VictemKey_30_100
- VictemKey_100_300
- VictemKey_300_700
- VictemKey_700_2000
- VictemKey_2000_3000
- VictemKey_3000
During the encryption phase the files are renamed with the .zXz extension. After the process is complete for all files the virus display the ransom note crafed in a zXz.html document which has the following contents:
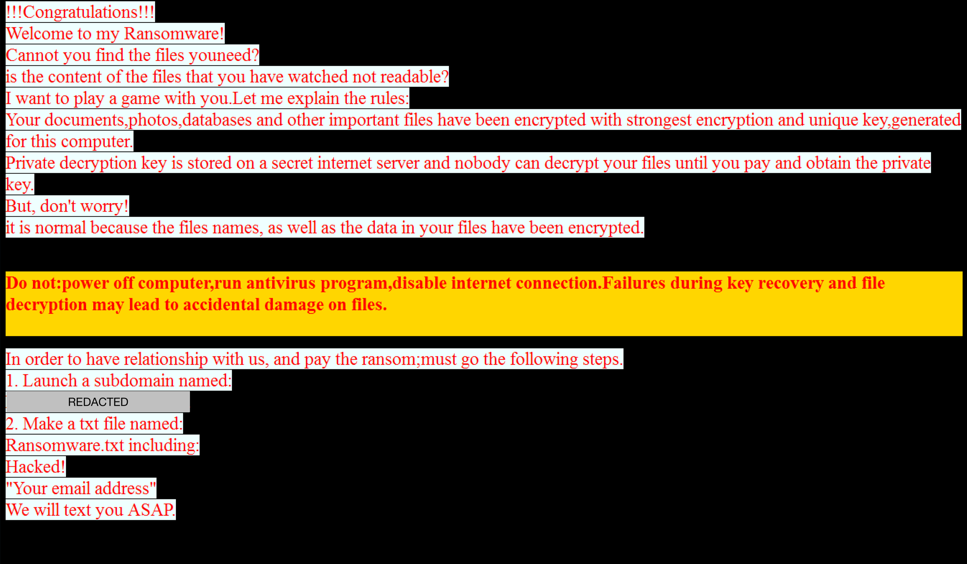
!!!Congratulations!!!
Welcome to my Ransomware!
Cannot you find the fies youneed?
is the content of the files that you have watched not readable?
I want to play a game with you. Let me explain the rules:
Your documents, photos, databases and other important files have been encrypted
with strongest encryption and unique key generated for this computer.
Private decryption key is stored on a secret internet server and nobody can decrypt
your files until you pay and obtain the private key.
But, don’t worry!
It is normal because the file, names as well the data in your files have been encrypted.Do no: power off compuer, run antivirus program ,disable internet connection. Failures during key recovery
and file decryption may lead to accidental damage on files.In order to have relationship with us, and pay the ransom; must go the following steps:
1. Launch a subdomain named:
XXXXXXXXXXXXXXXXXXXXXXXXXXXX
2. Make atxt file named:
ransomware.txt including:
Hacked!
“Your email address”
We will text you ASAP.
From the ransomware note and the displayed behavior we can assume that the following facts are true:
- Like other similar malware families it does not quote a fixed ransomware payment sum. Instead it asks the victims to contact the operators directly. This tactic is often used by more advanced forms of ransomware as the operators can “judge” the price of the affected data.
- A rather interesting fact is that the hackers demand from the victims to create a subdomain with a politically-inclined name. According to the experts this also forces the users to publicly announce that they have been hacked.
- It appears that the RanRan ransomware has used open-source and freely available code in its encryption module.
RanRan Ransomware Distribution
The fact that the virus was detected in a series of attacks against government organizations from the Middle East shows that this is the primary means of infections. At the time of writing this article we have not received news of a major outbreak using another infection strategy.
The hackers have used a wide variety of infection tactics to infiltrate the target systems. Some of the frequently used methods include the following:
- Exploit Kits & Direct Attacks – The use of exploit kits and automated vulnerability testing toolkits that directly attack the systems looking for any unpatched software and services.
- Phishing Scams – Email spam messages that pose as originating from legitimate sources are a primary method of infection. In this case the messages might be infected documents that include dangerous scripts that redirect to a malicious download site or download the payload directly.
- Online Scripts – Dangerous scripts like browser hijackers and ad networks can cause virus infections. The browser hijackers modify the default home page, new tabs and search engine of the installed web browsers (Mozilla Firefox, Google Chrome and Internet Explorer).
Summary of the RanRan Ransomware
| Name |
RanRan ransomware |
| File Extensions |
VictemKey_[lower_bound]_[upper_bound] Pattern |
| Ransom |
1 Bitcoin |
| Easy Solution |
You can skip all steps and remove RanRan ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
RanRan ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
RanRan ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely RanRan ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore RanRan Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



