The NM4 ransomware is a new malware threat derived from the R malware that can be deleted by following our complete removal guide.
NM4 Ransomware Description
NM4 ransomware is a newly discovered malware threat which has been identified as a strain of the R virus. It is made by unknown hackers that have modified the core threat and created a virus that is now classified as a strain.
The virus uses an encryption engine equipped with the AES-256 and RSA-2048 ciphers to encrypt target user files. Like other similar threats it uses a built-in list that contains the target file type extensions. At the moment we don’t have access to it however we assue that it targets the most popular files – documents, music, photos, videos, archives, backups and etc.
When this process is complete the virus creates a ransomware note in a Recovers your files.html file. It contains the following message to the victims:
Your Key: ***
Encrypted files!
All your files are encrypted.Using AES256-bit encryption and RSA-2048-bit encryption.
Making it impossible to recover files without the correct private key.
If you are interested in getting is the key and recover your files
You should proceed with the following steps.
The only way to decrypt your files safely is to buy the Descrypt and Private Key software.
Any attempts to restore your files with the third-party software will be fatal for your files!
To proceed with the purchase you must access one of the link below
• xxxxs://3fprihycwetwk2m7.onion.to/
• xxxxs://3fprihycwetwk2m7.onion.link/
If neither of the links is online for a long period of time, there is another way to open it, you should install the Tor Browser
If your personal page is not available for a long period there is another way to open your personal page – installation and use of Tor Browser:
1. run your Internet browser (if you do not know what it is run the Internet Explorer);
2. enter or copy the address https://www.torproject.org/download/download-easy.html.en into the address bar of your browser and press ENTER;
3. wait for the site loading;
4. on the site you will be offered to download Tor Browser; download and run it, follow the installation instructions, wait until the installation is completed;
5. run Tor Browser;
6. connect with the button ‘Connect’ (if you use the English version);
7. a normal Internet browser window will be opened after the initialization;
8. type or copy the address xxxxs://3fprihycwetwk2m7.onion in this browser address bar;
9. press ENTER;
10. the site should be loaded; if for some reason the site is not loading wait for a moment and try again.
If you have any problems during installation or use of Tor Browser, please, visit xxxxs://www.youtube.com and type request in the search bar ‘Install Tor Browser Windows’ and you will find a lot of training videos about Tor Browser installation and use.
Your Key: ***
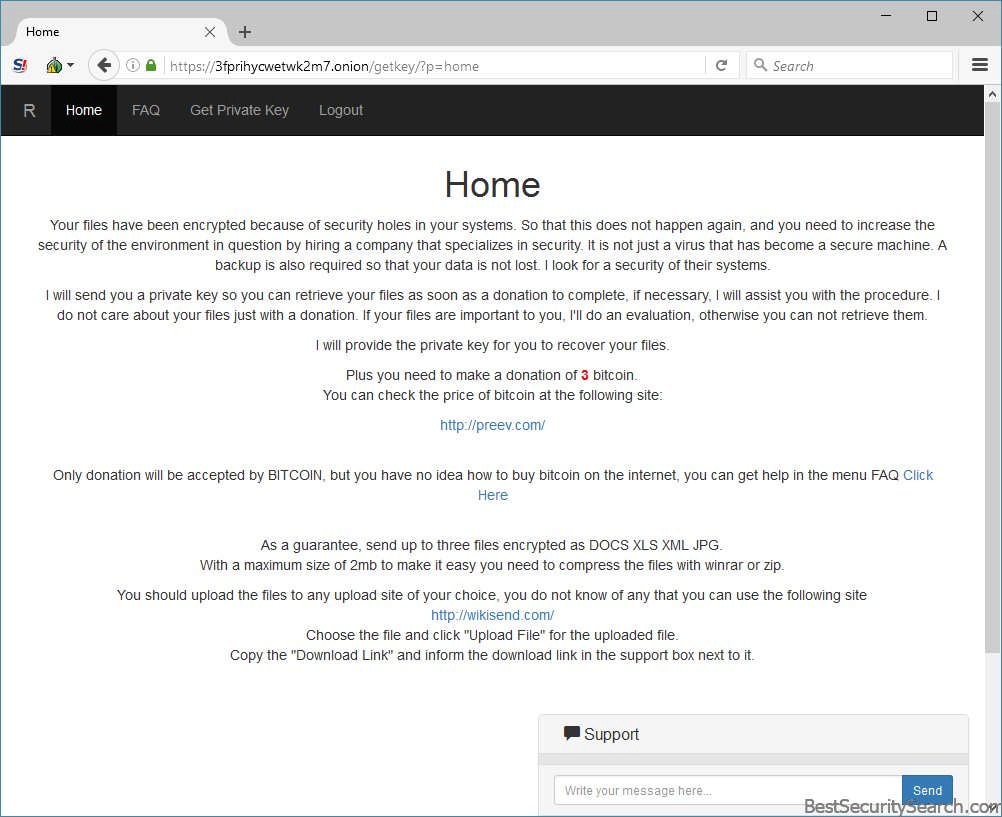
If the users go to the payment gateway they are shown a page which asks them for their key. Once it is placed they redirected inside the payment site which reads the following information:
Your files have been encrypted because of security holes in your systems. So that this does not happen again, and you need to increase the
security of the environment in question by hiring a company that specializes in security. It is not just a virus that has become a secure machine. A
backup is also required so that your data is not lost. I look for a security of their systems.I will send you a private key so you can retrieve your files as soon as a donation to complete, if necessary, I will assist you with the procedure. I do not care about your files just with a donation. If your files are important to you. I’ll do an evaluation, otherwise you can not retrieve them.
I will provide the private key for you to recover your files.
Plus you need to make a donation of 3 bitcoin.
You can check the price of bitcoin at the following site:http://preev.com
Only donation will be accepted by BITCOIN, but you have no idea how to buy bitcoin on the internet, you can get help in the menu FAQ Click here
As a guarantee, send up to three files encrypted as DOCS XLS XML JPG.
With a maximum size of 2mb to make it easy you need to compress the files with winrar or zip.You should upload the files to any upload site of your choice, you do not know of any that you can use the following site
http://wikisend.com/Choose the file and click “Upload File” for the uploaded file.
Copy the “Download Link” and inform the download links in the support box next to it.
From the gathered information we can conclude the following about the virus;
- High Ransomware Sum Request – The hackers behind the threat request the sum of 3 Bitcoins which is almost 4 US Dollars in equivalent.
- Unknown Developers – The virus is being made by an unknown hacker or hacker collective.
- Template Use – The ransomware uses a template-based note and payment gateway site which seems to be copied from other similar threats.
- Support Section – The hackers provides a support function that the victims can use.
NM4 Ransomware Distribution
The captured samples of the NM4 ransomware are limited in number at this time. This does not give a clear indication of the distribution methods employed by the hackers. We suspect that the NM4 ransomware is distributed using one of the following methods:
- Direct Hacker Attacks Automated or manual intrusion attempts may be attempted against the predefined targets. In the last few years most of the ransomware strategies use automated frameworks that use software exploits to gain entry into internal networks and computers. Computer users can protect themselves by always applying the latest software updates of all installed applications and using a quality anti-spyware solution that is able to protect to protect them from any incoming threats, as well as remove easily any active infections.
- Infected Installers – Malware such as the NM4 ransomware are often bundled with software installers of popular trial or free versions of applications, games, patches, utilities and etc. The hackers usually take the official packages from their original source and repackage them with the malicious code.
- Hacker-controlled Download Sites and P2P Networks – The computer hackers behind the ransomware usually distribute the files directly or bundled with software installers (see above) on hacked or owned download sites. They may pose as official sources or sponsored sources of the applications or legitimate download portals. In the last few years much of the BitTorrent trackers and other P2P networks have also been infested with various types of malware, including dangerous ransomware strains such as this one.
- Email Spam Messages – The criminals use email spam messages as one of the primary ways of spreading malware. Depending on the attack campaign they may send the ransomware binary either as an attachment or linked in the body of the message. Other tactics include the use of malicious scripts embedded in fake documents or infected software installers are also used by the hackers.
Summary of the NM4 Ransomware
| Name |
NM4 Ransomware |
| File Extensions |
.NM4 |
| Ransom |
3 Bitcoins |
| Easy Solution |
You can skip all steps and remove NM4 Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
NM4 Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
NM4 Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely NM4 Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover NM4 Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore NM4 Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



