The Point of Sales terminals are among the most tempting target for credit card data stealing. There are many reported cases of POS malware infections until now. Is seems that cyber criminals are insatiable to create new and modify the existing versions of POS Trojans. The latest security news report released by the researchers from Russian based company Dr.Web reveals the existence of a new version of Trojan.MWZLesson. The name of the new Trojan is Trojan.Kasidet.1.

The malware Trojan.MWZLesson that targets PoS systems was discovered in September 2015. One interesting discovery about this malware is its capability to launch DDoS attacks. After a week later another interesting discovery was made by security researchers from Trend Micro. They have realized that Trojan.MWZLesson was part of Kasidet (Neutrino) DDoS malware mechanism. It’s known for this malware to have PoS memory scraping module.
Characteristics of Trojan.Kasidet.1
The distribution of Trojan.Kasidet.1 is realized via ZIP archive that contains SCR file. This file type is generally associated with “Script” and is known to transmit Trojans from 2007. In the case of Trojan.Kasidet.1 the SCR distribution file is a self-extracting SFX-RAR archive. This file runs the primary malicious payload.
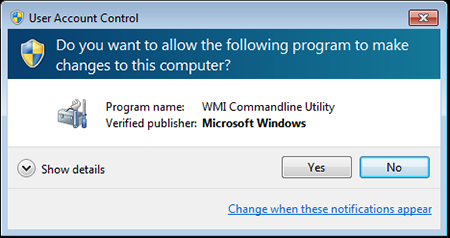
At the first stage of infection, the Trojan does a check if there are any virtual machines, emulators, debuggers or its copy in the infected system. In case it finds a program that can block its operation it terminates itself. Otherwise, it gains administrator privileges and continues with the infection process. Then the victim is successfully deceived with a warning window on the screen that appears to be developed by Microsoft.
A click on “Yes” button runs the executable file of Trojan.Kasidet.1. By the means of the POS scraping module, it does a memory scan for existing credit card data. Then the Trojan sends the stolen data to its command and control (C&C) server. Furthermore, in order to successfully intercept the GET and POST requests, it can steal passwords from the email applications Thunderbird, Foxmail, and Outlook that are usually integrated into Google Chrome, Mozilla Firefox, Microsoft Internet Explorer, and Maxthon browsers. Unfortunately, the malicious actions of Trojan.Kasidet.1 don’t end here. It can also download and execute another malicious library or application on the infected computer. Finding a particular file on a disk, generating a list of running processes and sending the information to its C&C server are parts of its infection as well.
The difference between Trojan.MWZLesson and Trojan.Kasidet.1 is that the C&C server addresses of Kasidet are hosted in the domain zone of Namecoin that allows a person to create .bit domains. These websites cannot be accessed by standard browsers. A unique tool NMControl should be utilized to obtain .bit websites.
In conclusion some good news stated by the researchers from Dr.Web:
“Although malware programs that use this Namecoin technology have been known since 2013, they are not frequently detected in the wild.“.