Security researchers from RiskIQ identified a large malicious campaign called Magecart that steals payment card data from major eCommerce sites.
The Magecart Campaign Is a Massive Intrusion Against eCommerce Sites
The security experts from RiskIQ have shed some lights on a big ongoing campaign, which has been active from at least March 2016, targeted against large eCommerce sites. Computer hackers target various eCommerce platforms such as Magecart, OpenCart, and Powerfront CMS. They target payment processing services such as Braintree and VeriSign and the online stores as well.
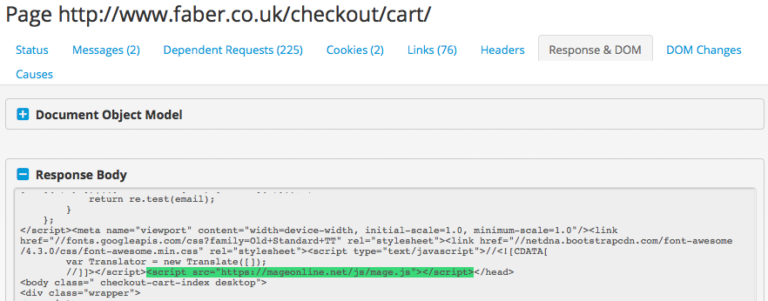
The security experts have identified more than 100 stores worldwide that are parts of the campaigns. The employed tools are Javascript code injections into the site that aim to capture the entered information by the visitors. This is a type of a man-in-the-middle attack between the victim user and the checkout page. In some of the cases, the malware has added form fields of its own which tricks the user into giving them even additional information. The stolen data is exfiltrated over a HTTPS secure connection to a remote server controlled by the operators of Magecart.
By directly injecting the sites with the malicious code the attackers can easily modify and update the malware without reinfecting them. According to the data, the peak of the Magecart campaign was in June. That is when the criminals started to us an Eastern European hosting company to store the domains that served the malware code. In the latest iterations of the attacks, the researchers also noticed additional script injection techniques that featured code obfuscation.
For more detailed information you can view the complete report on RiskIQ’s blog.