Security experts have managed to modify a recently leaked Cisco exploit to work on additional equipment. The vendor has still not developed a patch and only provides workarounds to amend the vulnerability.
Cisco Devices Are Under a Very Serious Threat
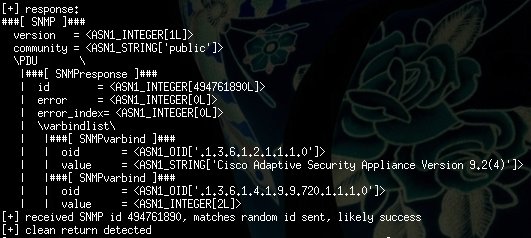
One of the most famous exploits that were part of the Equation Group leak has been modified to work on a wider range of Cisco Adaptive Security Appliance (ASA) firewalls as originally intended. The updated exploit was developed by the Hungarian penetration testing company Silent Signal. Their team have modified the source code and have made it effective against version ASA 9.2 (4), a substantial update as the original code exploited devices with ASA 8.4 (4) and earlier. The security experts have updated the shell code scripts to target newer versions of the Cisco devices. Their research indicates that the original exploit has been created by expert programmers. The lack of exploit mitigation techniques is a serious problem that potential malicious users can utilize.
Execution of the upgraded version doesn’t require a lot of work, however, the damage potential depends on the target conditions. The maximum impact can be achieved if the attackers have compromised the victim network. Knowledge of the SNMP community string and default configurations also helps the exploit to achieve it’s maximum efficiency. The vulnerability itself relies on buffer overflow errors in the target systems that allow remote attackers to cause a restart of the affected systems or to execute arbitrary code on the victim machines.
As the exploit is public knowledgeable malicious users can it against targets or modify it further to add new features and capabilities. Cisco ASA devices are popular among both big corporations and government agencies. At this time Cisco has not released a working solution that can resolve the security issues. Administrators are advised to allow only trusted users with SNMP access and to carefully review suspicious or affected machines with the SNMP-server host command.