An infection with the dangerous .vpgvlkb virus leads to serious security issues. Victims can restore and protect their computers by following our complete removal guide.
Remove .vpgvlkb virus and Restore PC
Manual Removal Guide
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Distribution of .vpgvlkb virus
The .vpgvlkb virus is a new virus which has been sighted in a limited attack campaign. At the moment the security researchers cannot determine the primary infection strategy. We presume that the most widely used tactics are going to be employed.
Among them are the email messages created in an automated way and sent to large lists of potential victims. The .vpgvlkb virus can be directly attached to the messages. This is one of the easiest way for the criminals to attempt the infection. However a lot of email hosting providers usually capture the signatures of the virus and as such discard such messages or label them as dangerous or spam. Other infection methods related to this one is the option of inserting hyperlinks in the body content of the messages. The links are usually labeled as leading to a familiar website or a file of user interest. Redirects can redirect to hacker-controlled sites, infected payloads or other instances that can lead to an .vpgvlkb virus infection.
The computer criminals behind the malware can create malicious sites or download portals which distribute malware of different kinds, including the .vpgvlkb virus. A popular option is the use of infected documents which may be of different types ‒ spreadsheets, rich text documents, presentations and databases. They are modified to initiate the virus once the built-in scripts are run. Usually when the files are opened a notification will ask the users to run the macros (scripts). If this is done the infection follows.
The hacker-controlled sites are specialist portals that have been created either manually or automatically by the criminals behind the .vpgvlkb virus. They can either directly distribute the threat by initiating various scripts or automated operations or link to such instances. Redirects are usually caused by email interaction, ad networks or other browsing activity. However one of the main sources is the availability of browser hijackers. They are malicious addons made for the most popular web browsers ‒ Mozilla Firefox, Google Chrome, Internet Explorer, Opera, Microsoft Edge and Safari. Once installed they not only infect the users with the malware, but also redirect the victims to a hacker-controlled site. Depending on the configuration the browser hijackers can also steal sensitive information such as any stored passwords, account credentials, history, bookmarks, form data and settings.
Impact of .vpgvlkb virus
The .vpgvlkb virus is a sample of the Magniber ransomware which has been reported by the security community. This threat is one of the most dangerous infections in the last few months and it still continues to target the same group of computer users ‒ those from South Korea. One of the most dangerous aspects associated with it is the fact that the Magnitude exploit kit is the same weapon used to deliver a large part of the Cerber ransomware strains. So far the larger part of the .vpgvlkb virus samples infect primarily through automatically generated malware email messages.
The security experts note that the hacker operators behind the threat attempt to exploit a vulnerability that is being tracked as CVE-2016-0189 which is also used by other exploit kits such as Disdain and Sundown. Its description reads the following:
The Microsoft JScript 5.8 and VBScript 5.7 and 5.8 engines, as used in Internet Explorer 9 through 11 and other products, allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site, aka “Scripting Engine Memory Corruption Vulnerability,” a different vulnerability than CVE-2016-0187.
Once the initial infection has made the initial infection the .vpgvlkb virus starts to execute its complex attack scheme. It can be configured depending on the target users and computers however to a larger extent it combines several important modules that can be activated. They can be uploaded and activated upon the victim machines. Examples include the following components:
- Virus Infections ‒ The .vpgvlkb virus can be used to deliver additional threats to the victim computers.
- Information Harvesting ‒ One of the first malware actions taken by the infection engine is to conduct a thorough data harvesting process. This may include a system analysis comprising of the hardware components, installed software and user settings. In other cases the criminals may opt to steal sensitive files, including financial documents and private photos.
- Spying Module ‒ The criminals behind the ransomware can include a fully-featured Trojan component which would allow them to spy on the victims in real time, as well as record their mouse movement and keystrokes. Depending on the case they may also be able to take over control of the machine at any given time.
- Stealth Protection ‒ Some versions of the .vpgvlkb virus are able to protect themselves from virtual machines, debugging environments and sandboxes.
At the onset of infection the main .vpgvlkb virus files are immediately copied to a temporary folder to prevent manual user removal. Unlike other similar threats the base engine actually changes the names of all associated files with random files so that the malware data cannot be spotted using a regular scan. Some versions of the .vpgvlkb virus have the ability to install themselves as a persistent threat. This means that their infection engine will actively monitor the users actions and protect itself from removal.
Other malware actions that have been found to be carried out by the .vpgvlkb virus are related to process creation. The security analysts discovered that the malware enginr is able to create many processes with different privileges of its own, as well as “hook” itself to both running apps and Windows services. This makes it very easy to carry out complex attack scenarios. In addition .vpgvlkb virus samples are also known to be able to execute commands as instructed by the hackers.
A possibility is the launch of windows and pop-ups from legitimate and widely used applications such as web browsers. The advanced infection capabilities means that the hacker operators behind the .vpgvlkb virus have the ability to modify important settings in a manner similar to hijackers. Modifications include the following: default home page, search engine and new tabs page which can all point to a hacker-designated address. In addition the .vpgvlkb may be used to extract valuable information from the browsers as well: any stored cookies, history, bookmarks, settings, passwords and account credentials. Similar viruses can impact the most widely used browsers: Google Chrome, Mozilla Firefox, Opera, Safari, Microsoft Edge and Internet Explorer.
Once all preliminary conditions have been met the ransomware process is started. Like the base threat this strain also uses the same old list of target file type extensions which includes the following data:
docx xls xlsx ppt pptx pst ost msg em vsd vsdx csv rtf 123 wks wk1 pdf dwg
onetoc2 snt docb docm dot dotm dotx xlsm xlsb xlw xlt xlm xlc xltx xltm pptm
pot pps ppsm ppsx ppam potx potm edb hwp 602 sxi sti sldx sldm vdi vmx gpg
aes raw cgm nef psd ai svg djvu sh class jar java rb asp php jsp brd sch dch
dip vb vbs ps1 js asm pas cpp cs suo sln ldf mdf ibd myi myd frm odb dbf db
mdb accdb sq sqlitedb sqlite3 asc lay6 lay mm sxm otg odg uop std sxd otp
odp wb2 slk dif stc sxc ots ods 3dm max 3ds uot stw sxw ott odt pem p12 csr
crt key pfx der 1cd cd arw jpe eq adp odm dbc frx db2 dbs pds pdt dt cf cfu
mx epf kdbx erf vrp grs geo st pff mft efd rib ma lwo lws m3d mb obj x3d c4d
fbx dgn 4db 4d 4mp abs adn a3d aft ahd alf ask awdb azz bdb bib bnd bok btr
cdb ckp clkw cma crd dad daf db3 dbk dbt dbv dbx dcb dct dcx dd df1 dmo dnc
dp1 dqy dsk dsn dta dtsx dx eco ecx emd fcd fic fid fi fm5 fo fp3 fp4 fp5
fp7 fpt fzb fzv gdb gwi hdb his ib idc ihx itdb itw jtx kdb lgc maq mdn mdt
mrg mud mwb s3m ndf ns2 ns3 ns4 nsf nv2 nyf oce oqy ora orx owc owg oyx p96
p97 pan pdb pdm phm pnz pth pwa qpx qry qvd rctd rdb rpd rsd sbf sdb sdf spq
sqb stp str tcx tdt te tmd trm udb usr v12 vdb vpd wdb wmdb xdb xld xlgc zdb
zdc cdr cdr3 abw act aim ans apt ase aty awp awt aww bad bbs bdp bdr bean
bna boc btd cnm crw cyi dca dgs diz dne docz dsv dvi dx eio eit emlx epp err
etf etx euc faq fb2 fb fcf fdf fdr fds fdt fdx fdxt fes fft flr fodt gtp frt
fwdn fxc gdoc gio gpn gsd gthr gv hbk hht hs htc hz idx ii ipf jis joe jp1 jrtf
kes klg knt kon kwd lbt lis lit lnt lp2 lrc lst ltr ltx lue luf lwp lyt lyx man
map mbox me mel min mnt mwp nfo njx now nzb ocr odo of oft ort p7s pfs pjt prt
psw pu pvj pvm pwi pwr qd rad rft ris rng rpt rst rt rtd rtx run rzk rzn saf
sam scc scm sct scw sdm sdoc sdw sgm sig sla sls smf sms ssa sty sub sxg tab
tdf tex text thp tlb tm tmv tmx tpc tvj u3d u3i unx uof upd utf8 utxt vct vnt
vw wbk wcf wgz wn wp wp4 wp5 wp6 wp7 wpa wpd wp wps wpt wpw
wri wsc wsd wsh wtx
xd xlf xps xwp xy3 xyp xyw ybk ym zabw zw abm afx agif agp aic albm apd apm
apng aps apx art asw bay bm2 bmx brk brn brt bss bti c4 ca cals can cd5 cdc
cdg cimg cin cit colz cpc cpd cpg cps cpx cr2 ct dc2 dcr dds dgt dib djv dm3
dmi vue dpx wire drz dt2 dtw dv ecw eip exr fa fax fpos fpx g3 gcdp gfb gfie
ggr gih gim spr scad gpd gro grob hdp hdr hpi i3d icn icon icpr iiq info ipx
itc2 iwi j2c j2k jas jb2 jbig jbmp jbr jfif jia jng jp2 jpg2 jps jpx jtf jw
jxr kdc kdi kdk kic kpg lbm ljp mac mbm mef mnr mos mpf mpo mrxs my ncr nct
nlm nrw oc3 oc4 oc5 oci omf oplc af2 af3 asy cdmm cdmt cdmz cdt cmx cnv csy
cv5 cvg cvi cvs cvx cwt cxf dcs ded dhs dpp drw dxb dxf egc emf ep eps epsf
fh10 fh11 fh3 fh4 fh5 fh6 fh7 fh8 fif fig fmv ft10 ft11 ft7 ft8 ft9 ftn fxg
gem glox hpg hpg hp idea igt igx imd ink lmk mgcb mgmf mgmt mt9 mgmx mgtx
mmat mat ovp ovr pcs pfv plt vrm pobj psid rd scv sk1 sk2 ssk stn svf svgz
tlc tne ufr vbr vec vm vsdm vstm stm vstx wpg vsm xar ya orf ota oti ozb
ozj ozt pa pano pap pbm pc1 pc2 pc3 pcd pdd pe4 pef pfi pgf pgm pi1 pi2 pi3
pic pict pix pjpg pm pmg pni pnm pntg pop pp4 pp5 ppm prw psdx pse psp ptg
ptx pvr px pxr pz3 pza pzp pzs z3d qmg ras rcu rgb rgf ric riff rix rle rli
rpf rri rs rsb rsr rw2 rw s2mv sci sep sfc sfw skm sld sob spa spe sph spj
spp sr2 srw wallet jpeg jpg vmdk arc paq bz2 tbk bak tar tgz gz 7z rar zip
backup iso vcd bmp png gif tif tiff m4u m3u mid wma flv 3g2 mkv 3gp mp4 mov
avi asf mpeg vob mpg wmv fla swf wav mp3
Previous samples are known to include an exclusion list which contains the following directories:
:\documents and settings\all users\
:\documents and settings\default user\
:\documents and settings\localservice\
:\documents and settings\networkservice\
\appdata\local\
\appdata\locallow\
\appdata\roaming\
\local settings\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
\$recycle.bin
\$windows.~bt
\$windows.~ws
\boot
\intel
\msocache
\perflogs
\program files (x86)
\program files
\programdata
\recovery
\recycled
\recycler
\system volume information
\windows.old
\windows10upgrade
\windows
\winnt
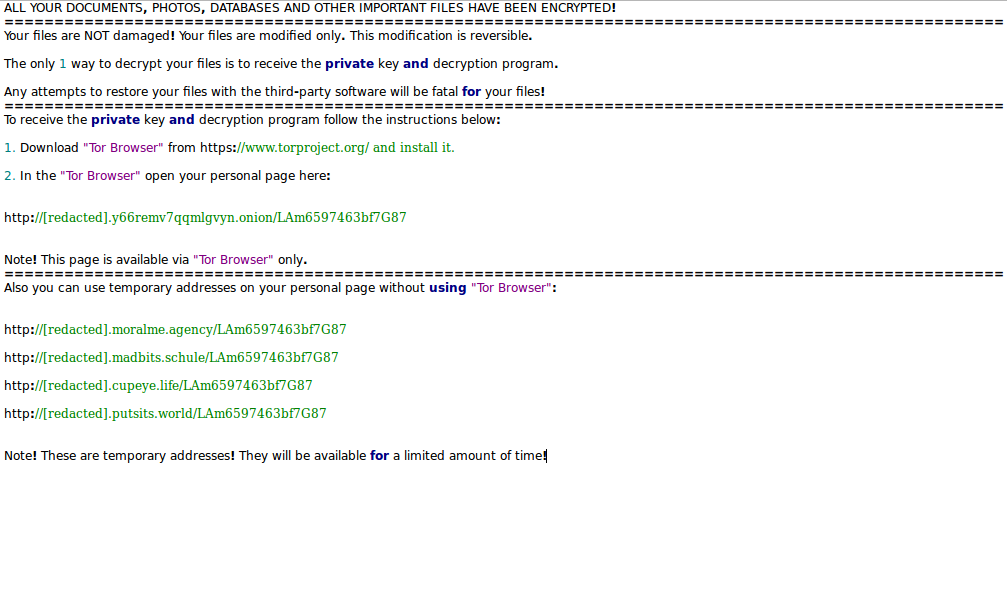
The ransomware note itself is created in a read me for decrypt.txt file which reads the following:
ALL YOUR DOCUMENTS, PHOTOS, DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED!
====================================================================================================
Your files are NOT damaged! Your files are modified only. This modification is reversible.The only 1 way to decrypt your files is to receive the private key and decryption program.
Any attempts to restore your files with the third-party software will be fatal for your files!
====================================================================================================
To receive the private key and decryption program follow the instructions below:1. Download “Tor Browser” from https://www.torproject.org/ and install it.
2. In the “Tor Browser” open your personal page here:
http://[redacted].y66remv7qqmlgvyn.onion/LAm6597463bf7G87
Note! This page is available via “Tor Browser” only.
====================================================================================================
Also you can use temporary addresses on your personal page without using “Tor Browser”:http://[redacted].moralme.agency/LAm6597463bf7G87
http://[redacted].madbits.schule/LAm6597463bf7G87
http://[redacted].cupeye.life/LAm6597463bf7G87
http://[redacted].putsits.world/LAm6597463bf7G87
Note! These are temporary addresses! They will be available for a limited amount of time!
We recommend that all users abstain from communicating with the hackers and use our full .vpgvlkb virus removal guide below to recover their data and delete the active infections.
Remove .vpgvlkb virus and Restore PC
WARNING! Manual removal of the .vpgvlkb virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.vpgvlkb virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Remove .vpgvlkb from Windows
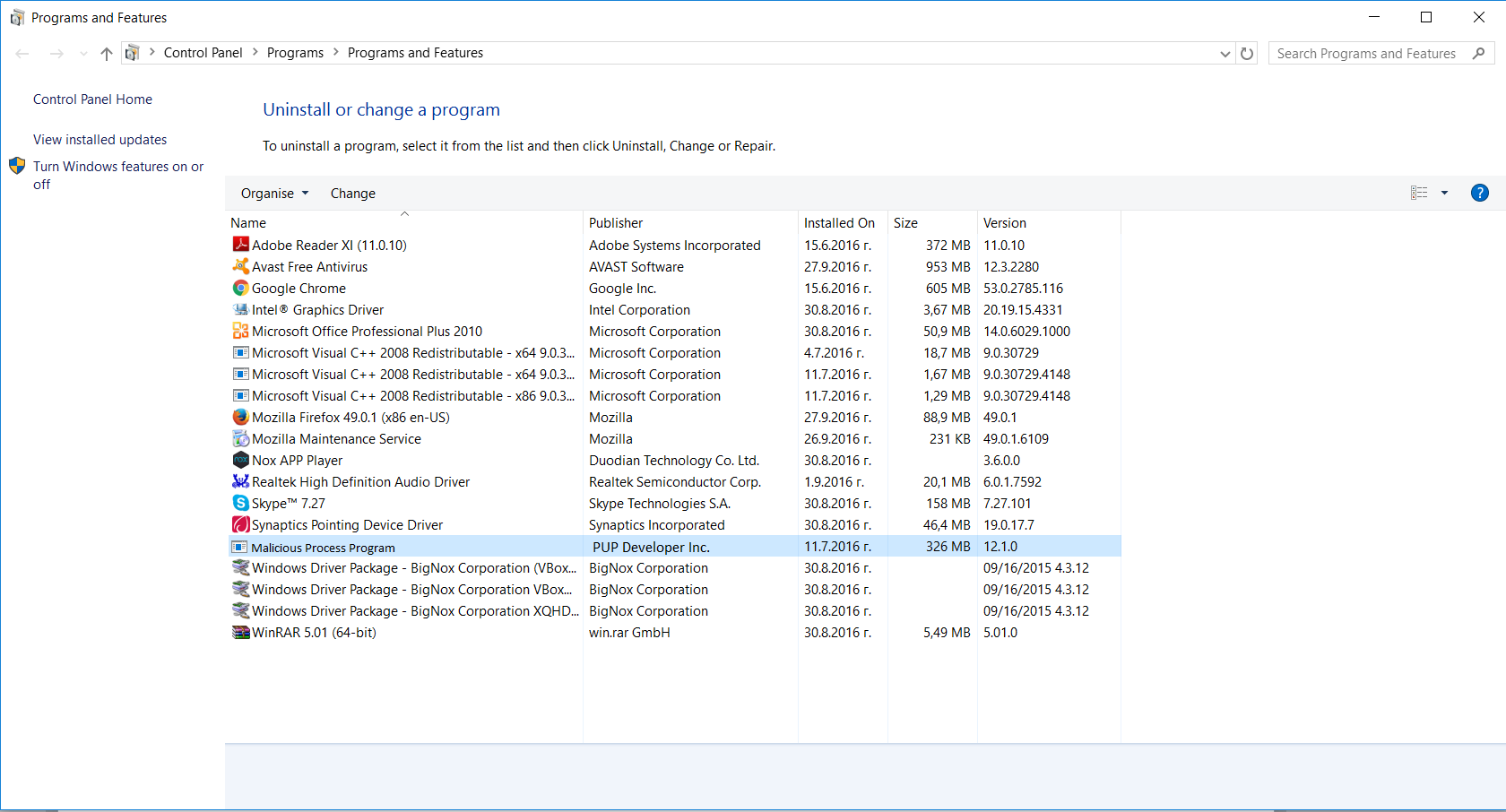
Here’s a way to remove the program. This method will work regardless if you’re on Windows 10, 8, 7, Vista or XP. Simply selecting the program and pressing delete won’t work, as it’ll leave a lot of small files. That’s bad because these leftovers can linger on and cause all sorts of problems. The best way to delete a program is to uninstall it. Here’s how you can do that:
1. Hold the “Windows” button (It’s between CTRL and Alt on most keyboards) and press “R”. You’ll see a pop-up window.
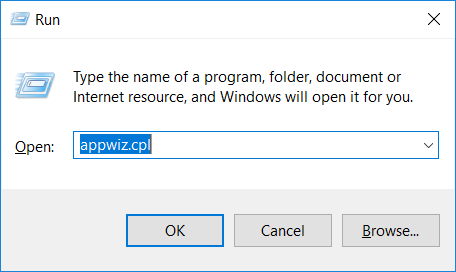
2. In the textbox, type “appwiz.cpl”, then press“ Enter ”.
3. The “Programs and features” menu should now appear. It’s a list of all the programs installed on the PC. Here you can find the program, select it, and press “Uninstall“.
Remove .vpgvlkb Virus From Your Browser
Before resetting your browser’s settings, you should know that this action will wipe out all your recorded usernames, passwords, and other types of data. Make sure to save them in some way.
-
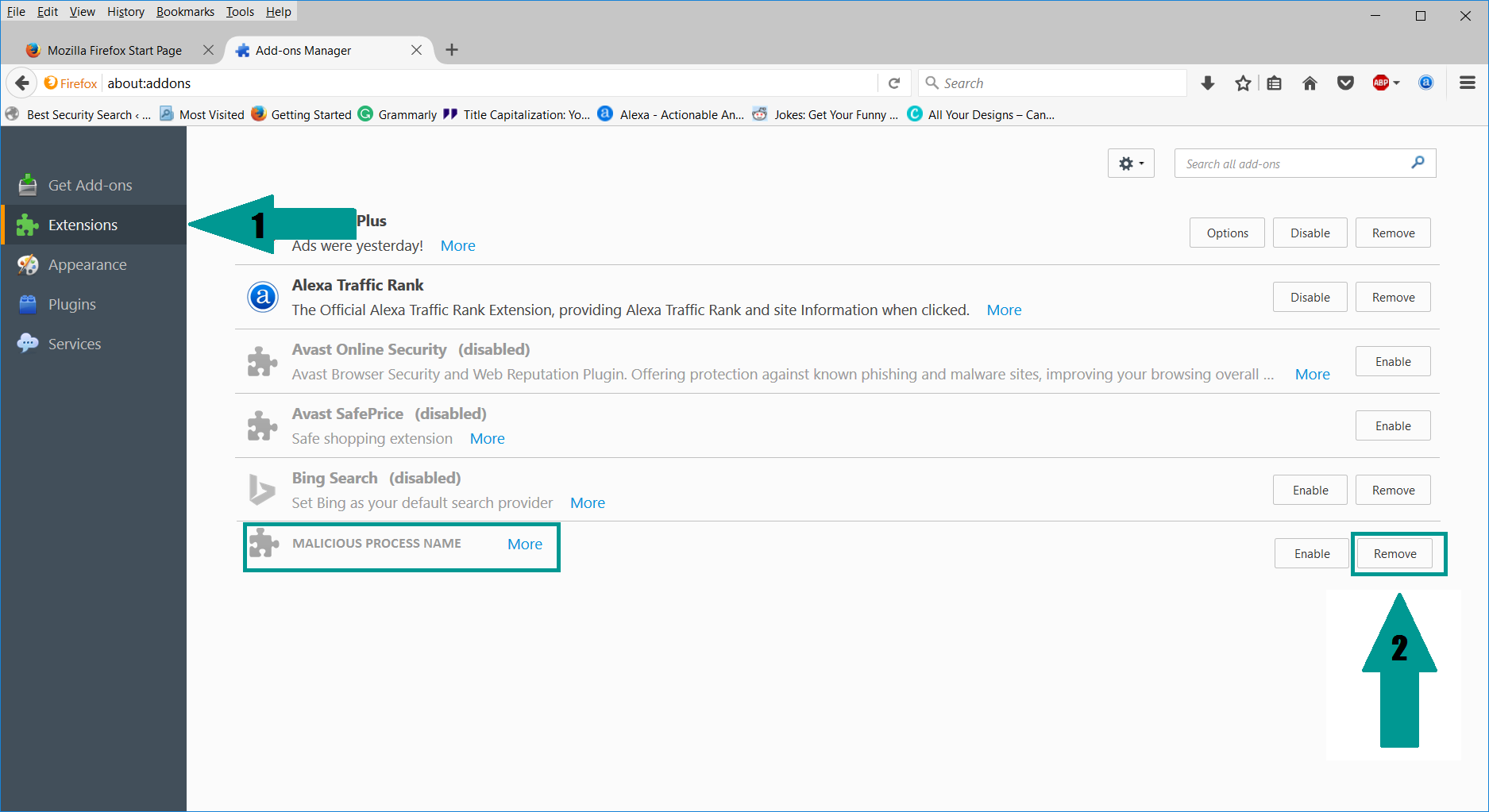
1. Start Mozilla Firefox. In the upper right corner, click on the Open menu icon and select “Add-ons“.

2. Inside the Add-ons Manager select “Extensions“. Search the list of extensions for suspicious entries. If you find any, select them and click “Remove“.
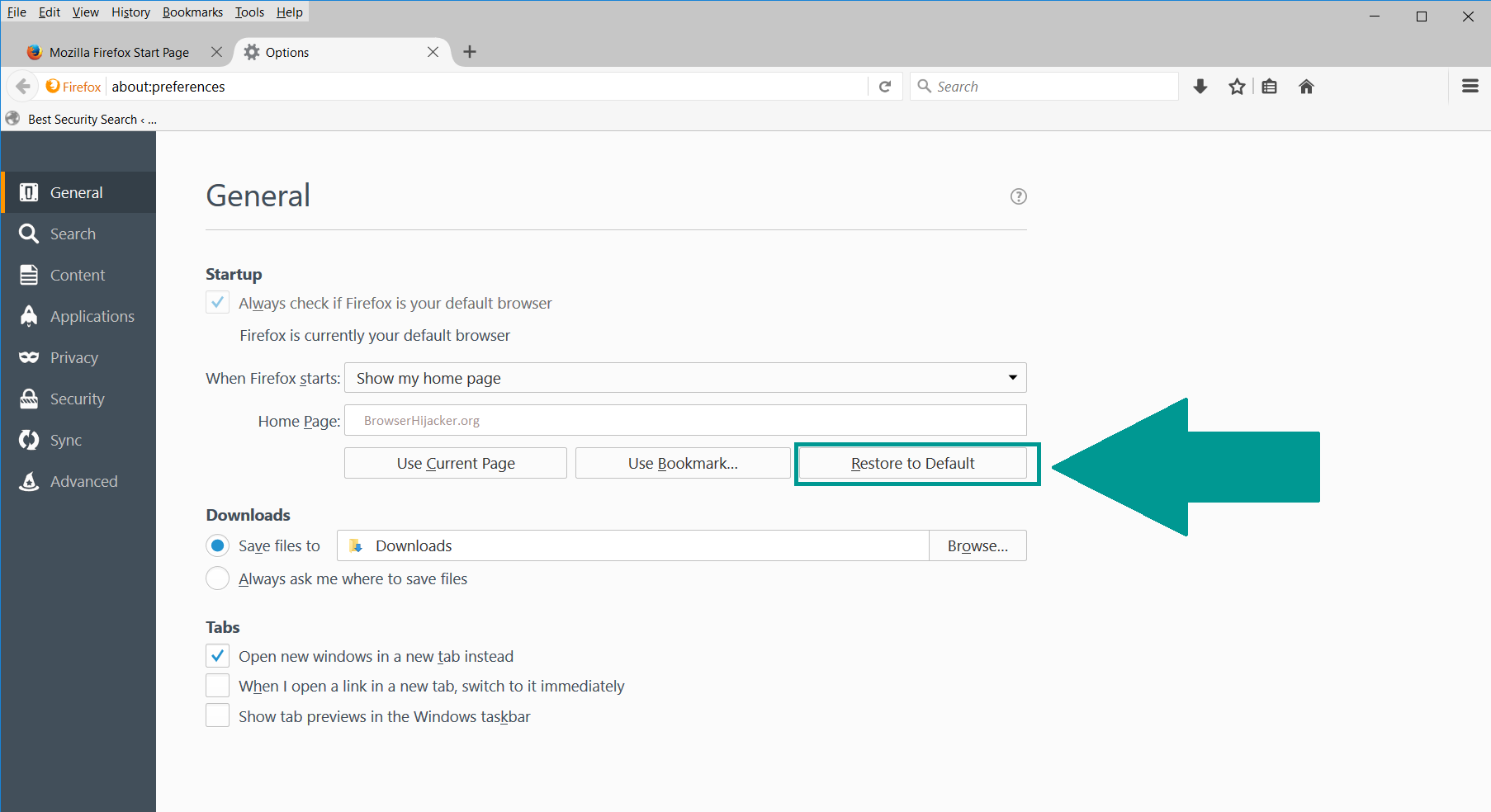
3. Click again on the Open menu icon, then click “Options“.

4. In the Options window, under “General” tab, click “Restore to Default“.
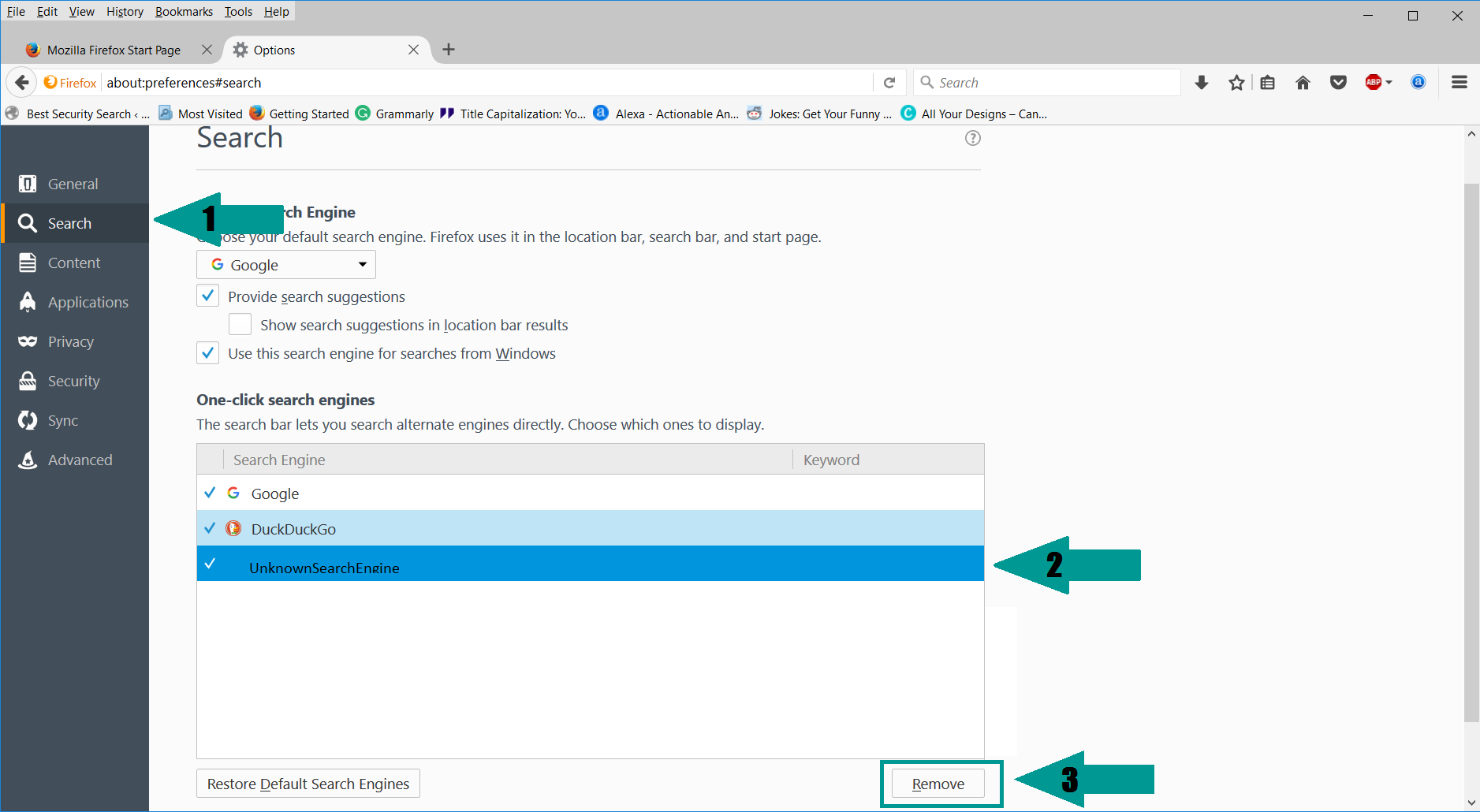
5. Select “Search” in the left menu, mark the unknown search engine and press “Remove”.
-
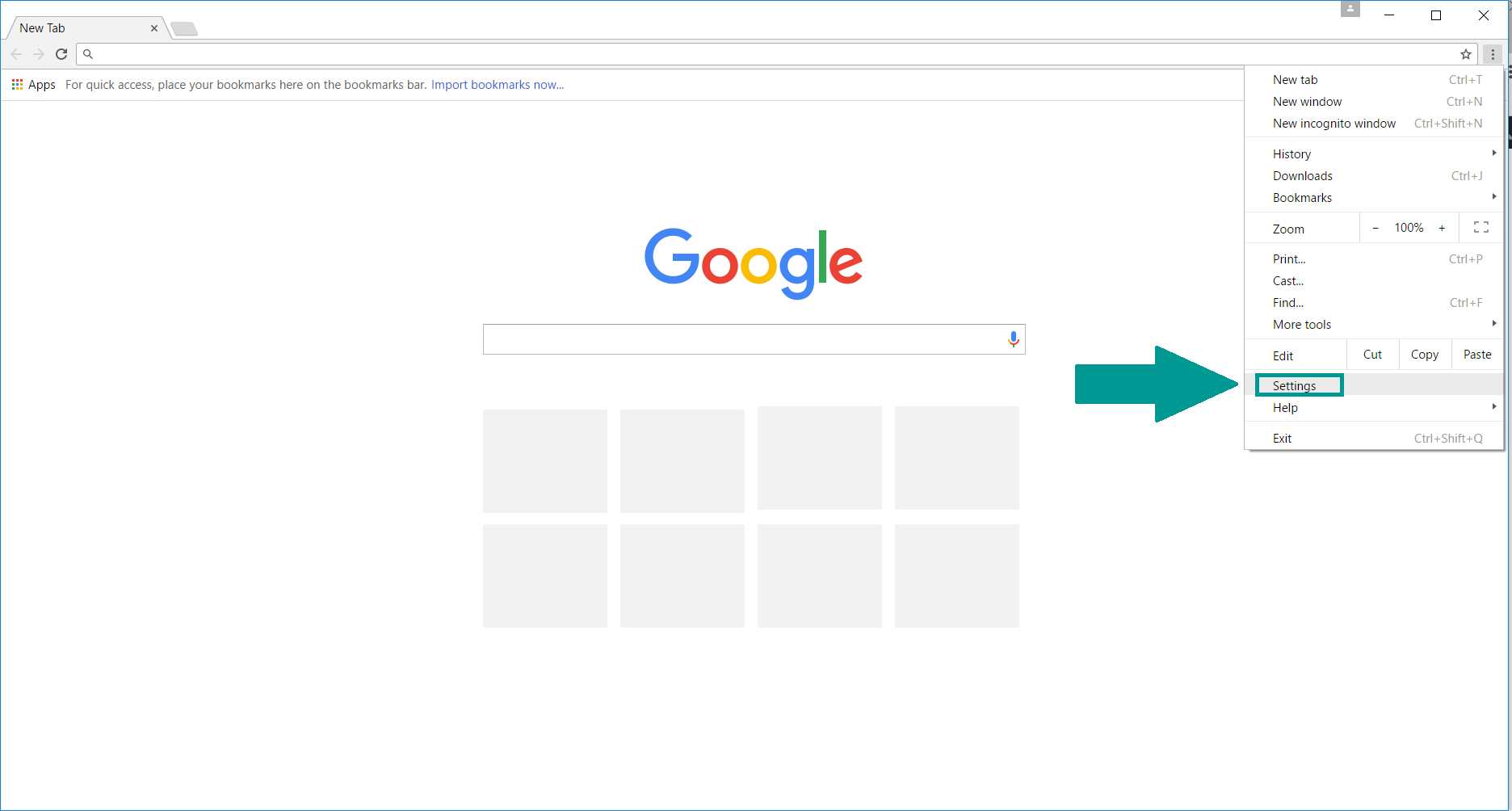
1. Start Google Chrome. On the upper-right corner, there a “Customize and Control” menu icon. Click on it, then click on “Settings“.
2. Click “Extensions” in the left menu. Then click on the trash bin icon to remove the suspicious extension.
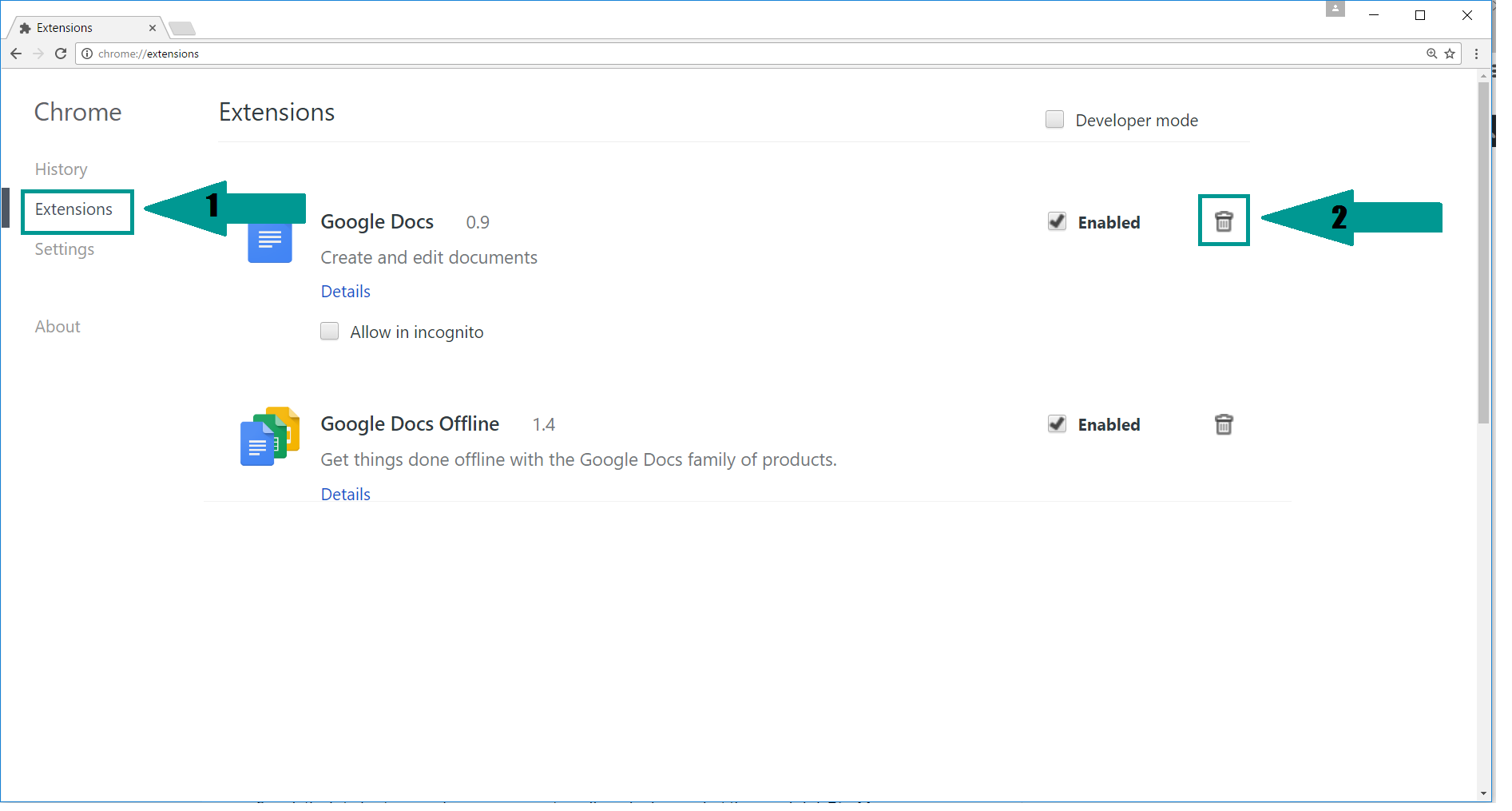
3. Again in the left menu, under Chrome, Click on “Settings“. Go under “On Startup” and set a new page.
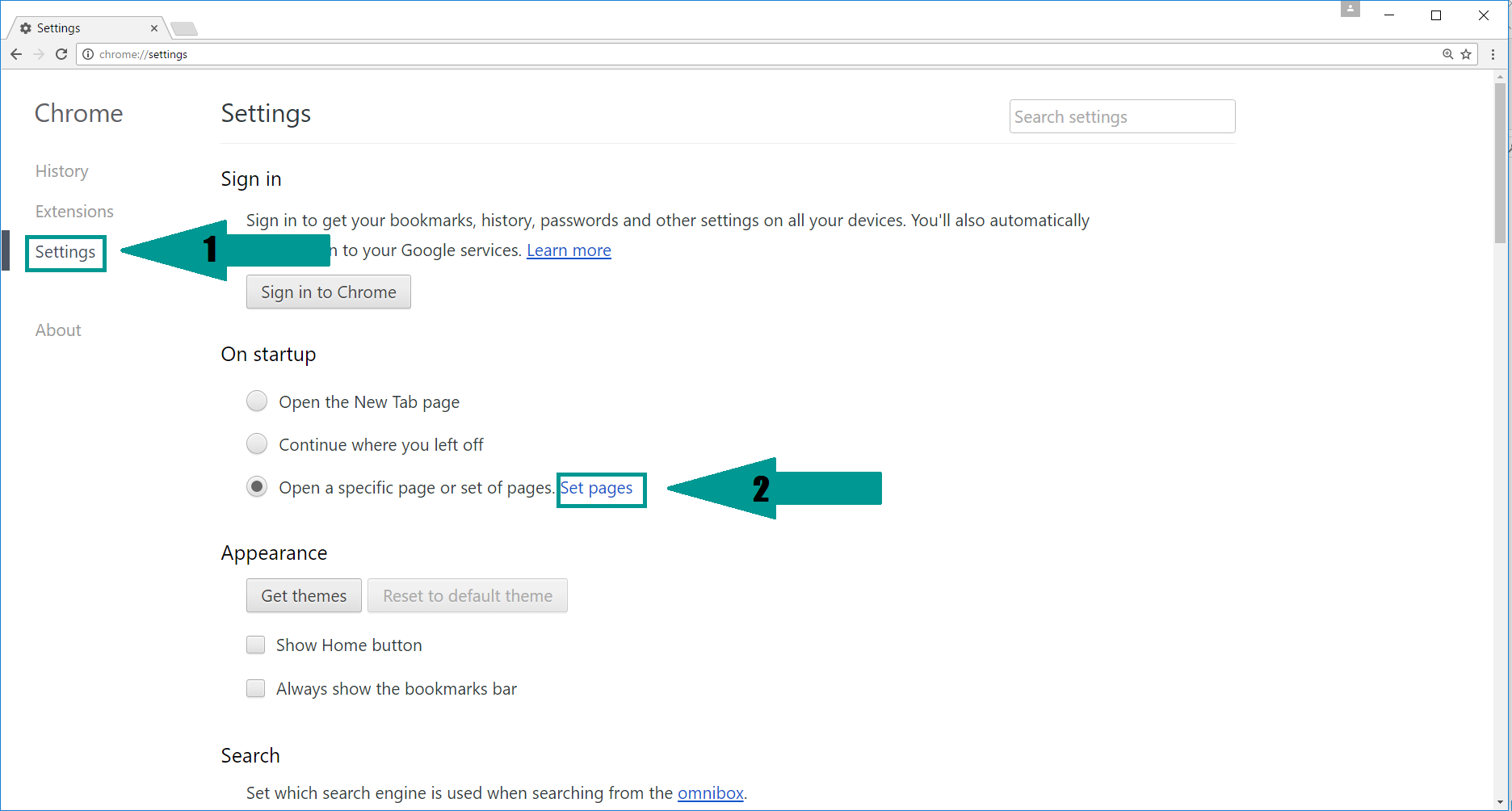
4. Afterward, scroll down to “Search“, click on “Manage search engines“.
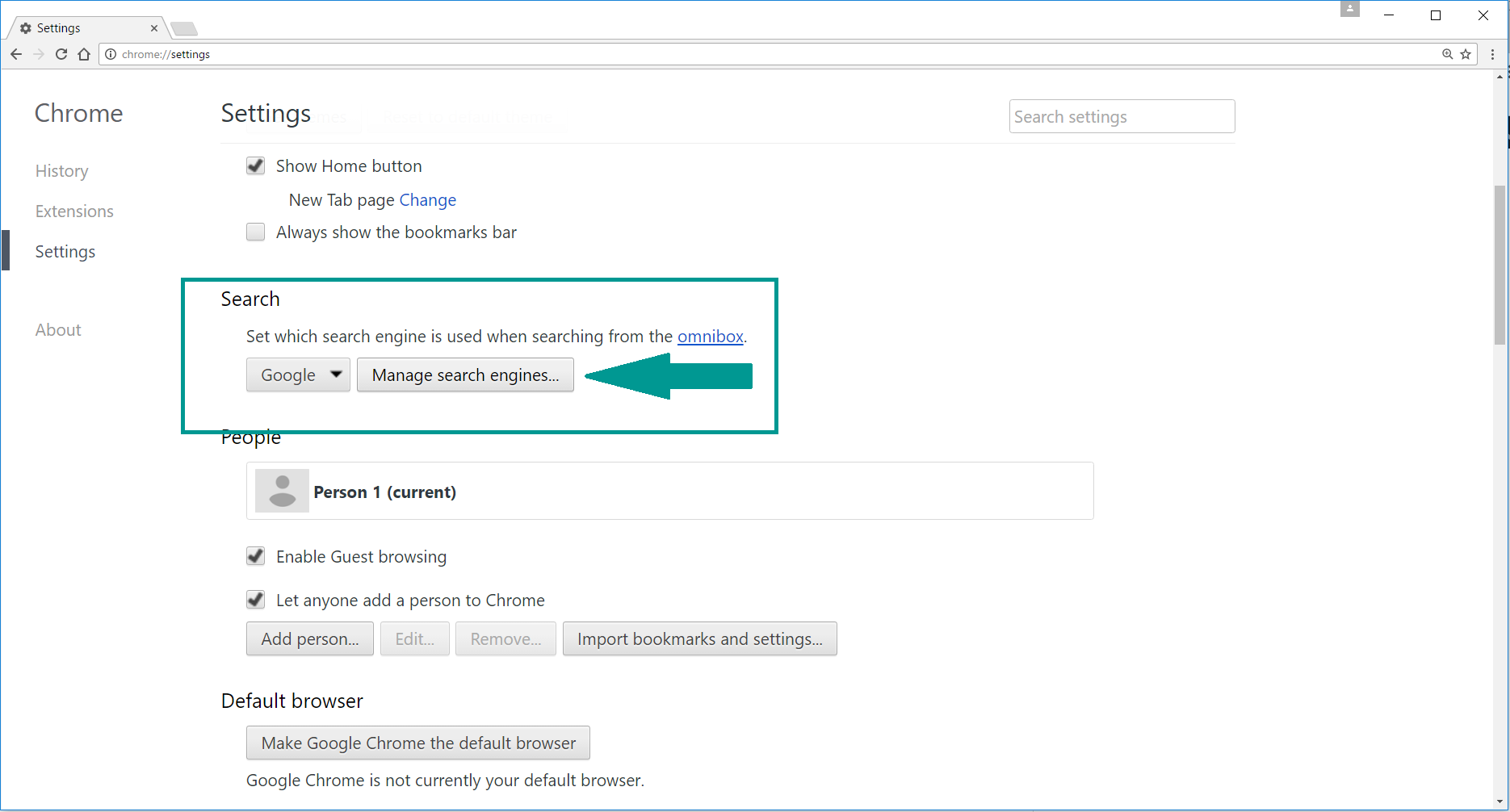
5. In the default search settings list, find the unknown search engine and click on “X“. Then select your search engine of choice and click “Make default“. When you are ready click “Done” button in the right bottom corner.
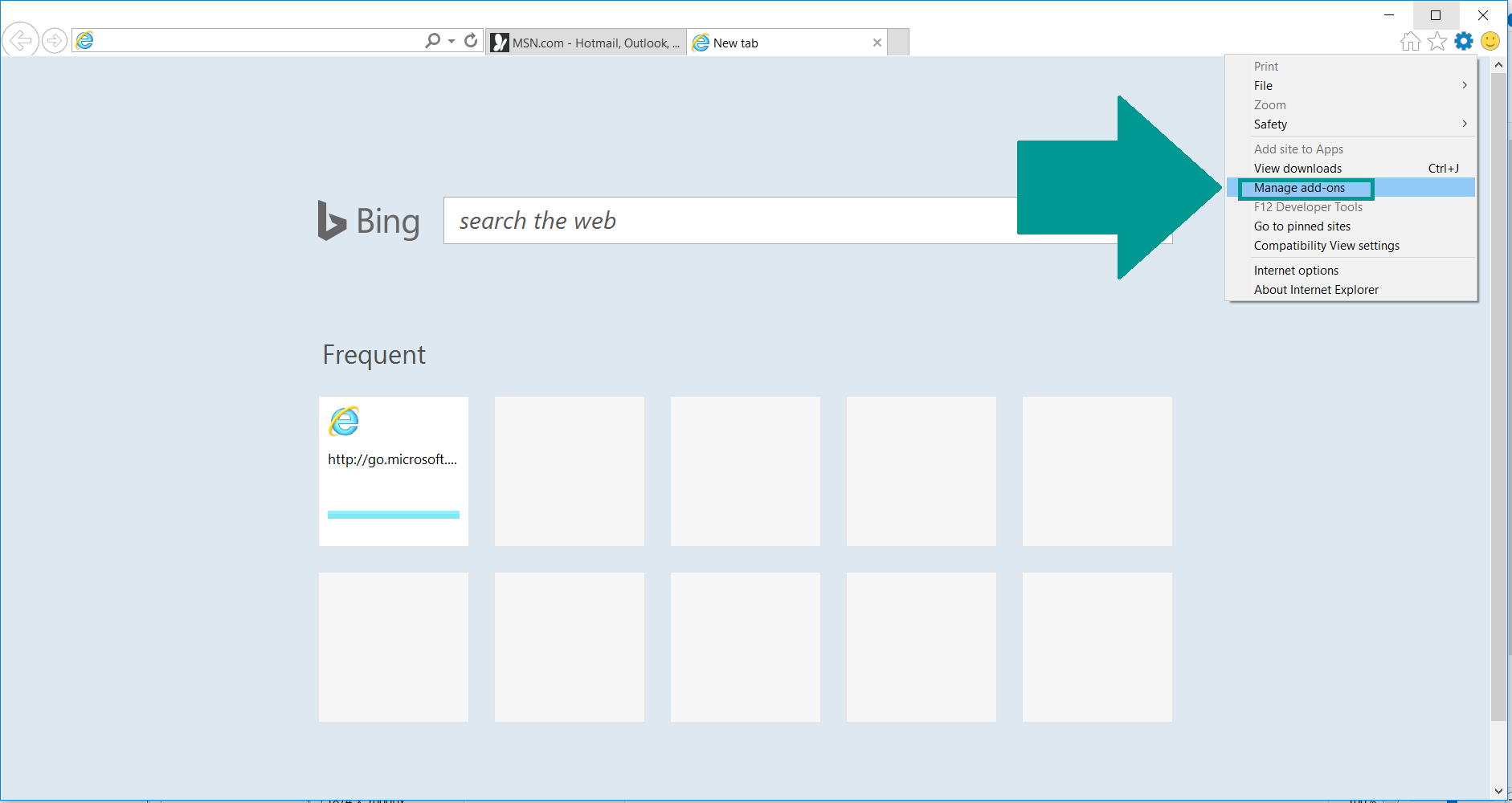
2. In the “Manage add-ons” window, bellow “Add-on Types“, select “Toolbars and Extensions“. If you see a suspicious toolbar, select it and click “Remove“.
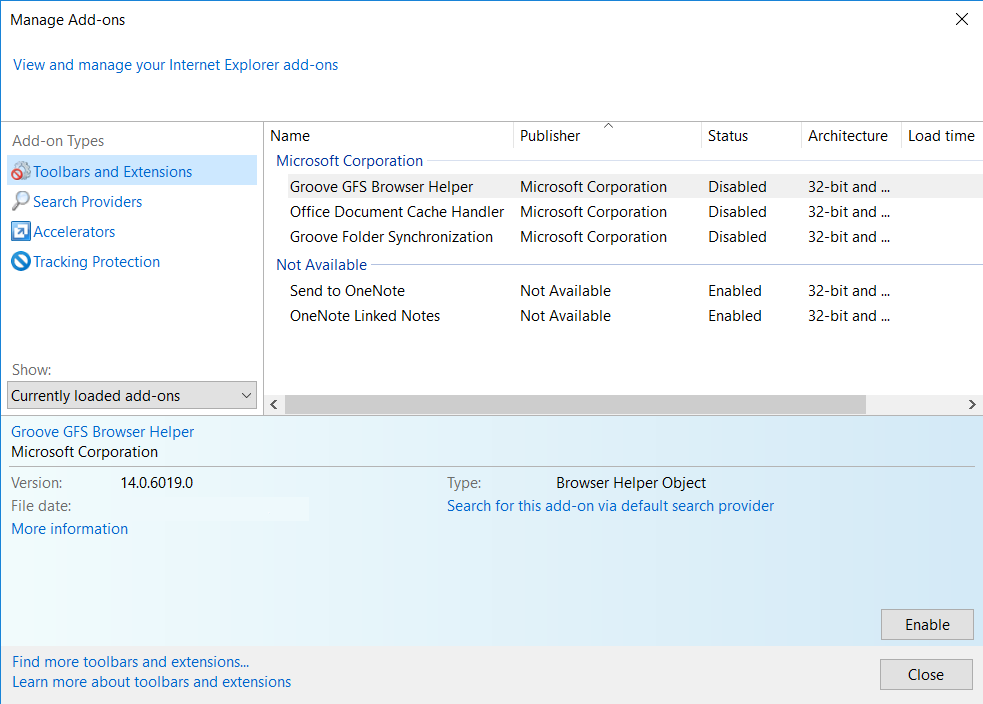
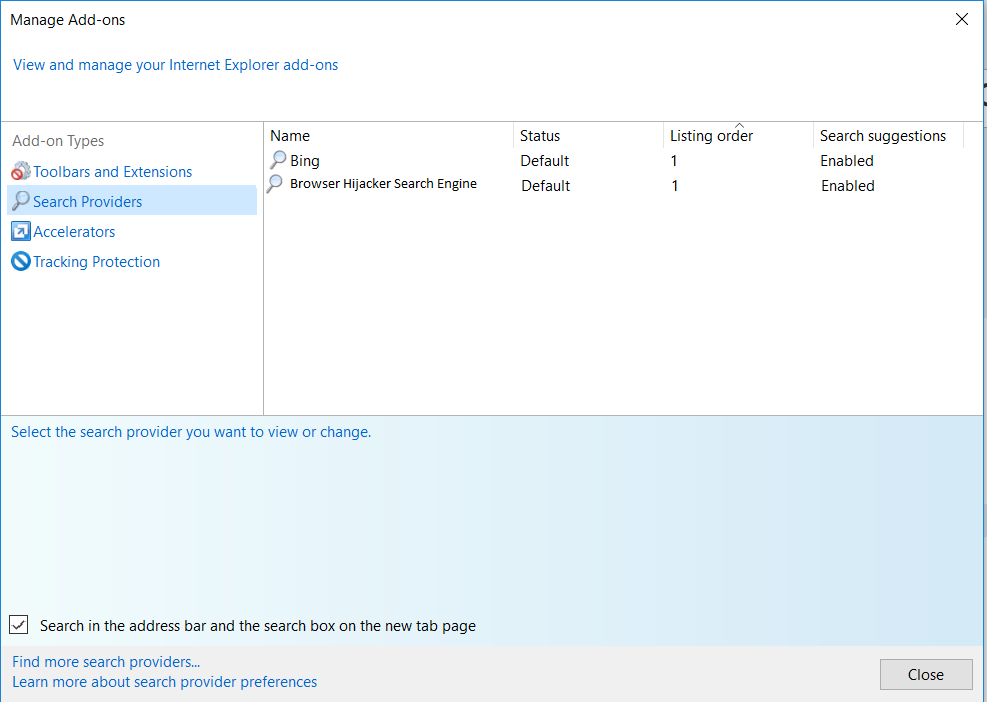
3. Then again in the “Manage Add-ons” window, in “Add-on Types“, Select “Search Providers“. Chose a search engine and click “Set as default“. Select the unknown search engine and click “Remove and Close”.
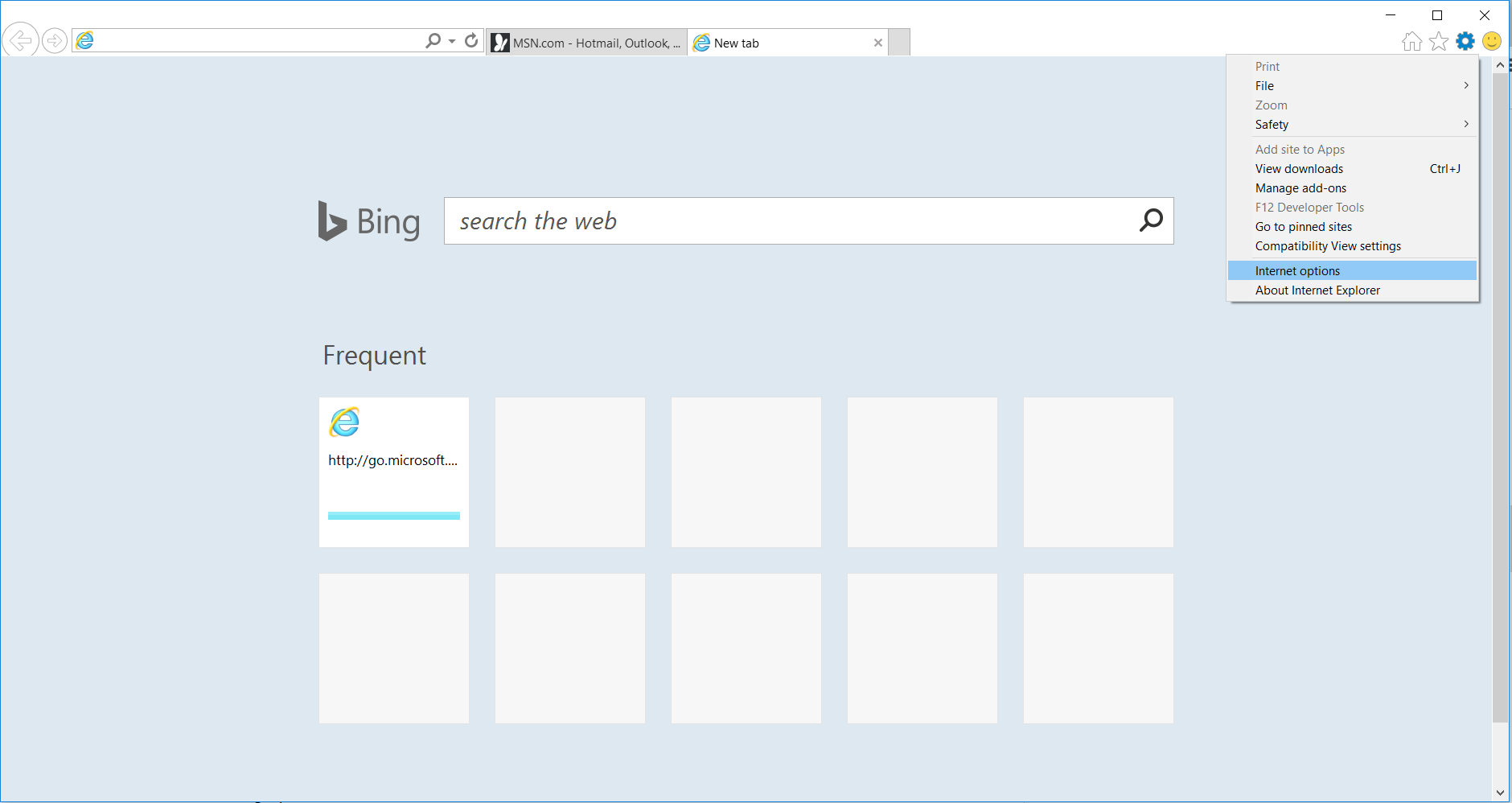
4. Open the Tools menu, select “Internet Options”.
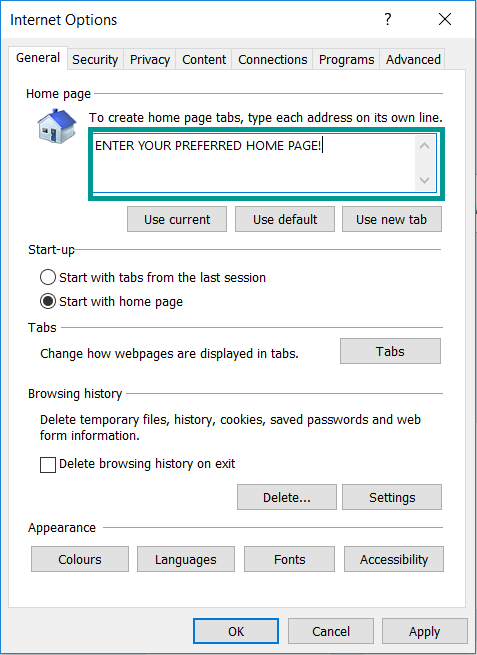
5. In the “General” tab, in “Home page”, enter your preferred page. Click “Apply” and “OK”.
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help



