The DoNotChange Ransomware is a malware threat which encrypts target user data and uses a complex naming scheme to rename the affected data, read our removal guide to learn more about it.
DoNotChange Ransomware Description
DoNotChange ransomware is one of the latest threats which have been reported by the security community. The initial security analysis shows that this is an independent creation which probably sources some of its source code based on other famous ransomware. This is apparent from some of the characteristics which have been observed in the infection process.
Once the victim has contacted the strain the virus engine automatically starts to deploy the strain to the host machine. It comes to no surprise to many of the experts that as a consequence the virus performs the usual activities associated with the typical malware – it encrypts target user data and extorts the victim for a payment.
So far the analysts have not been able to detect any advanced features bundled in the detected samples so far. However future versions might include additional modules which can render the DoNotChange ransomware even more dangerous. Examples include the introduction of a persistent environment which is used to modify key Windows settings, boot options, registry values and other important data to counter any manual removal attempts.
Other additions include the inclusion of a payload dropper and a Trojan module. They would allow the hacker operators to incur additional malware to the affected hosts and control them remotely and spy on the users activities. One of the actions that would be possible is related to the installation of dangerous browser extensions (browser hijackers) which have the capability of modifying the settings of the installed web browsers (Mozilla Firefox, Google Chrome, Microsoft Edge and Internet Explorer) – default search engine, default homepage and default new tabs page. They can be programmed to point to a hacker-operated web site and steal the stored account credentials, history, cookies and settings.
Once the virus engages its encryption engine it begins to target a predefined list of user data. It includes the following file type extensions:
.bin, .cab, .DAT, .dat, .db, .htm, .html, .jpg, .MSG, .png, .ppt, .tar, .txt, .XML, .zip and others
This shows that the DoNotChange ransomware targets the most commonly used data – archives, photos, databases, archives and configuration files. All of the affected file type extensions are renamed using the following pattern:
[original_file_name].id-[ID_victim].cry
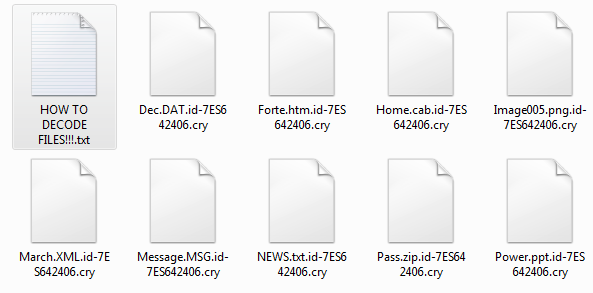
This means that the the virus engine is able to assign a unique victim ID to each host. In the most common case it is calculated by extracting key system information such as the machine ID, available hardware components and other related data.
Once the encryption process is complete the following ransomware note is shown to the victims:
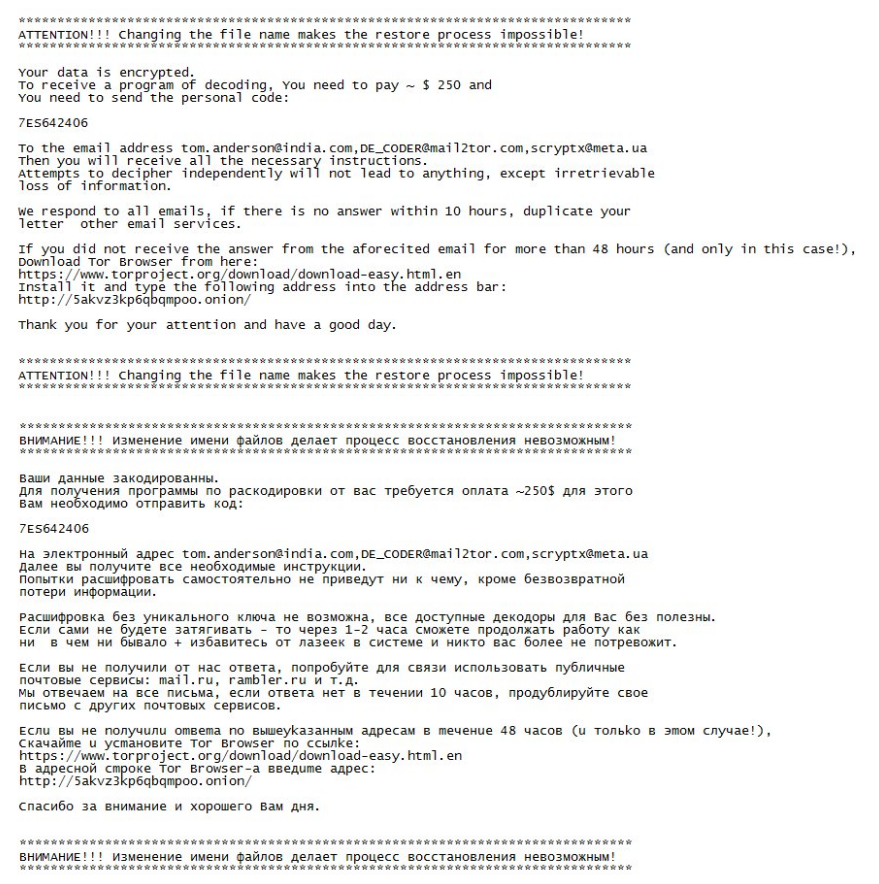
**************************************************************
ATTENTION!!! Changing the file name makes the restore process impossible!
**************************************************************
Your data is encrypted.
To receive a program of decoding, You need to pay ~ $250 and
You need to send the personal code:
7ES642406
To the email address [email protected],[email protected],[email protected]
Then you will receive all the necessary instructions.
Attempts to decipher independently wi11 not lead to anything, except irretrievable loss of information.
We respond to all emails, if there is no answer within 10 hours, duplicate your letter other email services.
If you did not receive the answer from the aforecited email for more than 48 hours (and only in this case!),
Download Tor Browser from here:
https://www.torproject.org/download/download-easy.html.en
install it and type the following address into tne address bar:
http://5akvz3kp6qbqmpoo.onion/
Thank you for your attention and have a good day.
**************************************************************
ATTENTION!!! Changing the file name makes the restore process impossible!
**************************************************************
Like other similar ransomware this one also specifies a ransomware sum which the victims are made to pay to the hackers. The operators have setup an inbox and a payment gateway site which is hosted on servers accesible through the TOR anonymous network.
The transactions are made in the Bitcoin digital currency which makes it very difficult to trace the money down to a specific individual or a group.
DoNotChange Ransomware Distribution
The limited number of detected malware campaigns does not give an accurate statistics of the primary infection method. We suspect that the hackers use the most popular scenarios. The first one involves the use of bulk email phishing messages which use social engineering tricks to try and impersonate legitimate individuals, companies, organizations and government agencies. There are several different types of these emails, depending on the placement of the virus payload. It may either be linked in the body of the text, the signature or attached directly to the message. In the past few months a lot of viruses are being distributed using infected documents with dangerous built-in scripts (macros) that deliver the payload upon interaction.
A widely used tactic is to create counterfeit download sites, search engines and malicious ad networks which redirect to the virus download. In many cases any interaction with these sites also generate revenue for the criminals. The use of infected software installers is also popular as these files are widely distributed on both download portals and P2P networks like BitTorrent.
The DoNotChange ransomware can also be installed on the target machines using direct hacker attempts and automated attacks using exploit kits.
Summary of the DoNotChange Ransomware
| Name |
DoNotChange Ransomware |
| File Extensions |
[original_file_name].id-[ID_victim].cry |
| Ransom |
250 US Dollars in Bitcoins |
| Easy Solution |
You can skip all steps and remove DoNotChange Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
DoNotChange Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
DoNotChange Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely DoNotChange Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover DoNotChange Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore DoNotChange Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



