A new crypto virus named CryptoJacky has been spotted from security researchers. Currently, it seems that criminals are targeting Spanish computer users. This article is dedicated to informing you about the most common spread methods of CryptoJacky ransomware and the massive impact it can deal on your computer in case of infection. Reaching the last paragraph you can find a how to remove guide and workable data decryption solutions.
How CryptoJacky Ransomware Can Infect the Computer
Like most crypto viruses CryptoJacky is highly believed to be part of spam email campaigns. So the malicious payloads are possible to be archived to a ZIP file or inserted into the code of an ordinary document. The infected files are most likely to be attached to an email which message commonly is written in a misleading way that invites you to interact with the attached content. If you download the file and open it, CryptoJacky ransomware infection will start taking control of your system and data. Be alert because cyber criminals are getting better at impersonating legit services that are usually part of our everyday life.
Malicious or corrupted web links are also possible to be part of criminals’ schemes for CryptoJacky ransomware distribution. Such suspicious links might be presented in:
- Spam emails – in the text body or the form of a button
- Malicious advertisements – banners, pop-ups, text, image, and even video based ads
- Spammed comments on websites with poor spam filters and configuration
- Shares and comments on social media sites from compromised profiles
- Personal messages from discredited social media profiles
CryptoJacky Ransomware Infection – Features and Impact
The original name of the threat is cryptoJacky v2.0, and the file cryptoJacky-setup.exe is the one that starts the infection process once it runs on the computer. CryptoJacky is a crypto ransomware. Thus it scans the system for particular file types in order to encrypt them via strong encipher algorithm. Whenever there is a match with the file types included in its target list, CryptoJacky utilizes AES algorithm to encrypt the file and appends a specific extension at the end of its original name.
There is no information about the exact file types that are in the scope of CryptoJacky malevolent impact yet. However, it is most likely that it is developed to corrupt commonly used files like MS Office documents, text files, images, videos, music, archives, etc.
As reported the encryption process of CryptoJacкy ransomware is carried out via a file called aescrypt.exe that is dropped on the Desktop. Probably the file is activated automatically via modifications in the Windows registries.
The extortionists offer a data decryption solution in exchange of the ransom amount of 250 EUR in bitcoins. Their message comes in the form of ransom notes that are also dropped on the Desktop. These files are:
- ransom-information.lnk
- ransom-instructions.lnk
- ransom-payment.url
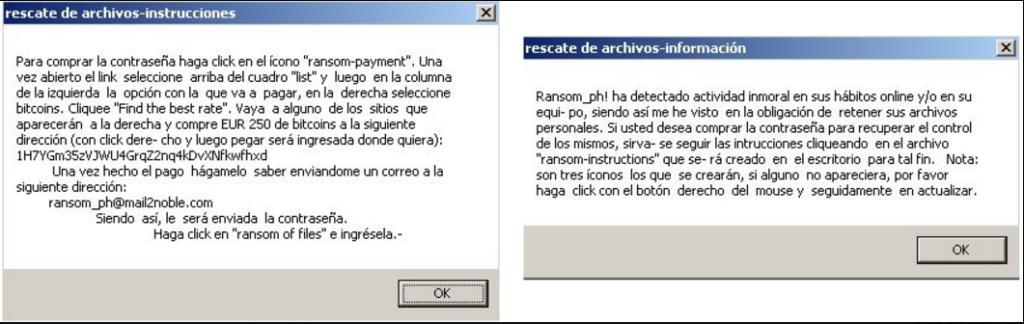
Two of them contain the following texts:
- ransom-information.lnk
Ransom_ph! ha detectado actividad inmoral en sus hábitos online y/o en su equi- po, siendo así me he visto en la obligación de retener sus archivos personales. Si usted desea comprar la contraseña para recuperar el control de los mismos, sirva- se seguir las intrucciones cliqueando en el archivo “ransom-instructions” que se- rá creado en el escritorio para tal fin. Nota: son tres íconos los que se crearán, si alguno no apareciera, por favor haga click con el botón derecho del mousey seguidamente en actualizar.
- ransom-instructions.lnk
Para comprar la contraseña haga click en el ícono “ransom-payment”. Una vez abierto el link seleccione arriba del cuadro “list” y luego en la columna de la izquierda la opción con la que va a pagar, en la derecha seleccione bitcoins. Cliquee “Find the best rate”. Vaya a alguno de los sitios que aparecerán a la derecha y compre EUR 250 de bitcoins a la siguiente dirección (con click dere- cho y luego pegar será ingresada donde quiera):
lH7YGm35zVJWU4GrqZ2nq4kDvXNfkwfhxd
Una vez hecho el pago hágamelo saber enviandome un correo a la siguiente dirección:
[email protected]
Siendo así, le será enviada la contraseña.
Haga click en “ransom of files” e ingrésela.-
The language of the notes is Spanish, so we suppose that the first attack waves will be targeting Spanish computer users. However, the malicious campaigns are probably to be expected worldwide.
The instructions include text that urges victims to make the ransom payment of 250 EUR in bitcoins in order to receive the decryption key. Once victims transfer the money, they are navigated to contact cyber criminals via sending them an email to [email protected]. Once the decryption key is received, it should be entered in the displayed field after clicking the “OK” button displayed on the ransom-instructions.lnk file.
How to Remove CryptoJacky Crypto Virus from the Infected Machine
The analysis of security researchers reveal that CryptoJacky is a sophisticated threat that implements various malicious commands and permanently damages the whole system. We advise all kidnapped users by CryptoJacky to consider the help of professional software that will contribute to best removal results and safe system performance in future.
It is not recommendable to negotiate with the cyber criminals and better stay on the state of security following the removal guide below.
The good news is that once you remove completely CryptoJacky ransomware from the system, there is chance to restore some of the encrypted data with the help of Windows functions and advanced recovery software solutions.
Summary of CryptoJacky Ransomware
| Name |
CryptoJacky Ransomware |
| File Extensions |
.(email)Unknown |
| Ransom |
250 EUR (0.23 BTC) |
| Easy Solution |
You can skip all steps and remove CryptoJacky ransomware with the help of an anti-malware tool. |
| Manual Solution |
CryptoJacky ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam emails, malicious URLs, malicious attacments, exploit kits, freeware. |
CryptoJacky Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely CryptoJacky Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



