Security experts have made a detailed analysis on the Karplux RAT malware, also known as PlugX, which has been used against important institutions in a variety of countries.
The most famous example of a Korplux attack is the intrusion against 400 thousand members of Vietnam Airlines.
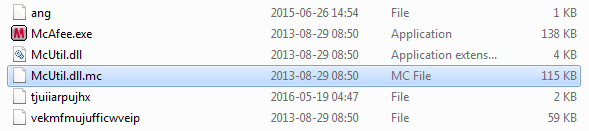
Korplux Fools Victims by Pretending to Be an Antivirus
The spyware has a modular structure and pretends to be an executable file of McAfee antivirus. The criminal developers have used the original certificate to sign the executable which makes it harder to detect. The DLL file that is present with the executable, however, is not signed, and this is what is used for the hijack.
Upon successful execution, the spyware runs silently without alerting the users of its presence. Malicious code is entered into the svchost system process. The code modification changes the default directory of the hanger to the spyware location. The malware then continues to scan the local area network for other computer hosts. Attempts to connect the C&C servers are also made.
The core spy bot is pretty well hidden in a DLL file that is obfuscated in shell code. Experts state that Trojans often pose as famous and legitimate applications as effective means of distribution.
Korplux is a good example of malicious programming. The payload is well hidden and presents a real threat to computer users worldwide, due to the stealth functions that it exhibits.