We have been notified of the discovery of Fluffy-TAR ransomware, a new malware which can be removed by following our removal guide.
Fluffy-TAR Ransomware Description
Security analysts have reported a new infection which is currently spreading across computers worldwide. The force behind it is the Fluffy-Tar ransomware which is made by an unknown hacker. According to the initial analysis it does not feature code from other malware families which makes it dangerous. The researchers need to identify all characteristics of the threat before they can make an accurate fingerprint which is used by the specialist anti-virus applications. Fortunately our removal guide gives detailed information about how you can remove the threat by yourself – either by the use of an easy solution or by attempting manual removal.
According to the virus researchers it is still under active development and we can only describe the current iteration of the virus. Even though it only features the basics the virus is capable of inflicting much damage to the infected computers. As it appears the current iteration of samples follow the usual methods of installation which are described in our guide.
When the virus infiltrates the system it follows a predefined procedure in several steps:
- Information Extraction – The virus engine extracts system information from the machine that is both used for the encryption process as parameters insertion. The data is also sent to the remote attackers via a secured network connection. Some of the collected information includes: the active computer name, supported and installed languages, volume information, the cryptographic unique machine ID (GUID) and detailed system hardware data.
- Settings Manipulation – The next step is to modify key Windows settings which makes it possible for the virus to affect the host in a more effective way. Changes include software policy and certificate settings. In addition a .NET runtime environment is engaged to execute the dangerous actions that follow.
- Registry Monitoring – An important feature of these types of ransomwares is that they can actively monitor registry values for changes. This is a tactic used to create a persistent environment and prevent manual removal attempts. The virus actively prevents any type of modification by the users unless a quality anti-malware solution is used to delete the threat.
- Network Communication – Information about the compromised host is sent to remote C&C servers via a secured connection.
- Encryption Process – When the environment has been prepared the virus starts the encryption process.
After the processes are complete the encryption engine is initialized. This module uses a strong encryption algorithm (cipher) to encrypt a predefined list of target user file type extensions. The malware samples detected so far process the following:
.3fr, .7z, .abu, .accdb, .ai, .arp, .arw, .asp, .aspx, .ass, .asset, .ava, .avi,.bas, .bay, .bdcr, .bdcu, .bdd, .bdp, .bds,
.bikey, .blend, .bmp, .bpdr, .bpdu, .bsdr, .bsdu, .c, .cc,.cd, .cdr, .cer, .class, .com, .config, .cpp, .cr2, .crt, .crw, .cs,
.csv, .cxx, .db, .dbf, .dbx,.dcr, .dd, .dds, .der, .dng, .doc, .docm, .docx, .DTD, .dwg, .dxf, .dxg, .eps, .erf, .fdb, .forge,
.gdb,.gif, .groups, .gsd, .gsf, .h, .hpp, .htm, .html, .ims, .indd, .iss, .jar, .java, .jpe, .jpeg, .jpg,.js, .jsp, .kdc, .key,
.kwm, .lua, .m, .md, .mdb, .mdf, .mef, .mp3, .mpg, .mrw, .msg, .nef,.nrw, .oab, .obj, .odb, .odm, .odp, .ods, .odt, .orf, .ost,
.p12, .p7b, .p7c, .pab, .PAS, .pas, .pdb,.pdd, .pdf, .pef, .pem, .pfx, .php, .pl, .png, .ppk, .ppt, .pptm, .pptx, .ps, .psd, .pst,
.psw, .ptx, .pwm, .py, .r3d, .raf, .rar, .RAW, .raw, .rgx, .rik, .rm, .rtf, .rw2, .rwl, .safe, .sav, .sln,.sql, .srf, .srw, .swf,
.swift, .tex, .txt, .vcf, .vsd, .wb2, .wpd, .wps, .xcf, .xlk, .xls, .xlsb,.xlsm, .xlsx, .xml, .zip
From this information we can conclude that the virus affects several different categories of data:
- Archives – Compressed files.
- Audio files – Music and audio files.
- Documents – Popular document file types, they include both rich text, spreadsheets and other commonly used data.
- Application-Specific Files – Files used by specific software products.
- Images – Various types of image files – raster and vector formats.
- Source Code – Programmer source code in various formats and languages.
- Video Files – A selection of some of the most commonly used video file type extensions.
- Configuration Files – Files used by the operating system or applications for storing important configuration settings and variables.
All of the affected received the lock75 extension. The Fluffy-Tar ransomware uses a screenlocker which prohibits ordinary user interaction with the computer until the threat is removed completely from the infected machine.
A ransomware note is displayed which reads the following:
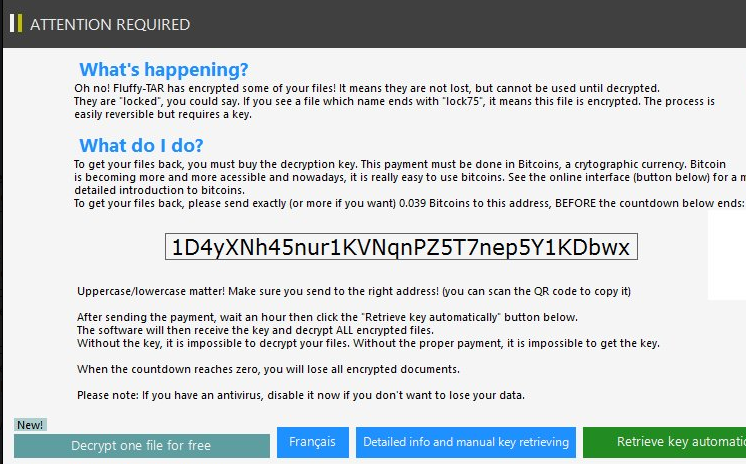
What’s happening?
Oh no! Fuffy-TAR has encrypted some of your files! It means they are not lost, but cannot be used until decrypted.
They are “locked”, you could say. If you see a file which name ends with “lock75”, it means this file is encrypted. The process iseasily reversible but requires a key.
What do I do?
To get your files back, you must buy the decryption key. This payment must be done in Bitcoins, a cryptographic currency. Bitcoin is becoming more and more acessible and nowadays, it is really easy to use bitcoins. See the online interface (button below) for a more detailed introduction to bitcoins.
To get your files back, please send exactly (or more if you want) 0.039 Bitcoins to this address, BEFORE the countdown below ends:
[1D4yXNh45nur1KVNqnPZ5T7nep5Y1KDbwx] Uppercase/lowercase matter! Make sure you send to the right address! (you can scan the QR code to copy it)
After sending the payment, wait an hour then click the “Retrieve key automatically” button below.
The software will then receive the key and decrypt ALL encrypted files.
Without the key, it is impossible to decrypt your files. Without the proper payment, it is impossible to get the key.
When the countdown reaches zero, you will lose all encrypted documents.
Please note: If you have an antivirus, disable it now if you don’t want to lose your data.
[Decrypt one file for free] [Francais] [Detailed info and manual key retrieving] [Retrieve key automatically]
If the victim chooses to interact with the virus they are forwarded to the payment gateway which is located on the TOR anonymous network. The hacker(s) behind the virus has/have made a two-language version of the site, available in English and French. The interesting thing about the payment gateway is that automatically uses the transferred unique infection ID to display a time limit counter. This is a common extortion tactic used to further pressure the victims into paying the designated fee.
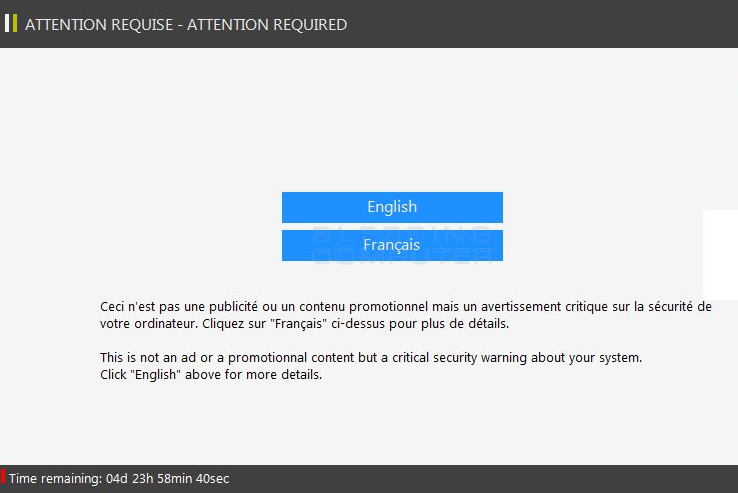
As it appears the ransomware can be customized to display a varying fee according to the targets, the analyzed samples show that the ransom fee was adjusted to 0.039 Bitcoins in the latest campaign. This is about 45 US Dollars in equivalent which is a small amount of money in comparison to other viruses of this kind.
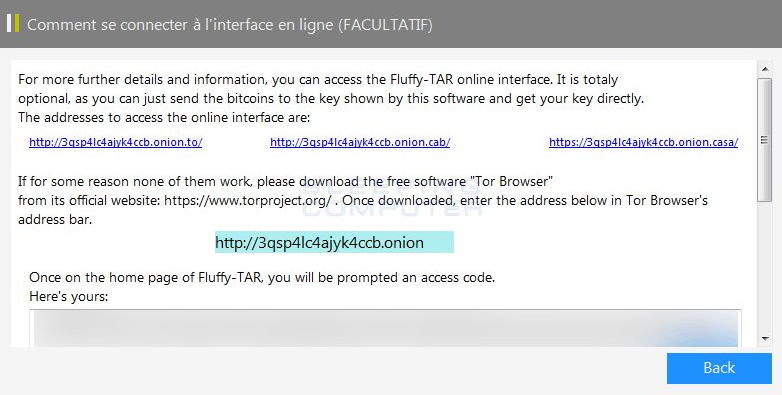
Its interesting to note that the creators of the Fluffy-Tar ransomware have created several different payment gateways where the transactions can be made. All of them are available on the TOR anonymous network and for the victims convenience a window with instructions has been made. Here is an excerpt:
For more further details and information, you can access the Fluffy-TAR online interface. It is totally optional, as you can just send the bitcoins to the key shown by this software and get your key directly.
The addresses to access the online interface are:http://3gsp4lc4ajyk4ccb.onion.to/ http://3gsp4lc4jyk4ccb.onion.cab/ http://3gsp4lc4ajyk4ccb.onion.casa/
If for some reason none of them work, please download the free software “Tor Browser”
from its official website: https://www.torproject.org/. Once downloaded, enter the address below in Tor Browser’s
address bar.http://3qsp4lc4ajyk4ccb.onion
Once on the home page of Fluffy-TAR, you will be prompted an access code.
Here’s yours.
XXXXXXXX
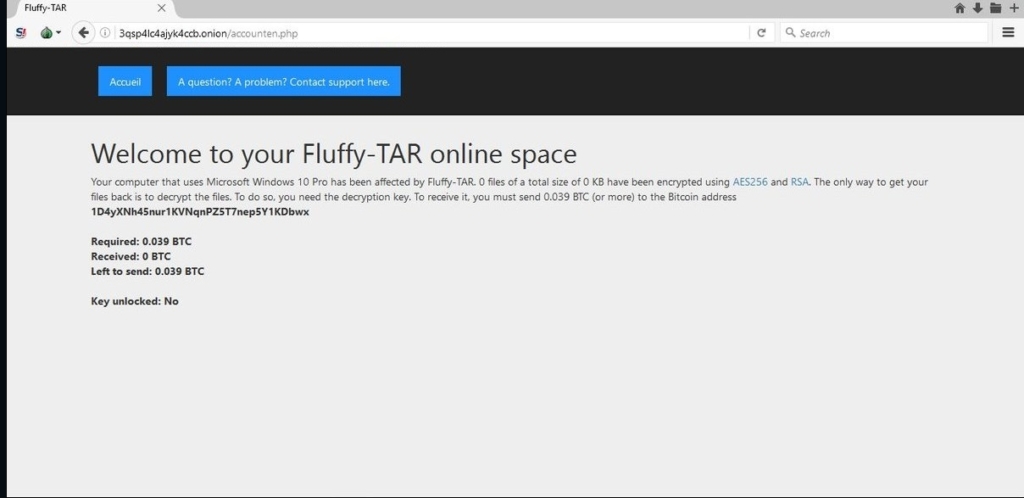
A personal web site is created for every affected host. It displays generic information which is populated by the harvested information. An example page reads the following:
Welcome to your Fluffy-TAR online space
Your computer that uses Microsoft Windows 10 Pro has been affected by Fluffy-Tar, 0 files of total size of 0 KB have been encrypted using AES256 and RSA. The only way to get your files back is to decrypt the files. To do so, you need the decryption key. To receive it, you must send 0.039 BTC (or more) to the Bitcoin address
1D4yXNh45nur1KVNqnPZ5T7nep5Y1KDwxRequired: 0.039 BTC
Received: 0 BTC
Left to send: 0.039 BTC
Key Unlocked: No
This page also gives access to a contact site which uses a live chat function which is used to communicate with the hackers. The personal page associated with the victims is dynamically updated with several variables:
- Extracted System Information – The current iteration shows the version of the operating system.
- Encrypted Files – The virus engine can report the number of affected files and their size.
- Used Cipher – The page shows the cipher which has been used by the ransomware.
- Ransomware Sum Status – This field shows the amount of Bitcoins transferred to the Bitcoin address.
Fluffy-TAR Ransomware Distribution
The malware infections have been spotted all across the world. At the moment there are several running distribution servers available in Romania and Sweden. There are several different infection methods which are used by the ransomware.
One of the most popular ways of getting infected with it is the interaction with infected spam emails. The hackers send out bulk messages which feature social engineering tricks (phishing) that try to persuade the recipients into opening up file attachments, hyperlinks or infected documents. In the most common case these emails are made to look similar to legitimate messages sent out from well-known individuals, companies or government institutions. One of the dangerous scams associated with this tactic is the use of infected documents that pose as files of user interest such as invoices, letters and contracts. When they are opened the victims is presented with a screen that requests a macro script to run. if they execute it the virus is automatically deployed to their system.
Other kinds of malicious scripts which are used as payload droppers include browser hijackers. They are browser extensions which upon installation misconfigure the settings of the installed web browsers, usually they are made to impact the most commonly used ones – Mozilla Firefox, Google Chrome, Internet Explorer and Microsoft Edge. The basic settings are changed to point to a hacker-controlled site or directly to the virus, the modifications impact the default home page, default search engine and the new tabs page. In addition the hackers may extract the data from the applications which can be stored account credentials, cookies, web history and etc.
Hacker-controlled download sites, portals and malicious ad engines can also deliver the Fluffy-TAR ransomware to the victims. The virus may be bundled in software installers that are integrated with popular software and distributed on these rogue sites. The hackers may also opt to use various redirects and ads that also generate income for them.
So far no direct hacker attacks using exploit kits have been detected but that is a possibility in the future where the strain may be improved further.
Summary of the Fluffy-TAR Ransomware
| Name |
Fluffy-TAR Ransomware |
| File Extensions |
lock75 |
| Ransom |
0.039 Bitcoins |
| Easy Solution |
You can skip all steps and remove Fluffy-TAR Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Fluffy-TAR Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Fluffy-TAR Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Fluffy-TAR Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Fluffy-TAR Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Fluffy-TAR Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



