The Enjey ransomware is a new malware which has been recognized as being descendant from the RemindMe ransomware, read our removal guide to learn more about it.
Enjey Ransomware Description
The security community has alerted us of a new discovery – the Enjey ransomware. According to the initial analysis it is descendant of the RemindMe ransomware threat. At the moment we do not who is responsible for its creation – hacker or hacker collective.
What we know is that it follows the usual behavior associated with similar viruses – it uses an encryption cipher to target various user data and then extort the victims for a ransomware payment.
Upon infection the virus fist contacts the remote C&C servers and initiates a network connection to report of the compromised host. The Enjey ransomware reports information about the system to the attackers such as the computer’s name and local settings.
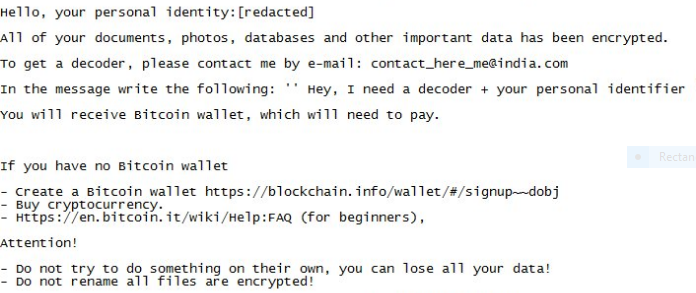
When the encryption process is started the virus affects the most popular file type extensions associated with documents, photos, videos, configuration files, databases and etc. When this is done a ransomware note is crafted (in a README_DECRYPT.txt file ) and shown to the user. It reads the following message:
Hello, your personal identity:[redacted] All of your documents, photos, databases and other important data has been encrypted. TO get a decoder, please contact me by e-mail: [email protected] In the message write the following: ” Hey, I need a decoder + your personal identifier You will receive Bitcoin wallet, which will need to pay.
If you have no sitcom wallet – create a sitcom wallet https://blockchain.info/wallet/#/signup—dobj – Buy cryptocurrency. – Https://en.bitcoin.it/wiki/Help:FAD (for beginners),
Attention!
– Do not try to do something on their own, you can lose all your data! – Do not rename all files are encrypted!
All affected data receive the following extension: [email protected]. The ransomware note is fairy typical for these types of viruses – it scares the users and attempts to trick them into paying the ransomware sum. Do not attempt to pay the hackers. There are several case scenarios which have been reported by the experts:
- The Criminals Receive The Payment And Do Not Restore The Files – As the payments are done via the Bitcoin currency they are pratically anonymous and untraceable. In the majority of cases the hackers receive the payment and then do not answer or restore the files of the victims.
- Partial Restoration – The hackers restore some of the user’s data to show that they have begun decryption. However they do not restore everything.
- Further Malware Infections – The hackers can introduce additional threats to the infected hosts.
These are the reasons why we recommend that everyone use a quality anti-malware tools to remove existing infections and protect their computers.
Enjey Ransomware Distribution
The captured Enjey ransomware samples are still very little in volume and the security experts cannot judge which are the primary infection methods.
The following options are the probable sources as they are the most popular ones:
- Email Scams – Computer hackers typically use phishing messages to infect the victims via popular scams. The emails pose as being from a well-known company or a government institution. The viruses may either be attached directly to the message or linked somewhere in the body.
- Download Sites and BitTorrent trackers – Various hacked or hacker-controlled sites are a popular source of viruses. BitTorrent trackers are notorious for distributing them.
- Exploit Kits and Trojans – Direct attacks can institute additional malware installations such as the Enjey ransomware.
- Dangerous Scripts and Browser Extensions – Malicious web scripts available on hacked sites, ad networks and browser hijackers can lead to a serious infection. The dangerous browser extensions (also known as hijackers) can infect the host computer with all sorts of viruses due to their behavior. They change the default search engine, new tabs page and homepage to point to a hacker-controlled site or portal.
Summary of the Enjey Ransomware
| Name |
Enjey Ransomware |
| File Extensions |
[email protected] |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove Enjey Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Enjey Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Enjey Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Enjey Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Enjey Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



