A massive corporate espionage campaign started in March 2016. A group dubbed Operation Ghoul was responsible for breaching into 130 companies worldwide. The activities of the group increased in late June of this year. Operation Ghoul mainly targeted industrial, engineering and manufacturing companies in 30 countries around the globe. Education, trading, tourism, shipping, pharmaceutical, and firms from other sectors were also victims of Operation Ghoul.
What Constituted the Operation Ghoul Espionage Campaign?
The main goal of the group seems to be financial profit. Operation Ghoul likely stole secret information from firms and sold them to the competition. The targeted organizations were mostly small to medium sized; that is to say that the number of employees ranges from 3 to 300.)
Kaspersky Lab detected the Operation and reported it on their SecureList site. They added also added an amusing definition of the world Ghoul, saying that: “the term is sometimes used to describe a greedy or materialistic individual.” The attackers were aiming at higher-ups in the hacked firms, like CEOs, managers, and engineers. The organizations were mostly located in Spain, UAE, India, Pakistan, and Egypt, though there are some firms in UK, Germany, Switzerland, and other countries that were also hacked.
How Did Operation Ghoul Breach Security?
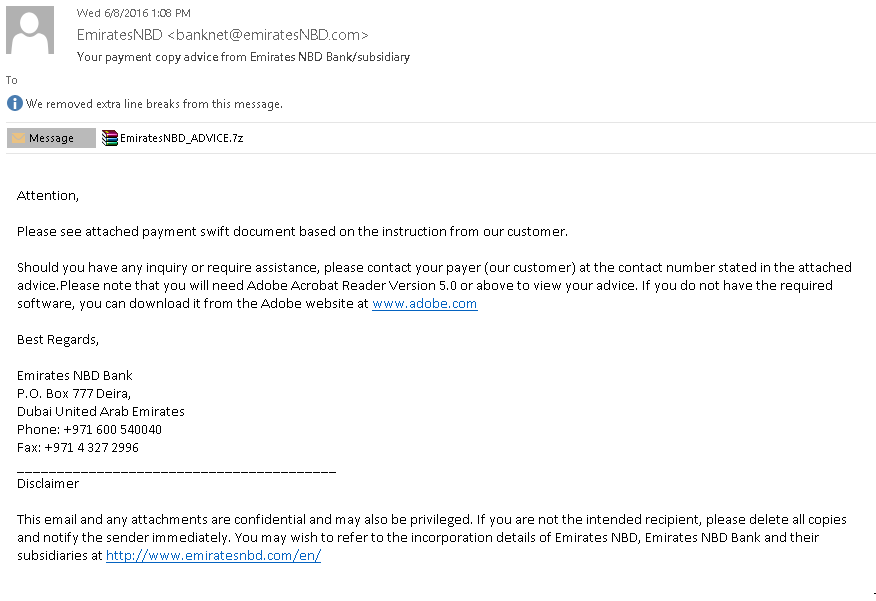
The group breached the security of the firms by sending emails infected with malware. The hacked masked the emails to look like they were sent from a bank. As usual, the infected emails contained malicious files attached or phishing links.
The malicious attachments contained a malware executable (EmiratesNBD_ADVICE.exe) using MD5 malware hashes:
fc8da575077ae3db4f9b5991ae67dab1
b8f6e6a0cb1bcf1f100b8d8ee5cccc4c
08c18d38809910667bbed747b2746201
55358155f96b67879938fe1a14a00dd6
and email hashes:
5f684750129e83b9b47dc53c96770e09
460e18f5ae3e3eb38f8cae911d447590
Picture of the Infected Emails:
The Files Contained Spyware
After all, their goal was to collect data, and their tools were right for the job. The malware could collect a massive amount of data. It used keystroke logging to collect everything typed on the infected PC’s keyboard, like accounts and passwords. It also collected malware that can collect information from FileZilla FTP servers, browser history, and accounts, data from messaging apps, email clients, and others. The attackers could steal information from most mainstream operating systems; Windows, Mac OS X, Android, Ubuntu, and iOS. The crooks based the spyware on the popular HawkEye malware.
The Operation Ghoul hack and cyber-security
The huge amount of hacked firms shows that nobody is safe from hacking, even small firms. It’s a fact we’ll have to put up with until everyone understands how important cyber-security is. Using cyber-security software is a must in our day and age. Malicious email attachments are a very avoidable if users are careful. No legitimate bank is going to send you important information in an archive file in the 7z or .rar formats. It’s troubling that the Operation Ghoul campaign was effective against higher ups in these companies.



