TelNet ports are often considered old-fashioned and even obsolete, having been replaced by the SSH protocol. However, the attacks on TelNet ports almost double those of SSH.
Telnet and Botnets
According to data collected by CZ.NIC from a honeypot server research:
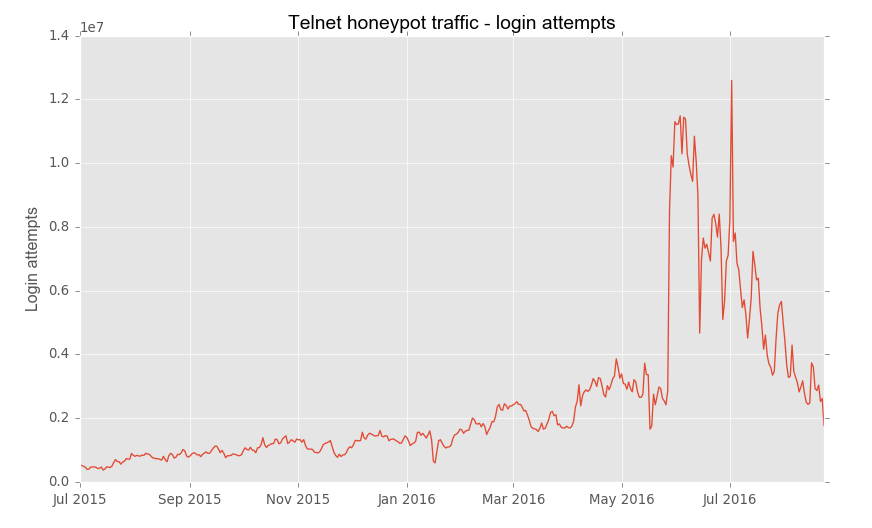
When we created our first honeypots for the Turris project, we started with SSH and Telnet, because both offer interactive console access and thus are very interesting for potential attackers. But SSH was our main goal, while Telnet was more of a complimentary feature. It came as a great surprise to discover that the traffic we drew to the Telnet honeypots is three orders of magnitude higher than in the case of SSH (note the logarithmic scale of the plot below).
Their monitoring shows that the number of attackers is up to 40, 000 unique IPs per day. This activity is likely due to a new botnet attackers, though it remains unclear.
Locations of the Botnet attacks
The botnet was active in countries around the globe, China, Russia, Turkey, Brazil, Vietnam, India, South Korea, and others.
Most of the IP addresses used in the botnet attack belonged to security cameras, DVRs, routers, though any device with that has embedded servers can be used.
The Botnet’s Login Attempt Stats:
Botnets Attacks as a Whole
Devices are becoming more and more connected to the internet, and botnet creators take full advantage of that. Many devices that have access to the Internet can be used for IoT botnets. Your camera or router can be used by hackers for botnet attacks if you’re not careful. Bedřich Košata from the NIC.CZ post says:
I recommend taking some time to review which of your ‘smart’ devices are accessible from the Internet and consider limiting access them by using a firewall.
Take care to avoid your devices falling into the hand of cybercriminals. As mentioned above, try to set up a firewall and keep your devices up to date. Doing this won’t just help you, it’ll also prevent the crooks from attacking others using your system.



