Computer hackers constantly create new malware and clever infiltration campaigns. Facebook as one of the most popular sites on the Internet has become a platform for spreading all kinds of viruses. In this article, we present the top 10 Facebook virus attacks and how you can protect yourself from danger.
1. The Spam Post
This is one of the most widely used tactics. The hackers create spam posts in either their Facebook timeline or group. In the majority of cases they contain links that redirect to a virus hosted on a third party site. The SPAM posts can be of any popular types — text, graphics or a combination of both elements. In many cases the hackers can also input smileys, emoticons and emojis to further capture the interests of the users.
The hackers create spam posts in either their Facebook timeline or group.

2. Messenger Phishing Attempt
The hackers utilize social engineering tricks that resemble those used in their classic email campaigns. The Facebook virus delivery is dependent upon the gullibility of the victims. The messages can impersonate companies or services that the users may use. They come from pages and user accounts that have hijacked the legitimate design elements and elements of the impersonating companies.
The hackers utilize social engineering tricks that resemble those used in their classic email campaigns.
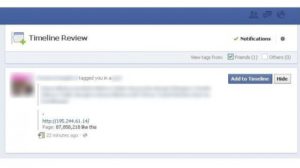
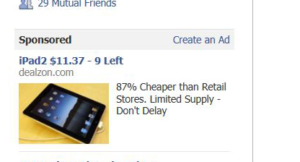
3. Ad Redirects
Some of the ad networks that operate from within the Facebook social network can lead to a virus attack. Such campaigns usually pose as legitimate sources for products or services, in this case they lead to hacker-controlled download portals. The links usually advertise services or products with a very low price.
Some of the ad networks that operate from within the Facebook social network can lead to a virus attack.

4. Malicious and Fake Apps
Computer hackers can create counterfeit apps that pose as legitimate ones. They may have similar names and design which is used to trick unsuspecting victims into using them. Interaction with them can lead to a dangerous virus infection. In some cases the advertised applications may be infected payload carriers — legitimate application setup files that have been infected with virus code. When they are installed the actual software will be installed
Computer hackers can create counterfeit apps that pose as legitimate ones.
5. Infected Images
Several large-scale spam campaigns were used to deliver dangerous malware such as the Locky ransomware via the Facebook social network. Spam users used image files that were actually compressed or binary files that lead to a dangerous infection. Advanced infections can include steganography-infected viruses — hidden threats that are activated once the image is downloaded on the computer.
Several large-scale spam campaigns were used to deliver dangerous malware such as the Locky ransomware via the Facebook.
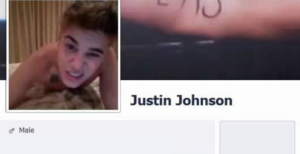
6. Impersonating Profiles
Hackers extract profile data from existing users and create fake identities. When a trigger is signaled they start to send out messages to contacts that contain links or attachments containing all kinds of viruses. The fake profiles can be an exact copy of the original ones by taking all public contents and placing them in the exact same way.
Hackers extract profile data from existing users and create fake identities.
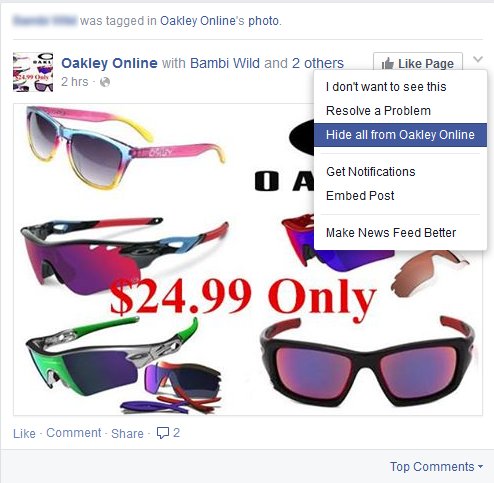
7. Virus Tags
Various hacker-controlled profiles tag multiple users with scam messages or links that lead to hacker-controlled download sites where viruses are hosted.
Various hacker-controlled profiles tag multiple users with scam messages or links that lead to hacker-controlled download sites. This can be countered by disallowing public tagging from the settings menu.

8. Counterfeit Facebook Browser Extensions
Hackers have created various browser hijackers that pose as legitimate extensions that feature Facebook integration or added features. When installed on the victim computer they endanger the users privacy and can infect the hosts with all kinds of viruses. These browser extensions are typically advertised using elaborate descriptions and uploaded to the relevant repositories with fake user reviews and developer credentials.
Hackers have created various browser hijackers that pose as legitimate extensions that feature Facebook integration

9. Facebook Notification Virus
Over the years we have seen several different viruses and scripts that create false notifications. If the victims interact with it they are lead to a hacker-controlled instance which delivers viruses to their computers. Malicious apps and scripts can lead to abuse of the Facebook notifications.
Over the years we have seen several different viruses and scripts that create false Facebook notifications.

10. In-Video Virus Scripts
Dangerous fake videos posted on groups, profiles and messages can lead to ransomware infection. The payloads can trigger a multi-stage infection or a single delivery of a virus instance.
Dangerous fake videos posted on groups, profiles and messages on Facebook can lead to ransomware infection. The reason for this is that various multimedia content, including videos, can include malware scripts. The payloads can trigger a multi-stage infection or a single delivery of a virus instance.
The top 10 Facebook virus attacks show that practically everyone using the social network is at a constant risk of infection. Various kinds of malware, including the most sophisticated ransomware strains, use the site for spreading to potential victims. Stay protected by using a quality anti-malware solution. It can both protect the computers and remove any active infections with a few mouse clicks.
SpyHunter anti-malware tool will diagnose all current threats on the computer.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter