2016 could be marked as
“The Year of Ransomware“
considering the uptrend in its dissemination and successful infections.

On an average, Ransomware infects 30,000 to 35,000 home and office devices in a month. The peak of ransomware infections has been reached in March 2016 when 56,000 devices were hit by the threat.
Cyber criminals have gained approximately $209 million for the first quarter of the year. At that rate, the ransomware income is expected to reach about a $1 billion in 2016.
Ransomware Findings
DEFINITION
Type of malware that blocks access to a system, device, or file until a ransom is paid.
RANSOM
0.1-100 BitCoins (BTC)
TYPES OF RANSOMWARE
Locker ransomware (computer locker)
Crypto ransomware (data locker)
AVERAGE NUMBER OF INFECTIONS PER MONTH
30 000 – 35 000 devices
Knowing the facts, our mission is to provide timely and reliable ransomware protection and removal help. Our manual guide will help you to remove easily all sorts of ransomware threats and restore encrypted data by yourself.

Loading…Ransomware Manual Removal Instructons
By following these instructions you can remove active infections from your computer. Please note that they do not guarantee 100% success as the more advanced threats can only be removed only by using an advanced security utility.
- 1. Start The Computer In Safe Mode With Networking
- Safe Mode is a special environment where only the minimal operating system programs, utilities and functions are executed. By using it you can isolate malicious processes and registry values from running on your computer. Follow our video guide
- 2. Show The Hidden Files
- In Windows 7
- In Windows 10
Open My Computer/This PC
-
– Click on the “Organize” button.
– Select “Folder and search options”.
– Select the “View” tab.
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option.
- – Open the “View” tab.
– Mark “Hidden items” option.
– Click “Apply” and then the “OK” button.

- Press the following keyboard combination: CTRL + SHIFT + ESCAPE
- This will open the Task Manager application. Navigate to the “Processes” tab.
- When you find the suspicious process right click on it and select “Open File Location”.
- Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”.
- Navigate to the folders where the process resides and delete it.
3. Enter The Windows Task Manager and Stop The Malicious Processes
Reduce the time and effort you spend during the removal process with the help of a removal tool.
SpyHunter’s free system scanner will analyze all computer files and show if malware is detected. After scan you will see detailed information about each malicious entry so that you can find and remove it manually.
- 4. Restore The Windows Registry
- Once again press the keyboard combination of Windows Key + R.
- In the dialog box, write “regedit” (without the inverted commas) and hit the Enter Key.
- Press the CTRL + F keyboard combination and then write the malicious name in the search type field to locate the malicious executable.
- In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys!
For More Information on Repairing Corrupted Windows Registry Entries Click Here
How to Recover Encrypted Files
We recommend that you use professional data recovery software for best results in recovering affected user data.
- • Stellar Phoenix Data Recovery
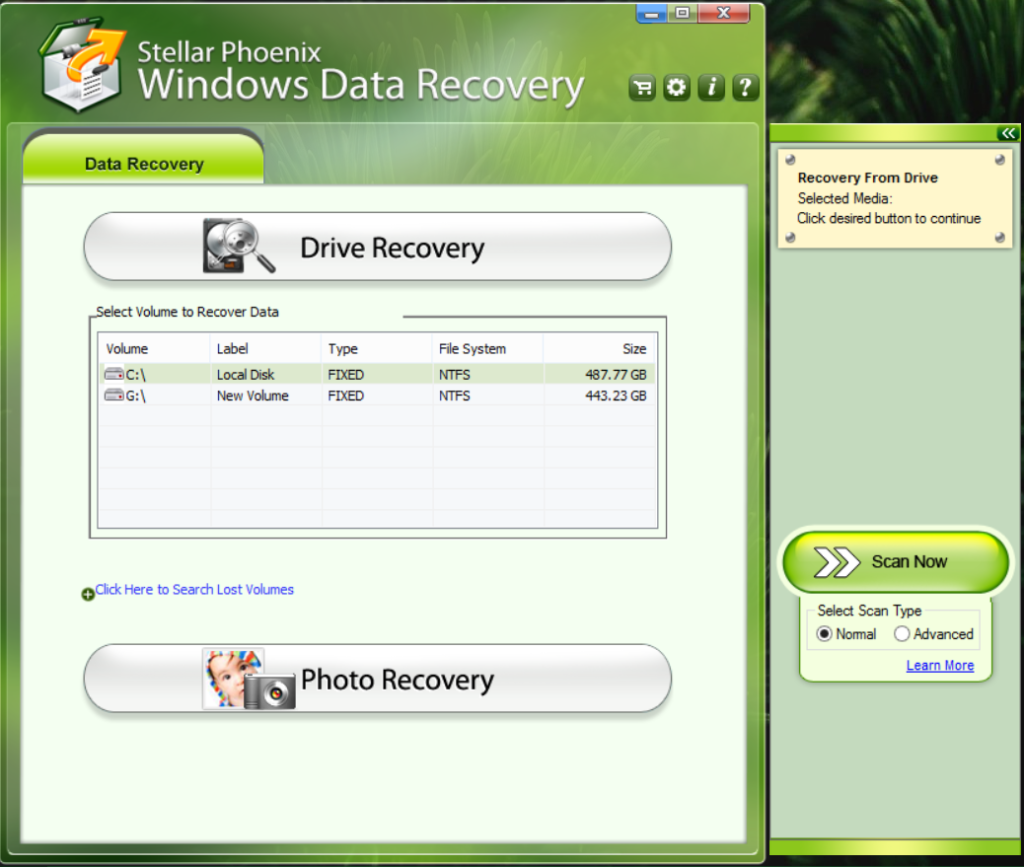
- It is a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- • Data Recovery Pro by ParetoLogic
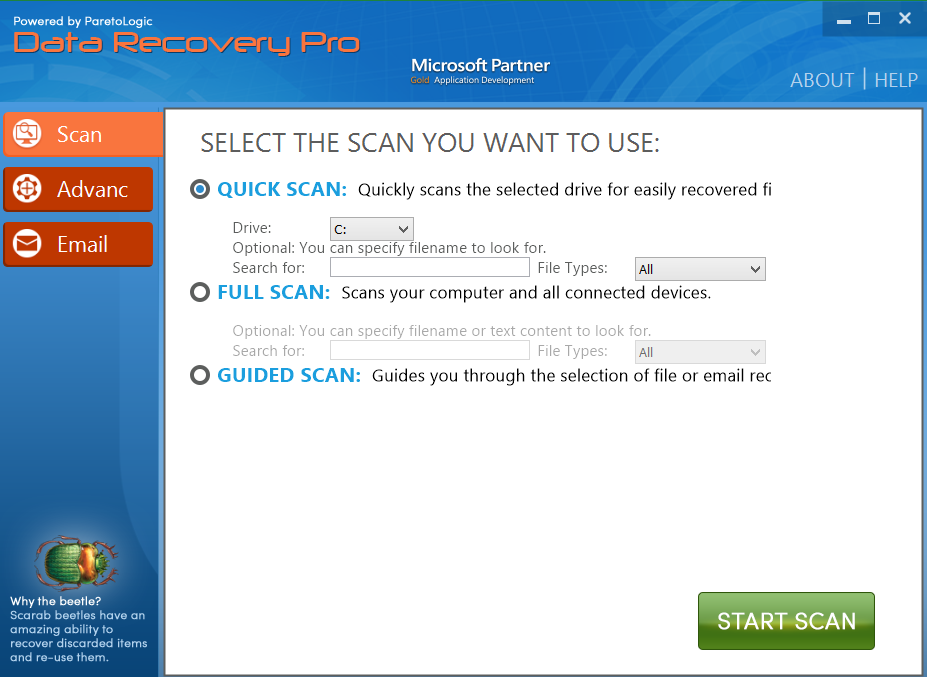
- Data Recovery Pro is a Microsoft Partner program that is very powerful. It can recover not only local files but also deleted emails and connected drives.
- • Free decryptor utilities
- If you are sure that you can identify the individual ransomware strain you can use a free decrypter utility to decrypt the compromised data without paying the ransom. Follow the links below to check out the free decrypter tools provided by EmsiSoft and Kaspersky.
For an easier removal solution of all existing infections and future protection against the latest malware threats download a trusted anti-spyware software.
We hope that you found these instructions useful !
Contact Us: [email protected]