Security researchers were able to devise a new brute force technique which allows them to crack credit card numbers information for only a few seconds.
Credit Card Numbers Can Now Be Easily Cracked
A group of security researchers and experts have managed to create a brute force technique which allows the cracking of credit card information such as expiration dates and CVV codes by quering various eCommerce sites. The issue was described in detail in a research paper title “Does The Online Card Payment Landscape Unwittingly Facilitate Fraud?” . The research has shown that there are a number of vulnerabilities that affect Visa’s payment ecosystem.
To understand what the problems are, we need to get a brief overview of how payment cards in general are used to conduct online transactions.
- The customers visit an eCommerce site and shops for a particular item. Afterwards they have to enter their payment card information during the checkout process. This data is passed to the bank that issued the card which authorizes or rejects the payment request.
- The merchant uses several different payment gateways and services to perform the transaction. These gateways work together with payment networks and banks to perform the transaction.
- The online card payments are done through a “card-not-present” transaction mode which means that the merchant cannot physically verify that the customer actually holds the card. This is why they are required to enter the complete payment card information to verify that this is true. Some of the requested data includes the following: cardholder name, card number, card expiry date, card verification value (CVV) and cardholder address.
The attack works by exploiting two major weaknesses in some of the global payment systems.
The first one is that some of the major systems do not detect when multiple invalid requests on the same card are performed through different merchant sites. This gives attackers the possibility to perform large-scale brute force attacks without worrying that a filter may block their operation.
The second weakness involves the individual designs of the implementation of the payment process. The different merchant sites utilize different fields which makes it much more effective to target individual pieces of information to quickly perform the attacks.
The Credit Card Numbers Cracking Demonstration
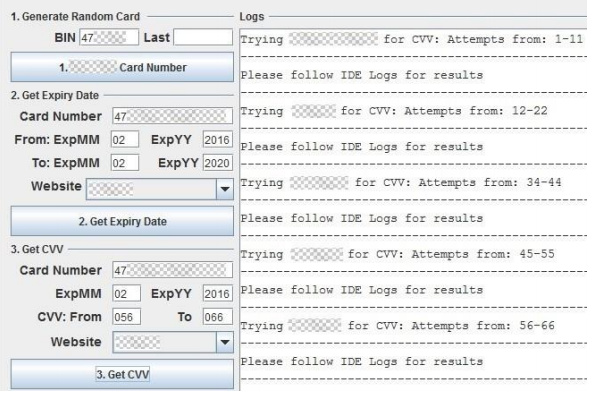
The team of researchers have demonstrated their technique by implementing a set of software tools to carry out a distributed brute force attack using the payment cads of the team members. this included a total of seven Visa cards with a spread of PAN, expiry date, and CVV2 values. Next, a selection of 400 Alexa Top rated commercial sites were added to the site list including iTunes, Google, Paypal and Amazon.
The used tools are automated scripts written in the Java Selenium browser framework. The demonstration was done using the Mozilla Firefox web browser.
The tests showcases that it is possible to run multiple bots at the same time on hundreds of payment sites without triggering any alarms in the payment systems. This allows online payment requests to get authorized within 2 seconds.
Here is an excerpt of the conclusion which sums the issue:
We showed that the attack works if the card payment network is not able to relate card activities from different websites. Fundamentally, much of the problem with card payment stems from the fact that the identity of the payer needs to be established in the ‘card-not-present’ mode. This is inherently problematic since it is at odds with the original use of cards (where the card and cardholder are present at the moment of purchase). It also implies that, for instance, Chip-and-PIN is not available to establish the identity of the payer. This is exacerbated by the fact that the Internet facilitates distribution of guesses for data fields over many merchant sites. To prevent the attack, either standardisation or centralisation can be pursued (some card payment networks already provide this). Standardisation would imply that all merchants need to offer the same payment interface, that is, the same number of fields. Then the attack does not scale anymore. Centralisation can be achieved by payment gateways or card payment networks possessing a full view over all payment attempts associated with its network. Neither standardisation nor centralisation naturally fit the flexibility and freedom of choice one associates with the Internet or successful commercial activity, but they will provide the required protection. It is up to the various stakeholders to determine the case for and timing of such solutions.



