The Stolich ransomware is a new iteration of the EDA2 open-source malware family which can be removed easily by reading our complete removal guide.
Stolich Ransomware Description
Malware researchers spotted a new virus strain that has been identified as coming from the famous EDA2 open-source malware family. The threat has undergone an initial analysis and using the available information we have constructed a thorough review and removal guide. In comparison to other similar siblings this iteration does not feature any new components.
As Stolich ransomware stems down from EDA2, it is good to know that even though the family was one of the first open-source ones (along with Hidden Tear), it continues to be one of the most popular bases to develop a ransomware threat. One of the reasons is the fact that it can be easily modified and configured to act against specific targets. The flexibility that the hackers have when creating strains from these two families are almost unmatched.
Likewise the virus engine can be customized. The EDA2 code can be used to setup the following modules:
- Encryption – The engine may use AES-256, RSA or another cipher to process the user data.
- Network Connectivity – As the Stolich ransomware like other variants of this family uses a remote C&C (command and control) server to report and download commands from, the hackers can specify a list of servers. Other available options include the possibility of encrypting the connection or forwarding it through proxies and various web services. We have already seen versions of implementation of custom protocols to evade detection using the most common filters.
- Additional Payload Delivery – The attackers may opt to install additional threats to the compromised machines.
- Botnet Recruitment – Victims of the Stolich ransomware can be recruited into a worldwide botnet. Such a large force can be used to launch spam email sites or DDOS attacks against predefined targets.
- Custom Extensions Renaming – Depending on the targets the ransomware may opt to use different file extensions when processing the target user files.
- Screenlocker – The creation of a screenlocker can prohiibt ordinary interaction with the compromised machine.
Ransomware strains such as this one have been used as both education tools and weapons used in mass attacks. In the most common case the hackers employ the ransomware in a several stage attack campaign. Most of the detected attacks happen due to automated vulnerability testing done with the help of exploit kits. They target various forms of software and operating systems vulnerabilties. Its hardly a surprising fact that the majority of desktop users lack proper security as they do not take the time to maintain their systems by updating them. This is the reason why a very large part of the predefined targets turn into victims of dangerous code.
The Stolich ransomware does not seem to use a different infection mechanism than the original EDA2 core. This means that upon infection with it the following routine is executed:
- The local engine contacts the remote server with basic extracted information about the infectd host. The original EDA2 used two variables – the computer’s name and the currently logged in user.
- The C&C server(s) generate a public/private keys pair which are used during encryption. The public key is sent to the virus engine on the local machine, while the private one is stored safely in a database operated by the hackers.
- The locally installed Stolich ransomware greates a random key based on the sent information and begins to target a predefined list of popular user file type extensions. Depending on the individual strain the list may be modified.
- When the process is complete the operation is announced to the remote C&C server.
- The ransomware note is displayed to the victims.
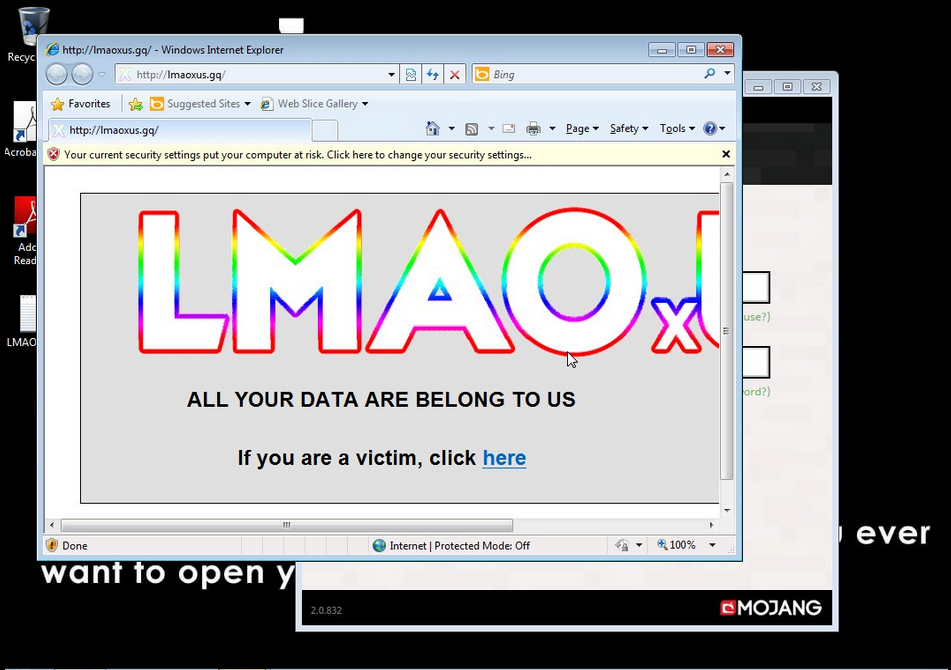
The displayed note displays an image which reads “ALL YOUR DATA ARE BELONG TO US. If you are a victim, click here”. The next screen displays the proper note on a text window overlay with a flashy background image.
LMAOxUS
You’ve been hit by LMAOxUS. But there’s still hope for you.
Send 0.1 BTC to 1Jek8L6HRjpNpcAasgoV37eoHqLUMyYjU
Use any payment processor you want, I recommend Coinbase or Blockchain.info. If BTC is too hi-tech for you, send me an email, I’m sure we can work something out.
Once done, send an email to [email protected] with the transaction details.
Listen fam, I don’t care about your data. My goal is not to cause harm or to fuck with people just for the hell of it. I’m just a broke college student in need of money. I have nothing personal against you. I promixe I’ll fix your data once I get your payment. If for whatever reason you’re even more broke than me, well shoot me an email and give me your best sob story. I do have a heart. Otherwise, you have until the date listed in your notepad until the server automatically deletes your decryption key. After that date, there’s nothing I can do. So I wouldn’t waster any more time. 🙂
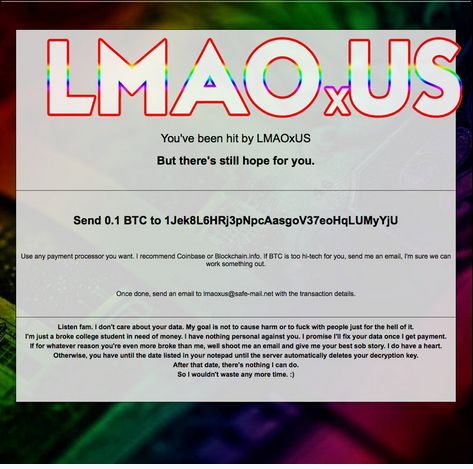
From the ransomware note we can conclude that there are several key characteristics employed by the hacker operators. The most important thing is that the criminal(s) behind the Stolich ransomware attempt to use a popular social engineering trick by posing as a poor college student. The use of empathy and informal language can convince a part of the victims to actually pay the fee.
As always the Bitcoin digital currency is used which is anonymous and cannot be traced down to a specific individual. Furthermore the use of the safe-email solution allows for additional privacy as it allows for private message sending. At the moment One Bitcoin is about 1156 US Dollars.
Unofficial information suggests that the developer behind the virus may be of Indian origin. According to the available analysis he has modified the core EDA2 code and removed the integrated backdoor function. The new strain uses a custom code obfuscator which means that the anti-virus companies need to update their definitions to reflect the change. At the moment the Stolich ransomware is categorized as being under active development. We suspect that new iterations may appear in the near future.
Stolich Ransomware Distribution
The Stolich ransomware is distributed in an ongoing large-scale global campaign. The hackers behind it use infected Minecraft installers and other related packages. The use of bundled installers is a popular tactic where the installers are distributed on various hacked or hacker-controlled sites.
Minecraft is one of the most popular games and this means that the dangerous code can also be found on various add-ons and custom packages which can also be posted on various community sites, forums and social media. This is the reason why computer users should be extra careful when installing such unofficial sources.
Other sources include email spam message campaigns (with or without the use of social engineering tricks), browser hijackers and various sorts of redirects. We presume that the criminals may also create specialist Minecraft-themed sites which can contain both ad networks and distribute the Stolich ransomware.
Summary of Stolich Ransomware
| Name | Stolich Ransomware |
| File Extensions | Depending on the strain |
| Ransom | One Bicoin |
| Easy Solution | You can skip all steps and remove Stolich Ransomware ransomware with the help of an anti-malware tool. |
| Manual Solution | Stolich Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution | Spam Email Campaigns, malicious ads & etc. |
Stolich Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Stolich Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Stolich Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Stolich Files
- 1) Use present backups
- 2) Use professional data recovery software
- – Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



