Rush ransomware encodes victims’ files with means of the AES-256 algorithm. The extension .remind or .crashed is appended to the extensions of the encrypted files. The ransom amount is 2 BTC, which equals to over $1300. It drops ransom note, displays ransom message and provides five days to accomplish the payment.
| Name | Rush Ransomware |
| File Extensions | .remind or .crashed |
| Ransom | 2 Bitcoins |
| Solution #1 | Rush ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
| Solution #2 | Rush Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution | Ransomware may use various techniques for the delivery of its malicious components to the system. |
We will look into Rush ransomware details, expose some of its delivery techniques and offer appropriate actions to remove the threat from the system.
Details in the Infection Process of Rush Ransomware
Rush ransomware is a crypto virus that aims to penetrate the system, encode victim’s files and request a ransom in exchange for the decryption key.
Once Rush ransomware is installed on the system, it creates an executable file. This file may have randomly generated name. The name may be either sequence of random symbols or identical to any legitimate Windows process. The executable file may locate in folders that store essential files for the operating system.
- %AppData%
- %LocalAppData%
- %Roaming%
- %Local%
- %Windows%
- %User’s Profile%
Rush ransomware may run with every start of the Windows. This may be caused by changes in Windows Registry Editor. The Run keys are responsible for the programs that start automatically each time the Windows OS is started. Rush ransomware could change or add some values in the Run keys.
→HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
After the execution of the malicious file, Rush ransomware searches for files with certain file extensions and starts the encryption process. Rush ransomware will detect and encode all files that have one of the following extensions:
The encryption operation ends with appending the extension .remind to the names of the original files after their initial extensions. It appears that Rush ransomware has got different variants thus the affix may also be .crashed.
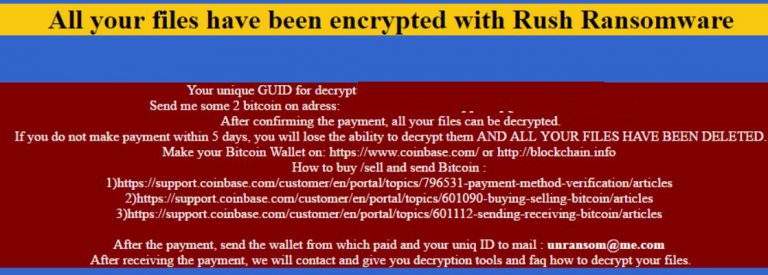
What follows is the creation of a file with the name “DECRYPT_YOUR_FILES.HTML“. It may be created in all folders that contain encrypted data and on the desktop. The content of this file is the text of the ransom note. The text states:
“All your files have been encrypted with Rush Ransomware
Your unique GUID for decrypt ***
Send me some 2 BitCoin on address: {bitcoin address}
After confirming the payment, all your files can be decrypted.
If you do not make payment within five days, you will lose the ability to decrypt them, and all your files have been deleted
Make your Bitcoin Wallet on: https://www.coinbase.com/ or http://blockchain.info
How to buy /sell and send Bitcoin:
l)https://support.combase.com/customer/en/portal/topics/796531-payment-method-verification/articles
2)https://support.coinbase.com/customer/en/portal/topics/601090-buying-selling-bitcoin/articles
3)https ://support.coinbase.com/customer/en/portal/topics/60 111 2-sending-receiving-bitcoin/articles
After the payment, send the wallet from which paid and your unique ID to mail: [email protected]
After receiving the payment, we will contact and give you decryption tools and FAQ how to decrypt your files.” Source: Infected users.”
According to the ransom message the victims should pay an amount of 2 BTC or over $1300 if they want to recover the encrypted files. We firmly advise you to avoid this action and try to deal with the problem without supporting cyber criminals’ malicious activities. At the end of the article, you could find step-by-step instructions on how to remove Rush ransomware manually.
Techniques of Rush Ransomware Delivery
Rush ransomware may use various techniques for the delivery of its malicious components to the system:
- Script with embedded malware binaries;
- Malicious attachments in emails;
- Malicious code in the text of emails;
- Vicious redirect links in legit websites;
- Compromised links in private messages on social networking sites;
- Malicious macros embedded in documents;
- File sharing websites.
Remove Rush Ransomware from the System
There is no doubt that you should instantly remove Rush ransomware from the system. The harm that it has caused to your data should be sufficient reason to eliminate any doubts of Rush ransomware removal. The system is exposed to other risks if you leave the threat on it. Some of the dropped malicious files may serve as a backdoor to cyber-criminals. We firmly recommend getting rid out of all records associated with Rush ransomware. Our removal instructions at the end of the article will help you to remove Rush ransomware manually. In case interfere with system files and registries appears a tough task you could try an automatic removal with a reliable anti-malware software. However, we are open to answering your questions just leave us a comment, and we will assist you.
In order to prevent from ransomware infection, you could use the services of VirusTotal and check the status of all files that look suspicious.
Recover .Remind/.Crashed Files
You won’t have any problem to restore encrypted files if you have a backup of your data. As times goes by malware is getting more invasive and that’s why regular backups are essential for your data security. Utilizing Shadow Explorer may be a way to recover .remind/.crashed files in case the shadow volume copies stored in Windows OS are not erased by Rush ransomware. Something else that worths trying is reliable file recovery software.
Try to Load Your PC in Safe Mode
For various Windows OS’s:
1) Hit WIN Key + R
2) A Run window will appear. In it, write “msconfig” and then press Enter.
3) A Configuration box shall appear. In it Choose the menu named “Boot”.
4) Choose the Safe Boot preference and then go to Network under it to tick it.
Eliminate the malicious processes
1) hit the following key combination: CTRL+ESC+SHIFT
2) Get over to Processes.
3) Choose the suspicious process if you have found it and then right click it after which click on “Open File Location”.
4) End the malicious process by again right-clicking and choosing “End Process”.
Delete registry objects created by malware.
For all Windows versions:
1) Again type simultaneously the Windows Button + R. key combination.
2) In the type box, write “regedit”(without the inverted comas) and hit Enter.
3) Type the CTRL+F key combination and then write the malicious name in the search type field to locate the malicious executable.
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys.
Recover files encrypted by ransomware.
If you want to try recovering files yourself, you have several options:
Option One: By using Windows’s System Restore
1) Hit the Windows Button + R. key combination.
2) After the “Run” Window pops up, write “rstrui” and hit on the Enter button.
3) Choose a restore point and continue.
IMPORTANT: If you want to be more effective, we strongly suggest booting in safe mode if you are to do this!
Option Two: By using Windows’s Shadow Volume Copies
To access shadow volume copies you may require a program, like Shadow Explorer. Install it open it and make it scan for shadow copies. If you have them enabled, this method will work, in case the crypto-virus has not deleted them.
Option Three: By using various Recovery Software
This option will not ensure maximum effectiveness and recovery rate but still, you may restore several files. Most data recovery programs are available for free online, simply Google “Data Recovery Software”.
Prevent viruses from damaging your files in the future.
To protect your important data we suggest that you store it in the cloud. Programs that makes online backup possible also enable you to schedule auto backup on different time periods and this way, even if you lose your data, you can find it uploaded in securely encrypted account, access to which only you have.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter