The Nuke ransomware is a new malware variant that has been identified by security researchers only a few days ago. Like other similar threats Nuke encrypts target user files and blackmails the user into paying a ransom fee to restore them.
| Name | Nuke Ransomware |
| File Extensions | .0x5bm |
| Ransom | Varies |
| Solution #1 | Nuke ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
| Solution #2 | Nuke Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution | The Nuke ransomware is distributed mainly by spam email campaigns. |
Nuke Ransomware Description
The Nuke ransomware is one of the newer ransomware threats that have unknown origins. It is not known which hacker or hacker group created the malware and why it is called Nuke. It has been discovered only a few days ago and security researchers have already spotted a few attacks with it.
Nuke shows typical features and it doesn’t stand out with something out of the ordinary. Upon infection it encrypts target file extensions such as Office documents, Music and video files, and encrypts them with a strong AES-256 cipher. The target data is renamed with random names and with a “.0x5bm” extension.
Ransom instructions are created on various locations and the desktop wallpaper is also changed to showcase them.
The ransomware has provided an email address to contact the hackers who operate the ransomware – [email protected] which is probably a covert inbox.
This is the contents of the ransom note:
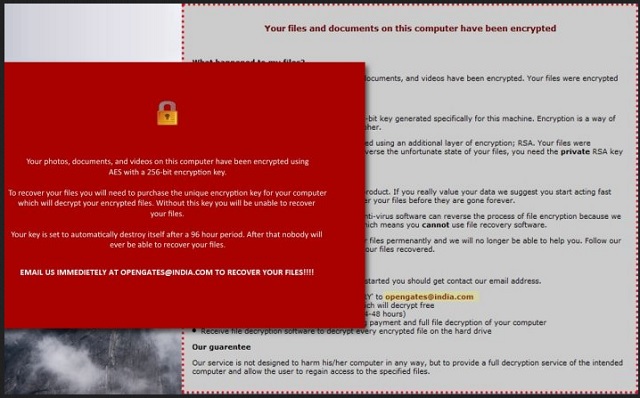
!! Your files and documents on this computer have been encrypted !!
** What has happened to my files? **
Your important files on your computer; photos, documents, and videos have been encrypted. Your files were encrypted using AES and RSA encryption.
** What does this mean? **
File encryption was produced using a unique 256-bit key generated specifically for this machine. Encryption is a way of securing data and requires a special key to decipher.
Unfortunate for you, this special key was encrypted using an additional layer of encryption; RSA. Your files were encrypted using the public RSA key. To truly reverse the unfortunate state of your files, you need the private RSA key which is only known by us.
** What should I do next? **
For your information your private key is a paid product. If you really value your data we suggest you start acting fast because you only short amount of time to recover your files before they are gone forever.
There are no solutions to this problem, and no anti-virus software can reverse the process of file encryption because we have also erased recent versions of your files which means you cannot use file recovery software.
Modifying your files in any way can damage your files permanently and we will no longer be able to help you. Follow our terms assigned to you below, and we will have your files recovered.
** Recovering your files **
– Send an email with the subject ‘FILE RECOVERY’ to [email protected]
– For a free test decrypt, send one small file which will decrypt free
– Wait for a response from us (up to 24-48 hours)
– We will send you further information regarding payment and full file decryption of your computer
– Receive file decryption software to decrypt every encrypted file on the hard drive
Nuke Ransomware Distribution
The Nuke ransomware is distributed mainly by spam email campaigns. The contents of the messages contain attachments or malicious links that lead to the dangerous binary file. Ransomware can often be found also on infected software bundles and torrents.
Nuke Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete Nuke completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Nuke Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
2) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
- 1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



