The Bing.VC hijacker modifies the behavior of the user’s internet browser. It is being distributed by Lavians Inc. Security researchers have spotted that the new variant replaces the homepage and the default search engine. In addition, it actively steals cookies and in some cases installs keyloggers that steal sensitive user information. It infects the most popular browsers that are used today – Internet Explorer, Mozilla Firefox, and Google Chrome. You can remove the hijacker using information from this article.
| Name | |
| Main Domain Address | Bing.VC |
| Solution #1 | The easiest way to remove and other browser hijackers from your computer is with the help of an anti-malware tool. This software will also protect your computer from severe cyber threats like ransomware |
| Solution #2 | You can remove the browser hijacker by hand by carefully following all the guidelines of our step-by-step guide below. |
| Distribution | PUPs, malicious ads, bundle packs. |
Bing.VC Browser Hijacker – Distribution
The Bing.VC infection can be installed by the user as part of a bundle with other software. Some vendors and software distributions can include it as part of their application. This is most often found when installing freeware or shareware software from the Internet. During the installation process Bing.VC may be included in the software by default. Users can prevent installation by unticking the check box or clicking “Disagree” in a dialog box depending on the scenario. In most cases, these options and buttons are available on the Terms of Use page.
In some cases, counterfeit installation packages can also be a source of infection.
Users may find download links embedded in emails and/or various websites. The hijacker can also spread through various pop-ups, banners, and redirects.
Security researchers have observed that the main sources of infection are installation packages for popular applications and drivers. Examples of such files are:
- HP DESKJET F4580 Driver Utility Setup
- DELL Inspiron 5100 Drivers Utility Setup
- Acer Aspire ONE ZG5 Drivers Utility Setup
Users are advised to download such utilities from official sources only.
Bing.VC Browser Hijacker – More Details
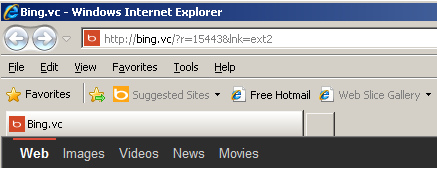
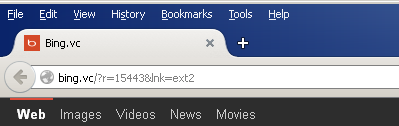
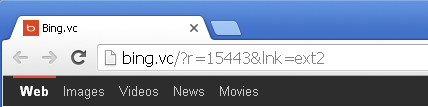
Experts have analyzed the behavior of the hijacker and noted that it installs silently without informing the user. Upon successful installation, it changes the browser homepages of Internet Explorer, Google Chrome, and Mozilla Firefox to “hxxp://bing(.)vc/?r=15443&lnk=sct2”. The default search engine is also changed to Bing.VC. This is a spoof of Microsoft’s search engine Bing and it has nothing to do with it.
The browser hijacker installs various binary and utility files in the system drive using the following scheme:
C:\Documents and Settings\Administrator\Local Settings\Application Data\IconOverlayEx.dll
C:\Program Files\DELL Latitude D810 Drivers Utility\DPInst.exe
C:\Program Files\DELL Latitude D810 Drivers Utility\DriverBackUp.exe
C:\Program Files\DELL Latitude D810 Drivers Utility\driverlib.dll
C:\Program Files\DELL Latitude D810 Drivers Utility\DriverUpdateUtility.exe
C:\Program Files\DELL Latitude D810 Drivers Utility\unins000.dat
C:\Program Files\DELL Latitude D810 Drivers Utility\unins000.exe
C:\Program Files\DELL Latitude D810 Drivers Utility\update.dll
C:\Documents and Settings\All Users\Desktop\DELL Latitude D810 Drivers Utility.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\DELL Latitude D810 Drivers Utility\DELL Latitude D810 Drivers Utility.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\DELL Latitude D810 Drivers Utility\Uninstall DELL Latitude D810 Drivers Utility.lnk
Note: In this example, the “Dell Latitude D810 Drivers Utility” name is used by the hijackers.
When the user uninstalls the software package this file still stays in place. In addition two registry entries are added to the system:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellIconOverlayIdentifiers\ IconOverlayEx\: “{E1773C0E-364D-4210-B831-72F5A359E88F}”
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved\{E1773C0E-364D-4210-B831-72F5A359E88F}: “Icon Overlay Shell Extension”
This is a shell extension handler, a known trick that hijackers often use. It requires no administrator rights for execution.
After uninstallation and a machine restart, the home page is changed without the user’s knowledge and/or authorization. The Bing.VC changes it after the uninstallation of the software package.
Examples of hijacked browser windows are shown below:
Internet Explorer
Mozilla Firefox
Google Chrome
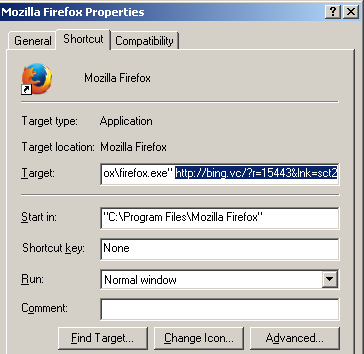
The shortcut targets are modified by the hijacker in order to introduce the changed home page.
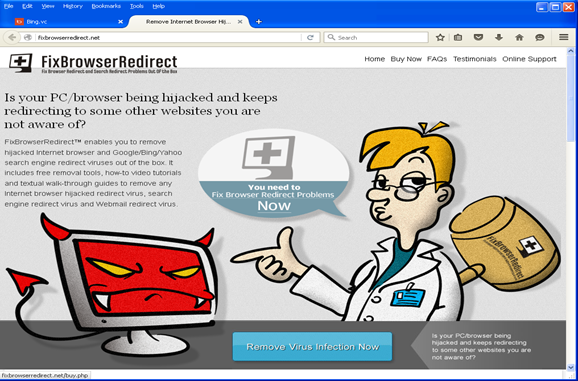
The counterfeit homepage shows a redirect to a rogue security site (fixbrowserredirect.net) that offers the users to buy software in order to fix the redirection.
How to remove Bing.VC from your Browser
You must first uninstall the registry entries that have been installed by the hijacker:
1. Using the Windows (Start) Menu go to “Run” (or use the shortcut CTRL + R) and type “regedit”. Press the “Allow” button in order to access the Microsoft Windows Registry Editor.
2. Navigate to the two registry entries and delete them:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellIconOverlayIdentifiers\ IconOverlayEx\: “{E1773C0E-364D-4210-B831-72F5A359E88F}”
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved\{E1773C0E-364D-4210-B831-72F5A359E88F}: “Icon Overlay Shell Extension”
You also need to remove the IconOverlayEx.dll from your system. It is located at:
C:\Documents and Settings\Administrator\Local Settings\Application Data\IconOverlayEx.dll
The last step is to clean up the shortcut targets from your desktop and/or start menu. Right click on the shortcut to the browsers that you use (i.e. Internet Explorer, Google Chrome, Mozilla Firefox) and remove the string that is attached next to the shortcut. You need to have only the path to the .exe file and nothing else.