
The RozaLocker ransomware targets mainly Russian-speaking users and requests a ransom payment of 10000 Roubles, read our complete removal guide to learn more about it.
RozaLocker Ransomware Description
The RozaLocker Ransomware is a new virus which has just been reported by malware researchers. At this moment the initial analysis does not show any connection between this iteration and the famous families of viruses. We do not have information about the developer or hacker collective behind it. The only name that is mentioned is the alias (aoneder).
Upon infection it follows the same basic behaviour like all similar threats. It encrypts target user files, displays a ransomware note and then extorts the victims for a payment. Right now we do not have access to the complete list of affected file type extensions, however we assume that it targets the most popular ones – documents, photos, videos, backup images, configuration files, databases and etc.
As the virus is distributed as a executable file upon interaction with it the victim is presented with a UAC prompt. It requests elevated privileges in order to start the encryption engine. If this is not done, an application window is loaded which has the title “Игровая программа от Саши Рендера” (which translates as “Game program from Sashi Rendera”). It features a single line “ПОИСК …” (“Search”).
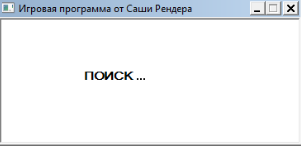
If the user grants the necessary privileges to the application then the predefined file type extensions are affected.
Once this is complete the virus displays a ransomware no in Russian. A machine-translated version of it reads the following:
YOUR FILES are encrypted (EVEN NOT LOOKING THAT THEY ARE PARTIALLY OPEN). WE HAVE YOUR LOGIN AND PASSWORD FROM THE ENTERTAINMENT, ONE-CLASSICS, ONLINE BANKS AND OTHERS.
YOU HAVE 6 HOURS TO PAY FOR A PURCHASE FOR THEM, OTHERWISE WE SHOULD PUT INTO OPEN ACCESS!
INSTRUCTION:
1) Find 10 000 (10 thousand) rubles, not less. Suitable for the following –
(Qiwi, Sberbank, Yandex.Money, Tinkoff Bank, VTB, but better Qiwi (faster)
2) In the browser, open the site https://x-pay.cc/ – through this site you will transfer money
3) In the column I DELETE where you will translate (according to item 1) and above enter the amount – 10,000 rubles.
4) In the RIGHT I select Bitcoin and on top the amount should automatically be transferred to btc
5) In the column DATA ENTRY, fill in your requisites from where you will pay and where to transfer (Bitcoin wallet)
ATTENTION-ATTENTION, CORRECTly copy this number to a purse (yes, it’s so strange)
3FjtFZWjyj46UcfDY4AiUrEv7wLtyzZv5o
After inserting, carefully, again check whether it is copied correctly.
6) Click on GO TO PAY and follow the instructions on the site.
In a couple of hours we’ll write you on the desktop and return everything to you.
If there are difficulties, then write on the mailbox – [email protected]
The virus has been found to initiate the following actions:
- Unusual Drive Letter Access – The virus tries to access unusual drive letters on the local computer. In most cases they apply to mapped network shares.
- Registry Monitoring – The virus engine monitors specific registry values for changes.
- File Deletion Capabilities – The virus can delete itself if specific criteria are met. In most cases this is part of the stealth protection module which stops the ransomware from running if an anti-spyware ot anti-virus solution is detected.
- Language Options Extraction – The built-in engine is able to extract the information about the currently selected language.
RozaLocker Ransomware Distribution
The first malware samples were detected in the beginning of March 2017. The virus is primarily distributed as binary executable files:
- Counterfeit Installers – One of the most popular infection strategies is the insertion of the virus code in software installers. The first malware samples were found in numerous Setup.exe packages available on untrusted download sites and portals, as well as P2P networks like BitTorrent.
- Spam Messages – Hackers can opt to use bulk email messages which distribute the virus files as directly attached, linked or downloaded to the host computer via a dangerous script.
- Dangerous Scripts – Malicious scripts such as hacker-controlled ad networks and browser hijackers can also lead to a RozaLocker Ransomware infection. The ad networks not only generate a revenue for the operators, but can also redirect to dangerous dowload sites. Browser hijackers modify the settings of the installed web browsers (Mozilla Firefox, Google Chrome and Internet Explorer) to redirect to a hacker-controlled site. This includes the home page, default search engine and new tabs page.
- Exploit Kits – Hackers can use automated attacks against predefined targets by using exploit kits. They attempt to infltrate the computers by targeting outdaded software and service installations.
The virus has also been identifies as masking as a trainer (trainer.exe), which is a type of cheating tool that is popular with PC gamers.
Summary of the RozaLocker Ransomware
| Name | RozaLocker Ransomware |
| File Extensions | .enc |
| Ransom | 10000 Roubles (Around 170 US Dollars) in Bitcoins |
| Easy Solution | You can skip all steps and remove RozaLocker Ransomware ransomware with the help of an anti-malware tool. |
| Manual Solution | RozaLocker Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution | Spam Email Campaigns, malicious ads & etc. |
RozaLocker Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely RozaLocker Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore RozaLocker Files
- 1) Use present backups
- 2) Use professional data recovery software
- – Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



