Most malicious content on the web relies on tricking the users into clicking something they shouldn’t be clicking on. That’s why most ransomware viruses get distributed through emails masked to look like genuine messages from a company. While this is a fairly dastardly thing to do, it pales in comparison to the new no-click method of distributing malicious content. Users can get infected with a banking Trojan by malvertisers.
Specifics of the No-Click Method
This new way of infection is reported by Kaspersky Labs. The researchers claim that the ads, that use this trick go through the Google AdSense advertising network. The agency is quite big, and lots of sites display ads from them. While users are simply browsing the Internet, they can download the last-browser-update.apk without any interference on their part. The .apk is part of the Svpeng Trojan family.
If the unwitting user decides to check the .apk, it can be installed, and the phone will be infected. The baking trojan is made to steal bank account information, intercept SMS That scheme can cost the victim quite a bit of money. The Trojan isn’t the only malicious thing on the APK, which is also loaded with powerful spyware as well. Svpeng collects a massive amount of data, including; The device’s ID, call information, call history, multimedia messages (photos, videos, gifs, text), browser data, bookmarks and phone contacts.
Here’s picture from the Meduza site, showing the download of the trojan, provided by Kaspersky Labs:
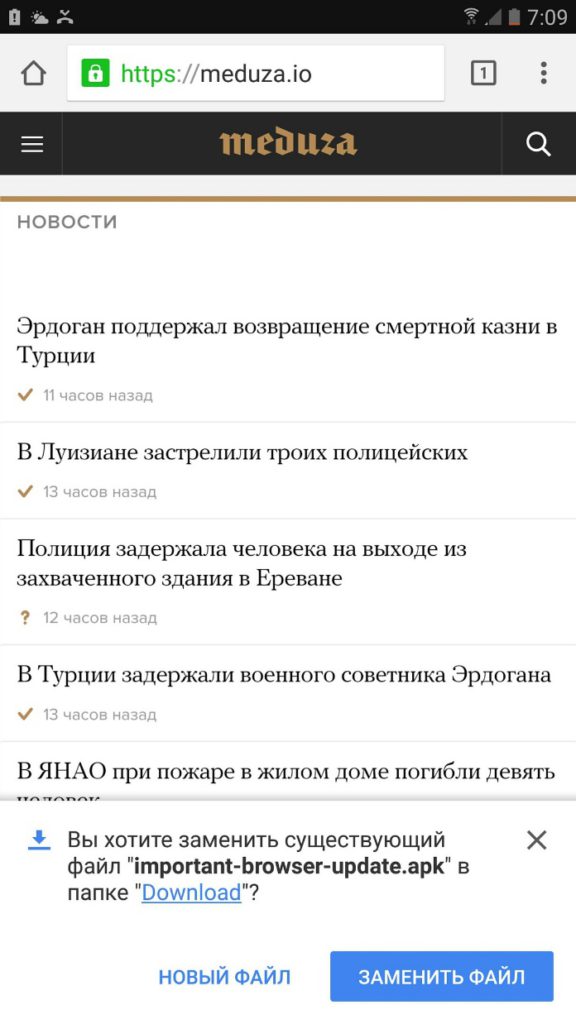
More Information About the Infection
Once installed, the .apk disappears from the application list. It’s pretty hard for users to locate and delete it.
The virus is distributed with malicious ads, but this time, they’re not limited to shady websites. The researchers at Kaspersky stated that the adware is found on two big Russian news agencies – Russia Today and Meduza. The latter reported that their site is now free of the infection. The virus is designed to penetrate most Android defensive programs that are popular in Russia.
A lot of legitimate sites use the Google AdSense network, so the .apk can pop-up anywhere. Be careful with your Android browsing. The good news is that the .apk won’t install without the user’s involvement. If you get any .apk’s that you don’t remember downloading, then it’s best to avoid opening them. Most of the time, a message will pop-up informing the user that he/she has downloaded “last-browser-update.apk.” If you see that message on your Android screen, don’t open it.
Protection from Android Viruses
The non-click method demonstrates that malware developers are trying more sophisticated methods of infection. While this is troubling, it also shows that more users have learned how to counter-act the usual old tricks. Our team has always advocated the notion that good cyber-security etiquette is half the battle against malware. The other half is a good security program, an anti-virus or anti-malware tool. Encryption and good passwording can also prove crucial for cyber-security. You can check out our guide to Android security for more information on the subject. Remember – always be vigilant, even on legitimate looking sites. The advertising game is so big at the moment, and there’s always crooks that will try to take advantage of it through malicious means, like the pay-per-install adware that we reported earlier this month.



