The Gruxer ransomware virus is a new threat based on the Hidden Tear family of malware that encrypts user data and can cause other damage to the infected systems. Victims can follow our in-depth removal guide to delete active infections and prevent future intrusion attempts. There are two methods of removal and recovery:
DOWNLOAD GRUXER RANSOMWARE VIRUS REMOVAL TOOL.
Gruxer Ransomware Virus Description
The Gruxer ransomware virus is a new malware threat which follows the usual behavior patterns associated with its parent – the Hidden Tear family. During the initial security analysis it has been found that the Gruxer ransomware virus is a descendant of the famous family.
When the infection is triggered the built-in engine automatically starts to encrypt a predefined list of target file type extensions. According to the configuration of the virus it may target a wide range of files: music, photos, videos, backups, archives, databases and etc.
The Gruxer ransomware virus is made up of three modules:
- Encryption Engine – The Gruxer ransomware virus features a main module that processes user and system data.
- JPG Worm – A distinctive feature of the Gruxer ransomware virus is that it includes an image worm. It processes all found JPG image files that are then rewritten in the PNG format.
- Lockscreen Blocker – This part starts after the encrypted engine has completed its work. It effectively blocks any ordinary interaction with the computer until the virus is removed. By using this module the Gruxer ransomware virus prevents the users from using manual methods of removal. It displays the ransomware note and can only be removed effectively via a quality anti-spyware tool.
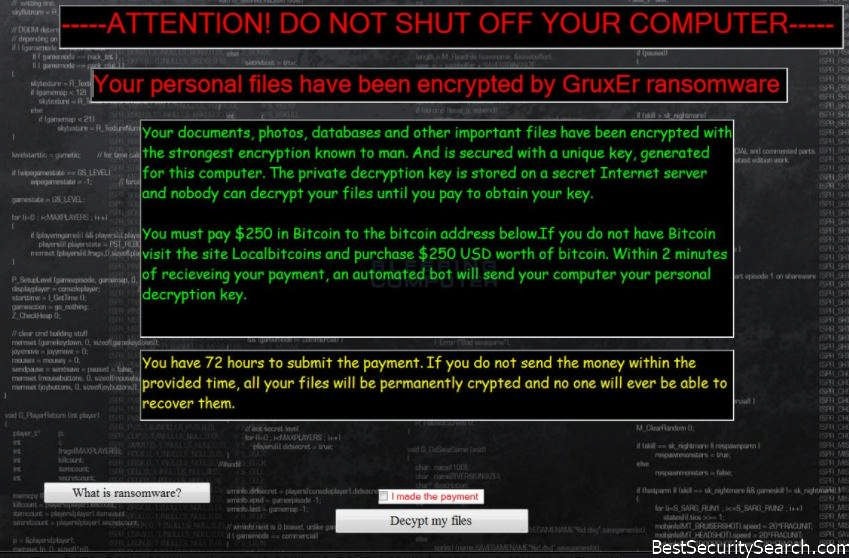
The Gruxer ransomware virus note is displayed in an application frame that reads the following message:
—– ATTENTION! DO NOT SHUT OFF YOUR COMPUTER —–
Your personal files have been encrypted by GruxEr ransomware
Your documents, photos, databases and other important files have been encrypted with the strongest encryption known to man. And is secured with a unique key, generated for this computer. The private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay to obtain your key.
You must pay $250 in Bitcoin to the bitcoin address below. If you do not have Bitcoin visit the site Localbitcoins and purchase $250 USD worth of bitcoin. Within 2 minutes of recieveing your payment, an automated bot will send your computer your personal decryption key.
You have 72 hours to submit the payment. If you do not send the money within the provided time, all your files will be permanently crypted and no one will ever be able to recover them.
[What is ransomware?] □ I made the payment
[Decypt my files]

The hackers demand a fixed ransomware fee of 250 US Dollars in the Bitcoin digital currency. The criminals behind the virus however have not specified an address where the money needs to be sent or a designed payment gateway.
The Gruxer ransomware virus is similar to the Karmen ransomware which also stems from the Hidden Tear family.
Gruxer Ransomware Virus Distribution
The Gruxer ransomware virus is a distributed as a single binary file that may have a random name. The detected samples that are associated with it include the following: GRUXER.EXE, TEARS.EXE and WORM.EXE. According to the available data it is distributed worldwide. The low number of detected Gruxer ransomware virus samples shows that the hackers may use different strategies:
- Direct Hacker Attacks – Computer criminals can launch automated attacks against whole computer networks. They use automated frameworks that find out weaknesses (vulnerabilities) in outdated software.
- Email Spam Messages – Hackers can use email campaigns that attach the Gruxer ransomware virus directly to the messages or link them in the body content.
- Infected Documents – Office documents that have been modified by the hackers can carry the Gruxer ransomware virus. In most cases they pose as being sent by a legitimate user, company or government institution. The built-in macros (scripts) trgger the infection after they are activated by the users.
- Bundle Installers – Malicious software bundles can be used to instal the Gruxer ransomware virus. The hackers modify legitimate app installers and bundle the dangerous code.
- Malicious Download Sites and P2P Networks – Hacker-controlled download sites that may pose as legitimate sources of famous software are used to spread all types of malware, including the Gruxer ransomware virus. P2P networks like BitTorrent where pirate content is usually found also constitute a major infection method.
- Browser Hijackers – Malicious browser extensions, also known as hijackers, can lead to a gruxer ransomware virus infection. They are usually made for the most popular browsers including: Mozilla Firefox, Google Chrome, Internet Explorer, Microsoft Edge and Safari. As well as infecting the victims with the malware they are also used to steal valuable information such as any stored cookies, bookmarks, history, form data, account credentials and etc.
Summary of the Gruxer Ransomware Virus
| Name | Gruxer |
| File Extensions | Varies |
| Ransom | 250 US Dollars in Bitcoins |
| Easy Solution | You can skip all steps and remove Gruxer ransomware with the help of an anti-malware tool. |
| Manual Solution | Gruxer ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution | Spam Email Campaigns, malicious ads & etc. |
Gruxer Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Gruxer Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover encryted Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
- – Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



