Our removal guide shows how the newly discovered AvastVirusinfo Ransomware which is based on Xorist, continue reading to learn how to remove existing infections.
AvastVirusinfo Ransomware Description
The AvastVirusinfo ransomware has been discovered by malware experts, this is a new iteration of computer threats that is based on the Xorist Builder code. This is a well-known family which bases its encryption engine on a project called Encoder Builder. It allows computer criminals to create customized virus threats by tweaking various parameters such as:
- Target File Types List Modification.
- Ransomware Extension.
- Encryption Cipher (XOR or TEA).
- Master Decryption Key.
- Ransomware Note Customization.
- System Modification Changes: institution of screenlockers, persistence and etc.
The ransomware builder is one of the key aspects which has driven the infection rate of Xorist viruses. They come in a lot of forms and cannot be easily distinguished at first, as they can be heavily customized. Only after a thorough security analysis can the malware researchers spot the family’s characteristics.
The AvastVirusinfo ransomware like other similar threats follows the same behaviour pattern as other viruses of this type. Upon infection it scans for specific file types and encrypts them with a powerful cipher. Bsed on the cusomizations it may vary and the resulting data is renamed with a randomly-named extension.
When the virus is engaged it copies itself to the %AppData%/Local% folders under several names, one of which is randomly-generated.
The following file types are affected by the current iteration of the ransomware:
.000, .002, .003, .004, .005, .006, .007, .008, .009, .010, .1cd, .1st, .264, .2bp, .3d, .3D,
.3d4, .3df8, .3dm, .3dr, .3ds, .3fr, .3g2, .3ga, .3gp, .3gp2, .3mm, .3pr, .4db, .4dl, .4mp, .73i,
.7z, .7z001, .7z002, .7zip, .8xi, .9png, .a00, .a01, .a02, .a03, .a04, .a05, .a3d, .aa, .aac,
.ab4, .abk, .abm, .abr, .abs, .abw, .ac3, .accdb, .accdc, .accde, .accdr, .accdt, .accdw,
.accft, .ace, .ach, .acr, .act, .adadownload, .adb, .ade, .adi, .adn, .adp, .adpb,
.adr, .ads, .adt, .af2, .af3, .aft, .afx, .agdl, .agg, .agif, .agp, .ahd, .ai,
.aic, .aiff, .aim, .ain, .aip, .air, .ais, .ait, .al, .albm, .alf, .als, .alx, .alz,
.amf, .amr, .amu, .amx, .amxx, .ani, .ans, .aoi, .ap, .apd, .ape, .api, .apj, .apk,
.apm, .apng, .app, .application, .appx, .appxbundle, .aps, .apt, .apx, .apz, .ar,
.arc, .arh, .ari, .arj, .ark, .aro, .arr, .art, .artwork, .arw, .asa, .asc, .ascii,
.ascx, .ase, .asec, .asf, .ashx, .ask, .asm, .asmx, .asp, .aspx, .asr, .asw, .asx,
.asy, .atom, .aty, .aup, .avatar, .avi, .avs, .awdb, .awg, .awp, .aws, .awt, .aww,
.axx, .azw, .azw3, .azz, .b1, .b64, .ba .back, .backup, .backupdb, .bad, .bak, .bank,
.bar, .bas, .bat, .bay, .bbb, .bbc, .bbs, .bc, .bck, .bdb, .bdp, .bdr, .bean, .bgt, .bh,
.bhx, .bib, .bic, .big, .bik, .bin, .bkf, .bkp, .blend, .blf, .blkrt, .blp, .bm2, .bmc,
.bmf, .bml, .bmp, .bmx, .bmz, .bna, .bnd, .bndl, .boc, .bok, .boo, .bp2, .bp3, .bpl,
.bpw, .brk, .brn, .brt, .bsp, .bss, .btd, .bti, .btm, .btr, .bz, .bz2, .bza, .bzabw,
.bzip, .bzip2, .c, .c00, .c01, .c02, .c03, .c10, .c4, .c4d, .cab, .cache, .cad, .cag,
.cal, .cals, .cam, .can, .cap, .car, .cb7, .cba, .cbr, .cbz, .cc, .ccd, .cch, .cd,
.cd5, .cda, .cdb, .cdc, .cdf, .cdg, .cdmm, .cdmt, .cdmtz, .cdmz, .cdr, .cdr3, .cdr4,
.cdr5, .cdr6, .cdrw, .cdt, .cdx, .cdz, .ce1, .ce2, .cer, .cf, .cfg, .cfm, .cfp,
.cfu, .cgf, .cgi, .cgm, .chart, .chk, .chm, .chord, .cib, .cimg, .cin, .cit, .ckp,
.class, .clear, .clf, .clkw, .clr, .cls, .cma, .cmd, .cms, .cmt, .cmx, .cnf,
.cnm, .cnt, .cnv, .cod, .coff, .col, .colz, .com, .config, .contact, .cp, .cp9,
.cpc, .cpd, .cpg, .cpi, .cpio, .cpl, .cpp, .cpr, .cps, .cpt, .cpx, .cr2, .craw,
.crd, .crdownload, .crt, .crw, .crwl, .crypt, .cs, .csh, .csi, .csl, .cso, .css,
.csv, .csy, .ct, .ctt, .cty, .cue, .cv5, .cvg, .cvi, .cvs, .cvx, .cwf, .cwt,
.cxf, .cyi, .czip, .daa, .dac, .daconnections,.dacpac, .dad, .dadiagrams, .daf,
.dal, .dao, .dap, .daschema, .dash, .dat, .db, .db_journal, .db2, .db3, .dbb, .dbc, .dbf,
.dbk, .dbr, .dbs, .dbt, .dbv, .dbx, .dc2, .dca, .dcb, .dcp, .dcr, .dcs, .dct, .dcu, .dcx, .dd,
.ddc, .ddcx, .ddd, .ddl, .ddoc, .ddrw, .dds, .deb, .ded, .dem, .der, .des, .design, .deskthemepack,
.dev, .dex, .df1, .dgc, .dgn, .dgs, .dgt, .dhs, .dib, .dic, .dicom, .dif, .dii, .dir, .disk, .dist,
.dit, .divx, .diz, .djv, .djvu, .dlc, .dll, .dm3, .dmg, .dmi, .dmo, .dmp, .dnc, .dne, .dng, .dob, .doc,
.docm, .docx, .docxml, .docz, .dot, .dotm, .dotx, .download, .dox, .dp1, .dpk, .dpl, .dpp, .dpr, .dpx,
.dqy, .drf, .drv, .drw, .drz, .dsk, .dsn, .dsp, .dsv, .dt, .dt2, .dta, .dtd, .dtsx, .dtw, .dump, .dvd,
.dvf, .dvi, .dvl, .dvr, .dvx, .dwfx, .dwg, .dx, .dxb, .dxe, .dxf, .dxg, .dxl, .dz, .ebd, .eco, .ecs,
.ecw, .ecx, .edb, .edi, .efd, .efw, .egc, .eio, .eip, .eit, .elf, .email, .emd, .emf, .eml, .emlx,
.emz, .eng, .eot, .ep, .epf, .epi, .epp, .eps, .epsf, .epub, .eql, .erbsql, .erf, .err, .etf,
.etx, .euc, .evo, .evtx, .ex, .exe, .exf, .exif, .exr, .f, .f90, .fadein, .fal, .faq, .fax,
.fb2, .fb3, .fbl, .fbx, .fcd, .fcf, .fdb, .fdf, .fdp, .fdr, .fds, .fdt, .fdx, .fdxt, .fes,
.ff, .ffd, .fff, .fft, .fh, .fh10, .fh11, .fh3, .fh4, .fh5, .fh6, .fh7, .fh8, .fhd, .fic, .fid, .fif,
.fig, .fil, .fla, .flac, .flc, .flf, .fli, .flp, .flr, .flv, .flvv, .fm, .fm5, .fmp, .fmp12, .fmpsl,
.fmv, .fodt, .fol, .for, .fountain, .fp3, .fp4, .fp5, .fp7, .fp8, .fpos, .fpp, .fpt, .fpx, .frt, .ft10,
.ft11, .ft7, .ft8, .ft9, .ftn, .fwdn, .fxc, .fxg, .fzb, .fzv, .g3, .g64, .gadget, .gam, .gb, .gba, .gbk,
.gca, .gcdp, .gdb, .gdoc, .gdraw, .gem, .geo, .gfb, .gfie, .ggr, .gho, .gif, .gih, .gim, .gio, .glox,
.gmbck, .gmspr, .gmz, .gp4, .gp5, .gpd, .gpg, .gpn, .gpx, .gray, .grey, .grf, .gro, .grob, .groups, .grs,
.grw, .gry, .gsd, .gsheet, .gslides, .gthr, .gtp, .gv, .gwi, .gz, .gz2, .gza, .gzi, .gzig, .gzip, .h, .h264,
.h3m, .h4r, .ha, .hbc, .hbc2, .hbe, .hbk, .hdb, .hdd, .hdp, .hdr, .hht, .hi, .his, .hki, .hki1, .hki2, .hpg,
.hpgl, .hpi, .hpl, .hpp, .hqx, .hs, .htc, .htm, .html, .hwp, .hz, .i3d, .ib, .iba, .ibank, .ibd, .ibooks, .ibz,
.icn, .icns, .ico, .icon, .icpr, .ics, .idc, .idea, .idx, .iff, .ifo, .igt, .igx, .ihtml, .ihx, .iif, .iil,
.iiq, .imd, .img, .inc, .incpas, .ind, .indd, .inf, .info, .ini, .ink, .int, .inv, .ipa, .ipd, .ipf, .ipsw,
.ipx, .iso, .isu, .isz, .itc2, .itdb, .itl, .itw, .iwd, .iwi, .j, .j2c, .j2k, .jad, .jar, .jarvis, .jas,
.jav, .java, .jb2, .jbig, .jbig2, .jbmp, .jbr, .jc, .jfif, .jgz, .jia, .jif, .jiff, .jis, .jng, .jnt, .joe,
.jp1, .jp2, .jpc, .jpe, .jpeg, .jpf, .jpg, .jpg2, .jps, .jpw, .jpx, .jrtf, .js, .json, .jsp, .jtf, .jtx,
.jwl, .jxr, .kc2, .kdb, .kdbx, .kdc, .kdi, .kdk, .kes, .kext, .key, .keynote, .kic, .klg, .kml, .kmz,
.knt, .kon, .kpdx, .kpg, .ksd, .kwd, .kwm, .laccdb, .latex, .lav, .lbi, .lbm, .lbt, .lcd, .lcf, .ldb, .ldf,
.ldif, .lgc, .lgp, .lha, .lib, .lis, .lit, .ljp, .lmk, .lng, .lnk, .lnt, .log, .logic, .lp2, .lrc, .lrtemplate,
.lst, .ltm, .ltr, .ltx, .lua, .lue, .luf, .lvl, .lwo, .lwp, .lws, .lxfml, .lyt, .lyx, .lzo, .lzx, .m, .m2t, .m2ts,
.m2v, .m3d, .m3u, .m3u8, .m4a, .m4b, .m4p .m4v, .ma, .mac, .maf, .mag, .mam, .man, .map, .mapimail, .maq, .mar, .mat,
.maw, .max, .mb, .mbm, .mbox, .mbx, .mbz, .mcd, .md, .md3, .md5, .md5txt, .mdb, .mdbackup, .mdbhtml, .mdc, .mde,
.mdf, .mdi, .mdl, .mdn, .mds, .mdt, .mdx, .me, .mef, .mell, .mft, .mfw, .mgcb, .mgmf, .mgmt, .mgmx, .mgtx, .mht,
.mhtml, .mic, .mid, .midi, .min, .mip, .mkv, .ml, .mlb, .mlx, .mmat, .mmf, .mmw, .mng, .mnr, .mnt, .mny, .mobi,
.mod, .moneywell, .mos, .mov, .moz, .mp3, .mp4, .mpd, .mpe, .mpeg, .mpf, .mpg, .mpo, .mpp, .mpt, .mrg, .mrw, .mrxs,
.msg, .msi, .msmessagestore, .mso, .msp, .msu, .mswmm, .mt9, .mts, .mud, .mui, .mwb, .mwp, .mxf, .mxl, .mxp, .myd,
.myl, .n64, .nav, .nba, .nbf, .nbh, .nbu, .ncd, .nco, .ncr, .nct, .nd, .ndd, .ndf, .nds, .nef, .nes, .nfo, .njx,
.nk2, .nlm, .nop, .notes, .now, .npf, .npr, .nrg, .nri, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nv2,
.nvram, .nwb, .nwctxt, .nx1, .nx2, .nxl, .nyf, .nzb, .o, .oab, .obj, .oc3, .oc4, .oc5, .oce, .oci, .ocr, .ocx,
.odb, .odc, .odf, .odg, .odi, .odm, .odo, .odp, .ods, .odt, .ofl, .oft, .ofx, .oga, .ogg, .ogv, .oil, .old,
.omf, .one, .onepkg, .openbsd, .opf, .oplc, .opml, .oqy, .ora, .orf, .ort, .orx, .ost, .ota, .otf, .otg,
.oth, .oti, .otp, .ots, .ott, .out, .ova, .ovf, .ovp, .ovr, .owc, .owg, .owl, .oxps, .oxt, .oyx, .ozb, .ozj,
.ozt, .p12, .p7b, .p7c, .p7s, .p96, .p97, .pab, .pages, .pak, .pal, .pan, .pano, .pap, .part, .partial, .pas,
.pat, .pbf, .pbm, .pbo, .pbp, .pbs, .pc1, .pc2, .pc3, .pcd, .pcl, .pcm, .pcs, .pct, .pcv, .pcx, .pdb, .pdd,
.pdf, .pdm, .pdn, .pe4, .pef, .pem, .pfd, .pff, .pfi, .pfs, .pfv, .pfx, .pgf, .pgm, .pgp, .phm, .php, .phtml,
.pi1, .pi2, .pi3, .pic, .pict, .pif, .pip, .pix, .pjpeg, .pjpg, .pjt, .pkb, .pkg, .pkh, .pkpass, .pl, .plantuml,
.plc, .pli, .plist, .pls, .plt, .plugin, .plus_muhd, .pm, .pmd, .pmg, .png, .pni, .pnm, .pntg, .pnz, .pobj,
.pop, .pos, .pot, .potm, .potx, .pp4, .pp5, .ppam, .ppd, .ppf, .ppm, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx,
.prc, .prf, .prg, .prj, .prn, .pro, .prproj, .prt, .prw, .ps, .psa, .psafe3, .psb, .psd, .psdx, .pse, .psid,
.psp, .pspbrush, .pspimage, .pst, .psw, .ptg, .pth, .pts, .ptx, .pu, .pub, .puz, .pvj, .pvm, .pvr, .pwa, .pwf,
.pwi, .pwm, .pwr, .px, .pxp, .pxr, .py, .pz3, .pza, .pzl, .pzp, .pzs, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby,
.qcow, .qcow2, .qdf, .qdl, .qed, .qel, .qif, .qmg, .qpx, .qry, .qtq, .qtr, .qvd, .r00, .r01, .r02, .r03, .r04,
.r05, .r06, .r07, .r08, .r09, .r10, .r3d, .ra, .raf, .rar, .ras, .rat, .raw, .rb, .rc, .rctd, .rcu, .rdb, .rdl,
.readme, .rec, .ref, .reg, .rem, .rep, .res, .rev, .rft, .rgb, .rgf, .rgn, .rib, .ric, .riff, .ris, .rix,
.rle, .rli, .rm, .rmvb, .rng, .rom, .rpd, .rpf, .rpm, .rpt, .rri, .rrt, .rs, .rsb, .rsc, .rsd, .rsr, .rsrc,
.rss, .rst, .rsw, .rt, .rtd, .rte, .rtf, .rts, .rtx, .rum, .run, .rv, .rvt, .rw2, .rwl, .rwz, .rzk, .rzn,
.s2mv, .s3db, .s3m, .sad, .saf, .safariextz, .safe, .safetext, .sai, .sam, .sas7bdat, .sav, .save, .say,
.sbf, .sbu, .scad, .scc, .sci, .scm, .scn, .scpt, .scr, .scriv, .scrivx, .sct, .scv, .scw, .scx, .sd0,
.sd7, .sda, .sdb, .sdc, .sdd, .sdf, .sdm, .sdn, .sdoc, .sds, .sdt, .sdw, .sdxf, .sen, .sep, .sfc,
.sfcache, .sfera, .sfs, .sfw, .sfx, .sgm, .sgml, .sh, .sha, .shar, .shr, .shs, .shtml, .shw, .sig,
.sis, .sisx, .sit, .sitd, .sitx, .sk1, .sk2, .skcard, .skm, .skn, .skp, .sla, .slagz, .sld, .sldasm,
.slddrt, .slddrw, .sldm, .sldprt, .sldx, .sls, .slt, .smc, .smd, .smf, .smil, .sms, .snagitstamps,
.snagstyles, .snd, .sng, .snp, .so, .sob, .spa, .sparsebundle, .spb, .spe, .sph, .spj, .spp,
.spq, .spr, .sqb, .sql, .sqlite, .sqlite3, .sqlitedb, .sqx, .sr2, .src, .srf, .srm, .srt, .srw, .ssa,
.ssfn, .ssh, .ssk, .st, .st4, .st5, .st6, .st7, .st8, .stc, .std, .stdf, .ste, .sti, .stl, .stm, .stn,
.stp, .str, .strings, .stt, .stw, .stx, .sty, .sub, .sud, .sumo, .sup, .sva, .svf, .svg, .svgz, .svi,
.svp, .svr, .swd, .swf, .swp, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .sys, .t2b, .tab, .tao, .tar, .tar.gz,
.tax2013, .tax2014, .tb0, .tbl, .tbn, .tbz2, .tc, .tch, .tcx, .tdf, .tdt, .te, .teacher, .temp,
.template, .tex, .texinfo, .text, .tfc, .tg, .tg4, .tga, .tgz, .theme, .themepack, .thm, .thmx,
.thp, .thumb, .tib, .tif, .tiff, .tjp, .tlb, .tlc, .tlg, .tlz, .tm, .tm2, .tmd, .tmp, .tmv,
.tmx, .tn, .tne, .toast, .tod, .torrent, .tp, .tpc, .tpi, .tpl, .tpu, .tpx, .trelby, .trm,
.troff, .trp, .ts, .tsv, .ttc, .ttf, .tu, .tur, .tvj, .txd, .txf, .txt, .u3d, .u3i, .uax,
.udb, .udf, .ufo, .ufr, .uga, .uif, .umx, .unauth, .unity, .unr, .unx, .uof, .uop, .uot,
.upd, .upg, .upoi, .url, .usa, .usr, .usx, .ut, .ut2, .ut3, .utc, .utf8, .uts, .utx,
.utxt, .uvx, .uxx, .v12, .v64, .val, .vault, .vb, .vbox, .vbproj, .vbr, .vbs, .vc,
.vcd, .vcf, .vcproj, .vct, .vda, .vdb, .vdi, .vdo, .vec, .veg, .ver, .vff, .vhd,
.vhdx, .vmdk, .vmem, .vmf, .vml, .vmsd, .vmt, .vmwarevm, .vmx, .vmxf, .vnt, .vob,
.vpd, .vpe, .vrml, .vrp, .vsd, .vsdm, .vsdx, .vsi, .vsm, .vst, .vstm, .vstx,
.vsx, .vtf, .vtx, .vue, .vw, .vxd, .w3g, .w3x, .wab, .wad, .wallet, .war, .wav,
.wave, .waw, .wb1, .wb2, .wba, .wbc, .wbcat, .wbd, .wbk, .wbm, .wbmp, .wbz,
.wcf, .wdb, .wdgt, .wdp, .webarchive, .webdoc, .webm, .webp, .wgz, .wif,
.wire, .wks, .wll, .wlmp, .wm, .wma, .wmd, .wmdb, .wmf, .wmmp, .wmv, .wmx,
.wn, .woff, .wotreplay, .wow, .wowpreplay, .wp, .wp4, .wp5, .wp6, .wp7,
.wpa, .wpb, .wpd, .wpe, .wpg, .wpk, .wpl, .wps, .wpt, .wpw, .wri, .wsc,
.wsd, .wsh, .wtd, .wtf, .wtx, .wvl, .wvx, .x, .x_t, .x11, .x3d, .x3f,
.xap, .xar, .xbdoc, .xbplate, .xdb, .xdl, .xhtml, .xis, .xl, .xla, .xlam,
.xlb, .xlc, .xld, .xlf, .xlgc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsm,
.xlsx, .xlt, .xltm, .xltx, .xlv, .xlw, .xlwx, .xmi, .xmind, .xml, .xmmap,
.xpi, .xpm, .xpp, .xps, .xpt, .xsd, .xsl, .xslt, .xsn,.xvid, .xwd, .xwp,
.xy3, .xyp, .xyw, .xz, .y .yab, .yal, .ybk, .ycbcra, .yml, .yps, .ysp,
.yuv, .z01, .z02, .z03, .z04, .z05, .z3d, .zabw, .zap, .zdb, .zdc, .zif, .zip, .zipx, .zoo, .zw
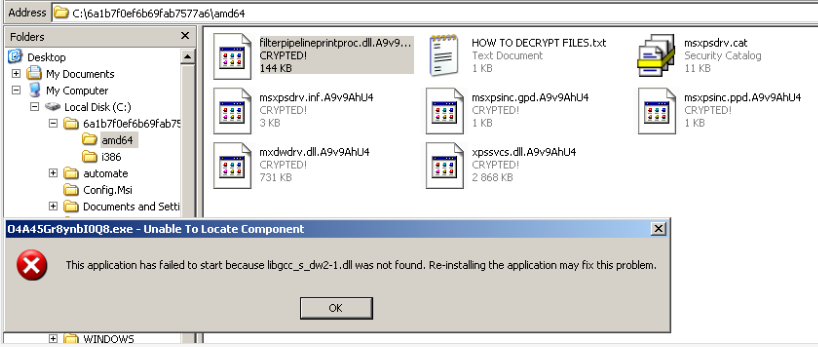
After the infection is complete the virus engages its encryption engine. The current iteration uses XOR which is one of the most popular ciphers. Decrpyiton is done by reapplying the custom XOR function with the necessary key to remove to restore the data. Computer programmers can easily implement such cryptography functions by using popular programming languages. A randomly named extension is chosen by the virus’s core engine which is then applied to the affected file types.
The virus may also institute additional damage by enforcing the following:
- Screenlocker Function – The virus may lock the computer and prevent any user interaction by imposing a screenlocker.
- Additional Malware Infection – Such ransomware can be used to install additional malware such as banking Trojans.
- Privacy Abuse – More complex strains of the ransomware can harvest account credentials, monitor the user’s actions and spy on them.
An interesting thing about this particular strain is that there are several users and groups that post on popular Russian internet forums about the virus. They post messages that translate as:
Уплата выкупа бесполезна! Файлы намеренно повреждены!
Payment of the redemption is useless! Files deliberately damaged.
The goal of these actions is to discedit the work of the anti-malware vendors and security experts in helping the victims.
After the encryption process is complete a ransomware note is crafted by the virus. A sample is written in the Russian language and a machine-translated version reads the following:
What happened to your files?
All of your files were protected by a strong encryption.
There is no way to decrypt your files without the key.
If your files not important for you just reinstall your system.
If your files is important just email us to discuss the price and how to decrypt your files.
You can email us to [email protected]
An important fact is that due to the wide range of affected file types, it is very likely that the Microsoft Windows operating will not be able to boot. This means that without the use of a quality anti-malware tool it will be very difficult to restore the affected files and protect against the threat.
AvastVirusinfo Ransomware Distribution
The first iterations of Xorist were identified in the beginning of January 2015. From there on customized strains such as AvastVirusinfo Ransomware started to appear as the hackers used the main code to create their own versions. The usual infection methods are suspected:
- Infected Installers – Software installers found on various pirate or untrusted download sites and P2P networks such as BitTorrent often contain dangerous viruses. They are bundled with the malware code as part of the primary installation file.
- Download Sites – Pirate and untrusted download sites can deliver the virus directly as an executable file, often masquerading as popular patches, updates or installation files.
- Malicious Redirects – Dangerous redirects such as ad networks and browser hijackers can lead to a viral infections. They use scripts and custom code to redirect the victim into visiting and downloading files from hacker-controlled servers.
- Email Spam Campaigns – Hackers employ the use of social engineering techniques to help increase the infection rate. Phishing scams can come in multiple variants, often the criminals pose as legitimate institutions or financial establishments which attempt to deliver an important documen to the target user.
Summary of the AvastVirusinfo Ransomware
| Name | AvastVirusinfo Ransomware |
| File Extensions | Random Extensions |
| Ransom | Varies |
| Easy Solution | You can skip all steps and remove AvastVirusinfo Ransomware ransomware with the help of an anti-malware tool. |
| Manual Solution | AvastVirusinfo Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution | Spam Email Campaigns, malicious ads & etc. |
AvastVirusinfo Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely AvastVirusinfo Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
2) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
- 1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



