Dangerous Android apps found on Google Play force users into awarding them five-star ratings and also infect them victims with viruses.
Android Apps Continue To Develop Counterfeit Ranking By Tricking Victims
Computer security experts have uncovered that malicious Android apps continue to be developed and distributed on the Google Play platform. The latest spree consists of several programs that appear as legitimate by providing descriptions and screenshots that make the users think that it is safe to use them. The apps use the widely used nag screen which has become popular by most games and applications which pop up a notification prompt which asks the users into ranking the opened program with a five-start rating. All of them include a dangerous module which is either a Trojan or an account harvester.
The difference between previous samples and the current iteration is that the new bunch of Android apps appears to be a “good-willed” by promising the users that it will disable the cascading ads in exchange of a high rating. This leads to several dangerous cases:
All of the malicious apps rely on the high ratings and large number of downloads in order to rank higher than legitimate apps. This ensures that the criminal operators can keep their infections ratio high.
The apps in questions feature dangerous modules – from remote control Trojans to information harvesting malware.
They pose as utilities for popular applications which makes it relatively easy to get infected with a virus.
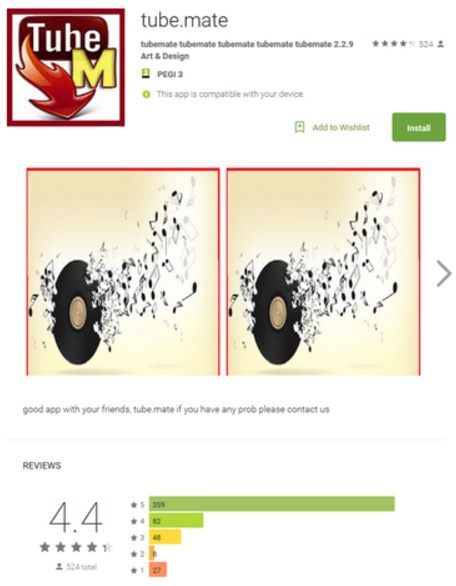
Some of the applications delivered in the campaign were detected to be samples of the Android/Hiddad family which are distributed globally. To this date most infections are detected in China, Yemen, Indonesia, Guatemala and Ukraine. According to the research several of the apps require the users to rate the games and programs first before actually allowing it to be run. After that a series of annoying ads are displayed which can lead to a serious secondary malware infection. Example includes the Subway Sonic Surf Jump game which has already been removed by Google. The hackers use name variations of popular apps like Youtube and SnapChat to create such counterfeit programs like “YouMate”, “SnapTube” and etc. As the users normally view the ratings and screenshots, normally not everyone pays detailed attention to the description. Experienced users can spot several grammar and spelling mistakes which are a clear indication of a malicious app.
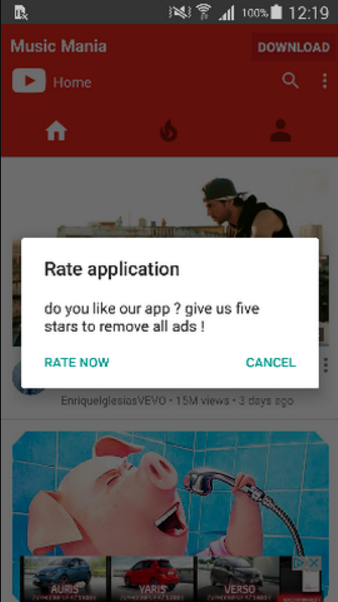
A virus sample was found in an app called “Music Mania” which creates a counterfeit system warning screen which prompts the victim into installing a “plugin android”. A screen overlay is created which prohibits further interaction until the payload is downloaded and executed on the host device. As a result of this the Trojan starts its infection. It begins to prompt the user with various dialog screens to give administrative rights to the running service. It proceeds further by presenting a screen that is riddled with ads and the victim is then asked to rate the installed service with five stars in exchange for removing all ads. If the users cancel the message then even more ads are presented to the device. Its interesting to note that even though such practices are prohibited by the Google Play Developer Policy, they have still made available to the general public.
The security experts note that merely uninstalling the dangerous apps from the device isn’t enough to remote the infection. The users need to disable the given administrator rights and then remove all traces from the relevant payload.
Note: Even though the current iteration of the dangerous apps have been removed, the users can still come in contact with the dangerous viruses. Many of them are actively being distributed on various unofficial download sites and BitTorrent trackers where freeware and pirate content is available. This is one of the reasons why sideloading (installing apps from sources other than Google Play) are discouraged for security reasons. The attack wave has been labeled has been rated as of medium threat. The researchers also indicate that such infections can also be used to give way into infecting the compromised hosts with even more dangerous threats – botnets, remote access Trojans and advanced banking Trojans.



