Alma Locker ransomware virus has just been spotted. It uses an AES-128 encryption algorithm to lock the files. Victims of the ransomware are demanded to pay a ransom of 1 bitcoin within five days.
More About Alma Locker Ransomware
Once Alma Locker is launched on the computer it generates 5 characters long extension that consists of random symbols. The same extension is later appended to the encrypted files. Additionally, it obtains the serial number of the C:\ drive and the MAC address of the first network interface and generates a unique 8 character victim ID.
Alma Locker, ransomware virus is one of the few reported to have working TOR command & control server. Thus the following information will be sent to its C&C server:
Then Alma Locker scans the drives of the victim’s PC and encrypts files with certain extensions. The files are encrypted with an AES-128 cipher. The encryption process ends with appending the 5 character extension generated at the previous stage of infection to the encrypted files. For example, the file offering.doc will be transformed into offering.doc.bt5kn once it’s encrypted.
Here is the list of file extensions targeted by Alma Locker ransomware:
The files in folders that contain the following strings may remain unaffected.
- System volume information
- Program files
- Program data
- Windows
- Microsoft
- Internet Explorer
- Mozilla
- Chrome
- App data
- Local settings
- Recycler
- Msocache
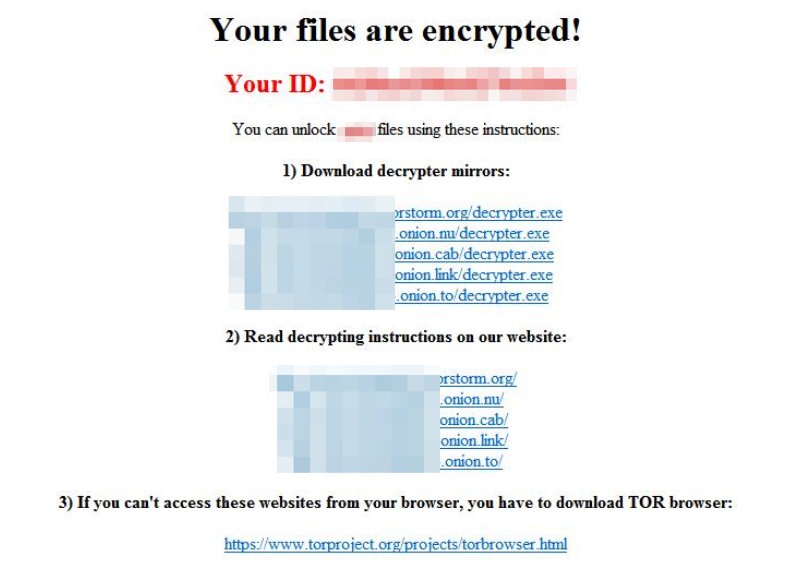
At the end of the encryption process, the victim will see a ransom note on the display. First, the ransom note states: “Your files are encrypted!”. The following information represents the victims unique ID and how to unlock the encrypted files. Two files Unlock_files_
The following image represents the ransom note of Alma Locker ransomware:
The Payment Site of Alma Locker Ransomware
At the end of the ransom note the victims see link to a TOR site and a link to download a decryptor that will decrypt some files as a proof that it is working. The ProofPoint researcher Darian Huss is the discoverer of this new ransomware. He posted the image that appears after visiting the Tor link that the ransomware provides.
And here is how it looks like:
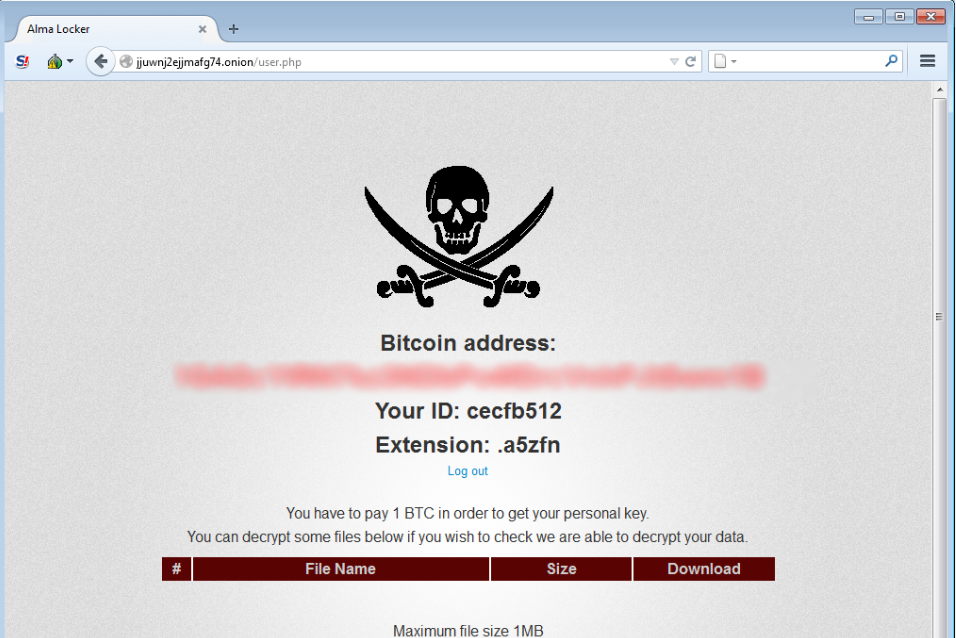
However, currently, the presented decryptor is not working.
RIG Exploit Kit Distributes Alma Locker Ransomware
Cyber criminals use RIG exploit kit to distribute Alma Locker at present. The malicious payload may be hidden in:
- The text of fake emails that pretend to be sent from trusted sources like your bank or electricity provider;
- Malicious attachment in an email;
- Fake notifications for software updates;
- Malicious links on social media sites;
- Spammed comments in websites.
In Conclusion
Currently, there are no found weaknesses in Alma Locker implementation, and there is no way to recover all encrypted files. Anyway, have in mind that the security experts are still analyzing the issue. So we advise you to instantly remove the nasty threat and keep patience until a working decrypter is available as it is likely enough to happen. As regarding the ransom, it’s for your best to not pay it. It’s better to invest the money in some alternative methods of decryption like data recovery software or reliable prevention tools against future attacks.



